Hi David, Glad the suggestion helps you.
From error message in above thread(line 104), it appears that the bind credential to connect to LDAP is incorrect.
Just to isolate the issue, Assuming valid user credentials,
1. Try and access the LDAP on both secure and non-secure port using an LDAP client utility. Make sure server side setup for both secure and non-secure is good.
2. Then try and execute pdadmin user login from the WebSEAL servers runtime. If it works,
3. Try and test authentication via WebSEAL login and if it fails, there is a possibility of WebSEAL ldap entry corruption under secAuthority tree.
It is not mandatory to use secure port from verify access but ,it's always a best practice to setup LDAP/Directory server on secure port.
Regards,
Rama
------------------------------
Rama Yenumula
------------------------------
Original Message:
Sent: Tue December 13, 2022 07:11 PM
From: David Vicenteño Sanchez
Subject: Verify Access - LDAP replication
Is it mandatory to use secure port and the associated certificate database for LDAP instances? I tried but I get these errors
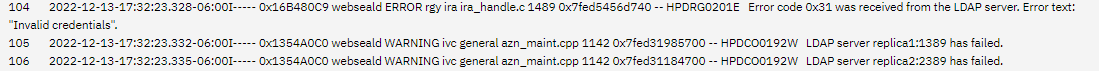
------------------------------
David Vicenteño Sanchez
Original Message:
Sent: Mon December 12, 2022 06:02 PM
From: JACK YARBOROUGH
Subject: Verify Access - LDAP replication
Hello David,
As Scott mentioned before we do have the ability to define LDAP replicas for the Reverse Proxy component.
The 'ldap.conf' has the following types of entries:
host
replica
The 'host' entry is the equivalent to 'ldaphost,port,readwrite,5' with respect to how it acts with the defined replicas.
The defined replicas take a hostname, port, mode, and priority with '10' being the highest.
If you wanted a scenario where writes only went to the primary and reads all went to other servers you could set up your ldap.conf like so:
[ldap]
...
host = primaryserver.dns.domain
port = 636
...
replica = readonlymember1.dns.domain,636,readonly,10
replica = readonlymember2.dns.domain,636,readonly,10
replica = readonlymemberN.dns.domain,636,readonly,10
replica = readonlymember9.dns.domain,636,readonly,10
This would tell the Reverse Proxy to make read requests to the pool of replicas unless they were not available at which point it would send read requests to the priority '5' server, unless that was also unreachable.
Here are the documentation references for each:
'host' : https://www.ibm.com/docs/en/sva/10.0.5?topic=ldapconf-host
'port' : https://www.ibm.com/docs/en/sva/10.0.5?topic=ldapconf-port
'replica' : https://www.ibm.com/docs/en/sva/10.0.5?topic=ldapconf-replica
These three entries used together determine how the Reverse Proxy instance communicates with the directory servers.
I believe the above information was also provided via slack as well.
------------------------------
JACK YARBOROUGH
Original Message:
Sent: Mon December 12, 2022 04:54 PM
From: David Vicenteño Sanchez
Subject: Verify Access - LDAP replication
Hi Scott, thanks for your anwser, It is clear to me that we can have multiple LDAP servers in replica and in various modes (read / write) but can it be guaranteed that the LDAP Master server only receives write requests (not read request)? This operational model for LDAP servers currently works and the client would like to maintain it.
------------------------------
David Vicenteño Sanchez
Original Message:
Sent: Mon December 12, 2022 03:10 PM
From: Scott Exton
Subject: Verify Access - LDAP replication
David,
I don't fully understand what you are asking. However, if you are asking whether ISVA can be configured to use multiple LDAP replica's for authentication the answer is yes. On top of this you also have the ability to specify which replicas are read-write and which replicas are read-only. For further information refer to the product documentation: https://www.ibm.com/docs/en/sva/10.0.5?topic=tasks-ldap-failover-configuration
Thanks.
Scott A. Exton
Senior Software Engineer
Chief Programmer - IBM Security Verify Access
IBM Master Inventor
Original Message:
Sent: 12/12/2022 11:14:00 AM
From: David Vicenteño Sanchez
Subject: Verify Access - LDAP replication
Hi Team.. A customer uses a home-made microservices layer to authenticate their applications to the IBM LDAP, all writes go to the LDAP Master, all reads go to the LDAP replicas. Customer is evaluating the possibility of replacing the microservices with Verify Access but wants to keep the scheme that write operations only go to the LDAP Master and write operations go to the LDAP replicas. Is this possible? Does Verify Access depend on something else? Some clue? Thanks in advance
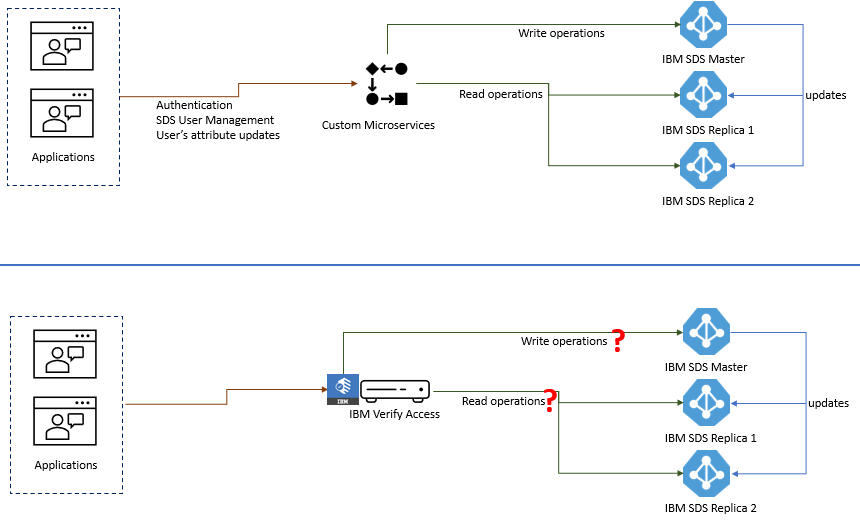
------------------------------
David Vicenteño Sanchez
------------------------------