Target audience: ODM user with ODM Administrator role
Estimated duration: 90 minutes
A downloadable version of this Blog Post is available here.
This article is part of an article series around Operational Decision Manager (ODM) on Certified Kubernetes. For more information about ODM environments and the topologies, see the ODM topologies blog post.
This document aims to describe how to make an ODM Bronze topology deployment on Certified Kubernetes.
ODM Bronze topology is an enterprise deployment of ODM in a single namespace of a cluster. It corresponds to the default production pattern deployment.
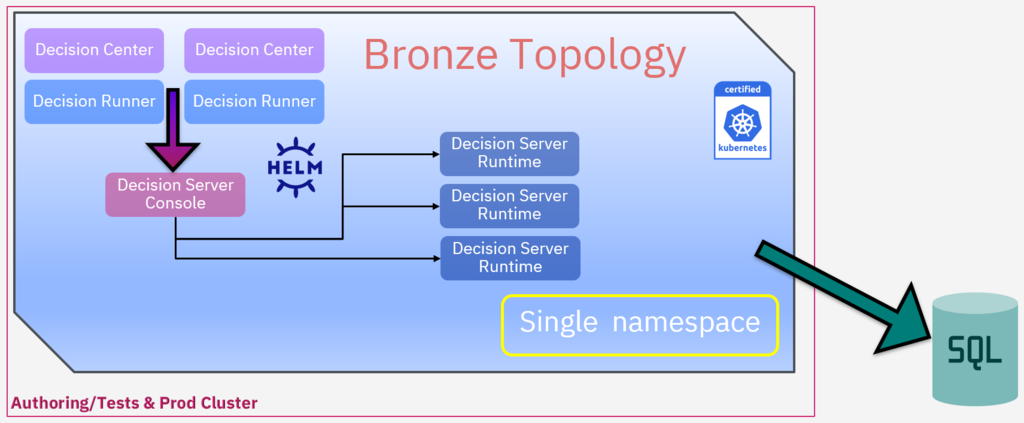
Schema of an ODM bronze topology (fig. 1)
Bronze topology is best suited for prototypes or applications with low production constraints (Small, no HA). It can also be seen as the baseline for Silver and Gold topologies and will be referenced as such in other articles.
Summary
Nota: In this configuration, you don't need storage classes as the database is externalized.
Deploying ODM production pattern comes with some choices which can lead to different installation instructions. In Customizing ODM for production, there are several production deployments guides for the Certified Kubernetes installation.
Create your Database
First you need to create your database to prepare ODM installation.
Here are some commands to help you create the database for DB2:
db2 create DB <odm DB>;
db2 connect to <odm DB>;
db2 CREATE BUFFERPOOL BP32K SIZE 2000 PAGESIZE 32K;
db2 CREATE TABLESPACE RESDWTS PAGESIZE 32K BUFFERPOOL BP32K;
db2 CREATE SYSTEM TEMPORARY TABLESPACE RESDWTMPTS PAGESIZE 32K BUFFERPOOL BP32K;
db2 CREATE SCHEMA <DB USER> AUTHORIZATION <DB USER>;
db2 connect reset;
Nota: you can complete these command with the additional command lines described in the following article: Updating DB configuration.Create a secret named secret-2301-db2.yaml for the database credentials with the following content (use your own name and use that name in your values.yaml file):
apiVersion: v1
kind: Secret
metadata:
name: odm-prod-secret-db2
type: Opaque
stringData:
db-user: "myUsername"
db-password: "myPassword!"
Then apply it to your Certified Kuberneted cluster:
kubectl apply -f "secret-2301-db2.yaml" -n ${NAMESPACE}
where ${NAMESPACE} is the targeted namespace for your Bronze installation.
If SSL is used to secure the database connection, create an additional secret (for example: db2-ssl-secret) with the SSL secret by running the following command:
oc create secret generic db2-ssl-secret --from-file=tls.crt -n ${NAMESPACE}
Whereby tls.crt is the DB2 SSL certificate in ASCII format. For example:
-----BEGIN CERTIFICATE-----
MIIHDzCCBfegAwIBAgIQCKZtYygfn9pg13D0uAX YzANBgkqhki
G9w0BAQsFADBg...zlKulqEDiV4TJ 1XpcoUq8wtmBSw1fyV7g=
-----END CERTIFICATE-----
Customize your installation
To specify configuration point, the official ODM documentation is using the "chart parameters" terms.
