Command & Conquer (your data access control challenges)
 AI generated image of applying controls to data in IT operations.
AI generated image of applying controls to data in IT operations.
Command & Conquer is the best PC game ever written**. If you’ve never played it, and you must, it’s a real time strategy game that was released in 1995 by Westwood Studios. You play as the UN-based “Global Defense Initiative (GDI)” or the cult-like “Brotherhood of Nod” led by the enigmatic Kane in a battle for the mysterious substance known as Tiberium. In the game, you race against your foe to construct an intricate base, carefully positioning defence systems to protect your resources including tanks, troops, buildings and “harvesters”. In the world of IT, network and application management, your data is those precious resources and protecting it is your mission.
With the latest release of IBM Cloud Pak for AIOps, v.4.7.1, we’ve introduced a major new capability# to help control the visibility of incidents, alerts, applications, inventory and topology data through a novel Role-Based Access Control(RBAC) and Attribute-Based Access Control (ABAC) solution. Read more about it in the documentation.
# I need to give a massive shout out to James, Jorge, Kilian, Roger, Scott, Steve, Stephen, Chris, Nick, Luca, Steph, Padraig, David, Ishan, Robert, Aileen, Maurice Peter, Murtuza, Andrea, Hartwin and the many others who worked on this for their endless creativity and astonishing speed and attention to detail.
** O.K., so Doom and GTA are pretty good!
Diversity is the Challenge
IT and network operations tools have conflicting requirements — on one hand, there’s pressure to be easy to use and provide rapid time to value. On the other hand, they’re tasked with solving really hard problems, the complexity of which comes from the myriad of data sources and models (inc. custom), APIs, business and workflow needs — from which two essential question arise: “who should have access to what data, and under what conditions?” and “how should the management tool provide the right capabilities and with a simple admin and test experience?”
Every organisation has different security and privacy requirements. In highly regulated environments, there may be stringent controls about who can view specific types and instances of data. For example, one of our customers has on-shore and off-shore operations teams who need different perspectives of the same data with the offshore team having a restricted view. The significant challenge for us was how to provide a suitably flexible solution that adapts to changing input data and business goals whilst providing a good administration experience that includes testing.
Profiles, restriction filters and redaction policies
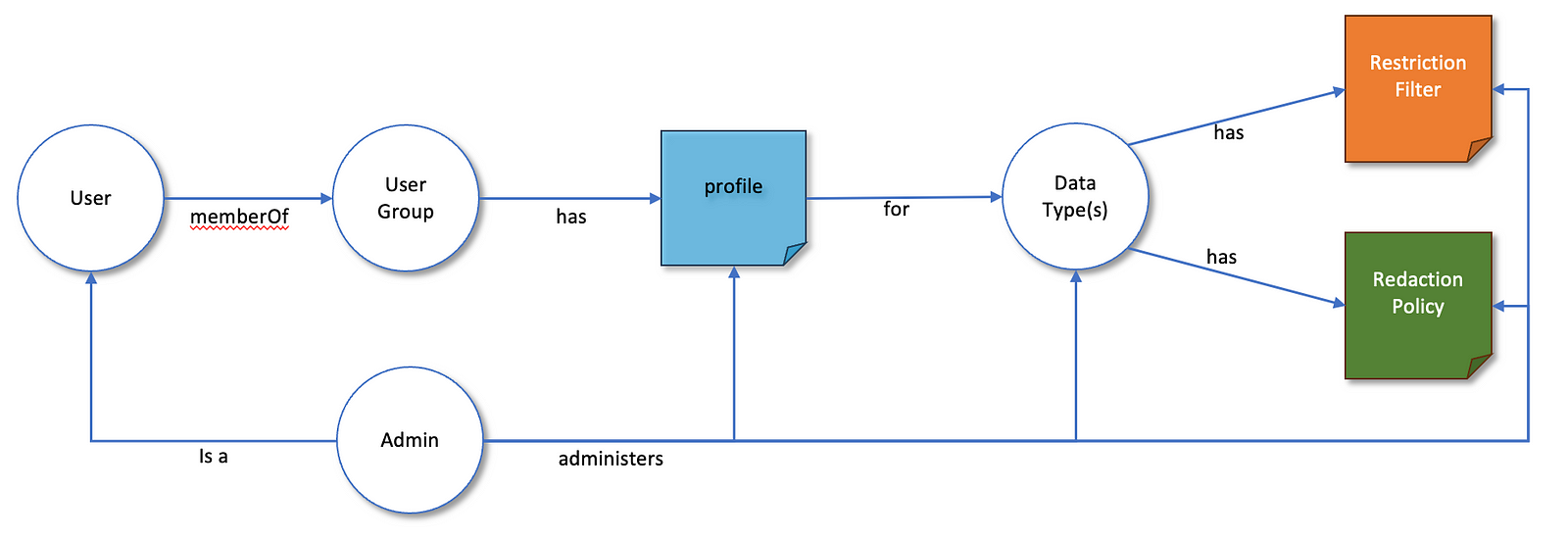
To meet these challenges, IBM Cloud Pak for AIOps breaks the problem down into the following constructs:-
- Data Types and their associated models to apply controls to. In IBM Cloud Pak for AIOps, this new capability focuses on incidents, alerts, applications/services, topology and inventory (resource) data.
- Restriction Filters control the visibility of incidents, alerts, applications/services and resource groups and resources. These are saved and allocated to a given group of users and can be thought of as the set of data they’re allowed to view. Complex criteria can be defined as part of these filters, such as only letting the offshore team see resources known to be outside of the U.K. and that have a greater than or equal to major severity problem.
