The IBM MQ Appliance is a hardware offering that provides a dedicated and optimised platform for hosting IBM MQ queue managers. It includes integrated support for high availability (HA), disaster recovery (DR) and IBM MQ Advanced capabilities, such as Advanced Message Security (AMS). You can read more about the appliance at https://www.ibm.com/products/mq/appliance.
From version 9.3.3, the MQ Appliance firmware includes support for standard SSH password and certificate authentication, and it includes a file system usage monitor that provides notifications about disk consumption.
SSH authentication updates
SSH is a widely used protocol for establishing secure connections to remote servers for command line interaction. Prior to 9.3.3, the MQ Appliance firmware supports SSH, but it implements a proprietary authentication method whereby users must enter both their username and password. From 9.3.3, this method is still used by default, but you can alternatively enable standard SSH password and/or certificate authentication instead. When you enable these options, the SSH service on the appliance responds as per SSH on other systems, which helps to meet user expectations, simplify scripting, and satisfy security policies that mandate certificates.
Default authentication (no configured SSH authentication method)
The username and password are entered at the proprietary prompts.
$ ssh hostname
login: username
Password: ********
Unauthorized access prohibited.
Welcome to IBM MQ Appliance M2003A console configuration.
...
mqa#
SSH password authentication
The SSH client determines the username automatically, or it can be explicitly specified. The client prompts for the password, then the credentials are sent to the appliance for authentication.
$ ssh user@hostname
user@hostname's password: ********
Unauthorized access prohibited.
Welcome to IBM MQ Appliance M2003A console configuration.
...
mqa#
SSH CA-signed certificate authentication
The SSH client determines the username automatically, or it can be explicitly specified. The client sends a certificate to the appliance for authentication. Assuming this is successful, the user is logged in. If a valid certificate is not provided, then the connection can either be rejected, or the user can be prompted for a password instead.
$ ssh -i user-key user@hostname
Unauthorized access prohibited.
Welcome to IBM MQ Appliance M2003A console configuration.
...
mqa#
The MQ Appliance supports CA-signed SSH certificates instead of unsigned SSH keys. This means that a user can only login by using a certificate that has been signed by a trusted CA key, which enforces a centralised point of control. It also means that the appliance only needs to be configured with the CA public key instead of needing the public key for every user. Individual certificates can be revoked, as required. The certificate is only used for authentication, so the user must still be authorised to login and perform operations, as per when using a password. The SSH authentication method is configured on the appliance in a new section under RBM Settings.
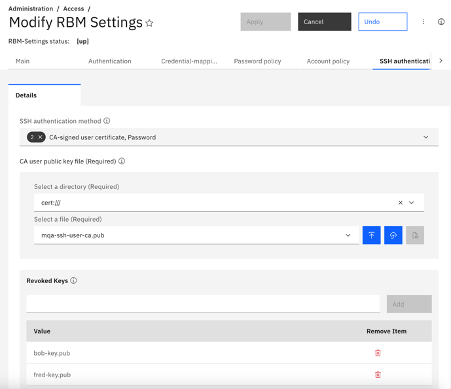
File system usage monitor
The appliance has two types of built-in storage:
- Flash storage, where the appliance firmware, the system configuration and the system logs reside.
- RAID (SSD) storage, where queue manager data, queue manager logs and other MQ configuration files reside.
These storage devices are divided in to file systems that are used for specific purposes, which also enables quotas to be enforced for different types of data. Each queue manager is allocated its own file system, and it is this file system that is replicated between appliances in a high availability (HA) or disaster recovery (DR) configuration.
It is best practice to monitor disk usage to understand trends, to aid ongoing capacity planning, and to respond to high disk usage before a file system becomes full. Prior to 9.3.3, file system usage information can be queried by using the CLI, the REST API, or other administrative interfaces. These commands and APIs enable the information to be polled, but additional orchestration is required to do this.
From 9.3.3, the MQ Appliance firmware also includes a file system usage monitor. This monitor can be scheduled to query file system usage and record this information in the log at a configurable interval. Warning and critical usage thresholds can be configured, either globally or for individual file systems, to control the severity of the notifications written to the log. The MQ Appliance firmware supports the streaming of logs to central monitoring tools, such as Splunk and Elastic Stack. By including file system usage information in these logs, it is easy to monitor file system usage over time, and receive timely notifications for file systems that are becoming full so that corrective action can be taken. In a HA or DR configuration, the monitor reports file system usage information for queue managers that have the primary role.
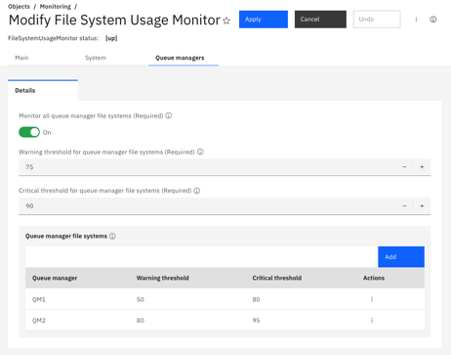
[warn] File system for queue manager 'QM1' is 55% used, 28862 MB free.
[info] File system for queue manager 'QM2' is 0% used, 64139 MB free.
Additional information
What’s new and changed for the MQ Appliance in 9.3.3
https://www.ibm.com/docs/en/mq-appliance/9.3?topic=overview-whats-new-changed-in-release-933
What’s new and changed for MQ in 9.3.3
https://www.ibm.com/docs/en/ibm-mq/9.3?topic=933-whats-new-in-mq
SSH authentication for CLI sessions
https://www.ibm.com/docs/en/mq-appliance/9.3?topic=management-ssh-authentication-cli-sessions
Disk space monitoring
https://www.ibm.com/docs/en/mq-appliance/9.3?topic=reporting-disk-space-monitoring