As an example, the documentation here mentions the following charts parameters:
However, Helm templates provide multiple ways to pass values into the chart:
- The values.yaml file in the chart
- If this is a subchart, the values.yaml file of a parent chart
- A values file if passed into helm install or helm upgrade with the -f flag (helm install -f values.yaml ./mychart)
- Individual parameters passed with --set (the chart parameters mentioned in the documentation)
As the values.yaml file is more suitable for an article and more readable for an human, we've decided to provide an example of our own properties using the values.yaml format.
license: true
usersPassword: <default admin password for ODM>
service:
enableRoute: true
externalDatabase:
type: db2
secretCredentials: odm-prod-secret-db2
databaseName: odmbronz
serverName: db2ssl.mycompany.com
sslSecretRef: db2-ssl-secret
port: '60001'
# Used for Openshift/Securised Kubernetes
customization:
runAsUser: ""
serviceAccountName: ''
Once you have customized the values.yaml file with your values, you can launch the installation of the helm chart using the following command line:
helm install ibm-odm-prod ibm-helm-repo/ibm-odm-prod -f "values.yaml" -n ${NAMESPACE}
where ${NAMESPACE} is the targeted namespace for your Bronze installation.
Configure User Access
By default, ODM is provided with a set of predefined users. To provide customized user access through an LDAP directory, some configurations need to be done. For more information, see Configuring user access.
To configure ODM with an external OpenID Connect server (OIDC provider) such as the Azure AD cloud service, you can refer to the following two articles:
Install the Licensing Service
As an IBM client, you must be sure that the License Service is up-and-running in your cluster topology.
In OCP cluster, there is a simplified manner for you to setup the service by applying the following CatalogSource:
# IBM Cloud Foundational Services 4.0
apiVersion: operators.coreos.com/v1alpha1
kind: CatalogSource
metadata:
name: opencloud-operators-v4-0
namespace: openshift-marketplace
annotations:
bedrock_catalogsource_priority: '1'
spec:
displayName: IBMCS Operators
publisher: IBM
sourceType: grpc
image: icr.io/cpopen/ibm-common-service-catalog@sha256:baec9f6a7b1710b1bba7f72ccc792c17830e563a1f85b8fb7bdb57505cde378a
updateStrategy:
registryPoll:
interval: 45m
priority: 100
Then, in the Administrator view of the OpenShift Console, open the Operators > OperatorHub and search for the IBM Licensing (provided by IBM) operator.
Select it and install it in the ibm-common-services namespace: you can create it on the fly with the installation wizard.
Once the operator is available (look at the pod name ibm-licensing-operator-xxxxxxxxxx-xxxxx in the ibm-common-services namespace), do the following steps to create an IBM Licensing instance:
- in the Administrator view, open the Operators > Installed Operators, click on the IBM Licensing instance ;
- go to the IBM License Service pannel ;
- click on the Create IBMLicensing button ;
- keep all the default parameters and check routeEnabled to create the OCP route for the service ;
- click on the Create button
Once you see the route ibm-licensing-service-instance appears, you can test it.
The token for the connection can be retrieved from the ibm-licensing-token secret.
Tune your Cluster
And especially the Networking part: haproxy, roundrobin annotation in the ibm-odm-prod-odm-ds-runtime-route route and the IngressController replicas increase.
Validate your Cluster
The default username is odmAdmin and the password is defined in your values.yaml file.
When the installation is complete, you can perform the following command lines to retrieve the routes:
echo Decision Center Business Console
DC_ROUTE=$(kubectl get routes ibm-odm-prod-odm-dc-route -o jsonpath='{.spec.host}')
echo https://"$DC_ROUTE"/decisioncenter
echo Decision Runner
DR_ROUTE=$(kubectl get routes ibm-odm-prod-odm-dr-route -o jsonpath='{.spec.host}')
echo https://"$DR_ROUTE"/DecisionRunner
echo Decision Server Console
DSC_ROUTE=$(kubectl get routes ibm-odm-prod-odm-ds-console-route -o jsonpath='{.spec.host}')
echo https://"$DSC_ROUTE"/res
echo Decision Server Runtime
DSR_ROUTE=$(kubectl get routes ibm-odm-prod-odm-ds-runtime-route -o jsonpath='{.spec.host}')
echo https://"$DSR_ROUTE"/DecisionService
#businessrules
#CloudPakforBusinessAutomation
#OperationalDecisionManager(ODM)
#RedHatOpenShift
#topology