- Redaction Policies provide the ability to redact data using a policy-as-code approach using a new authoring and testing capability. The policies are enforced using an integrated Open Policy Agent engine integrated into our APIs and are written in the Rego policy language. The reason for using a policy-as-code approach is due to the diversity of customer requirements and data and Rego provides a powerful platform on which to express the desired business logic. For example, a Rego policy can be used to mask IP address and contact details from devices while also redacting device names to hide sensitive information that may reveal location and role. OPA also provides good testing capabilities that we’ve integrated into IBM Cloud Pak for AIOps to help with policy authoring. Redaction policies are optional for incident, alert and resource data but less so for topology as restriction filters do not apply.
- Profiles serve as the means to unify restriction and redaction policies for various data types and to assign them to groups — providing a means to express RBAC and ABAC controls. RBAC in this context considers groups to be proxies for roles, such as the offshore team that has restriction filters and redaction policies assigned to their alert data. ABAC reflects the need to provide a more dynamic and flexible approach. Instead of solely relying on roles (groups), visibility is based on attributes, such as IP subnet, tags, contact information and so on. As a result, it’s inherently able to adapt to changes in the environment and the onboarding of new infrastructure and applications. A ‘base profile’ simplifies administration by setting the criteria that generally applies, and on-top of which more specific policies are defined. For instance, best practice would be to be as strict and redactive as possible with additional profiles granting more visibility as needed.
The model between these constructs is as follows:-
Here’s some screenshots of the new capability in action.
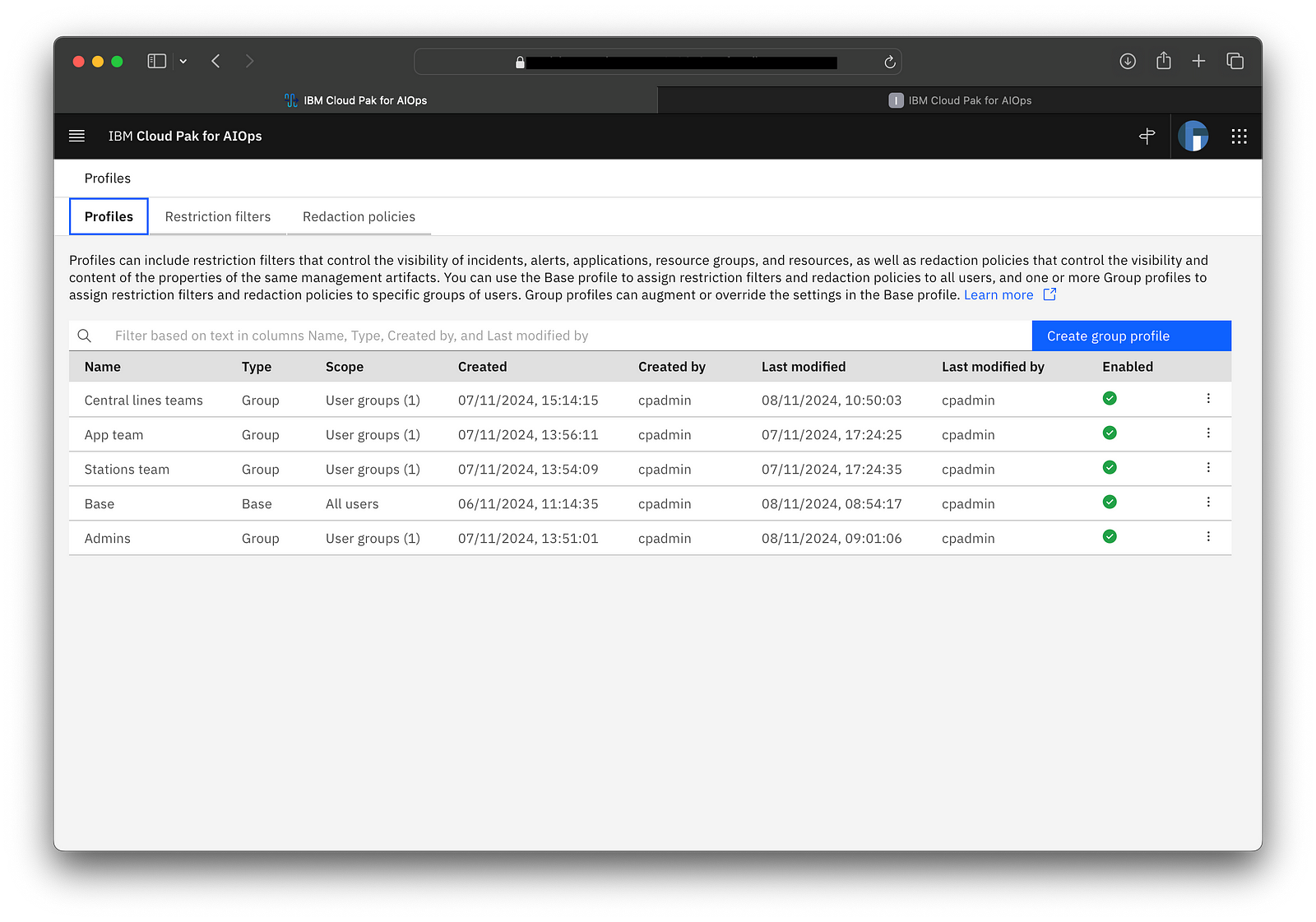 1. Administrators manage multiple profiles that unify the filters and redaction policies that apply to user groups and a set of data types. Each data type can specify a restriction file and/or redaction policy to apply.
1. Administrators manage multiple profiles that unify the filters and redaction policies that apply to user groups and a set of data types. Each data type can specify a restriction file and/or redaction policy to apply.
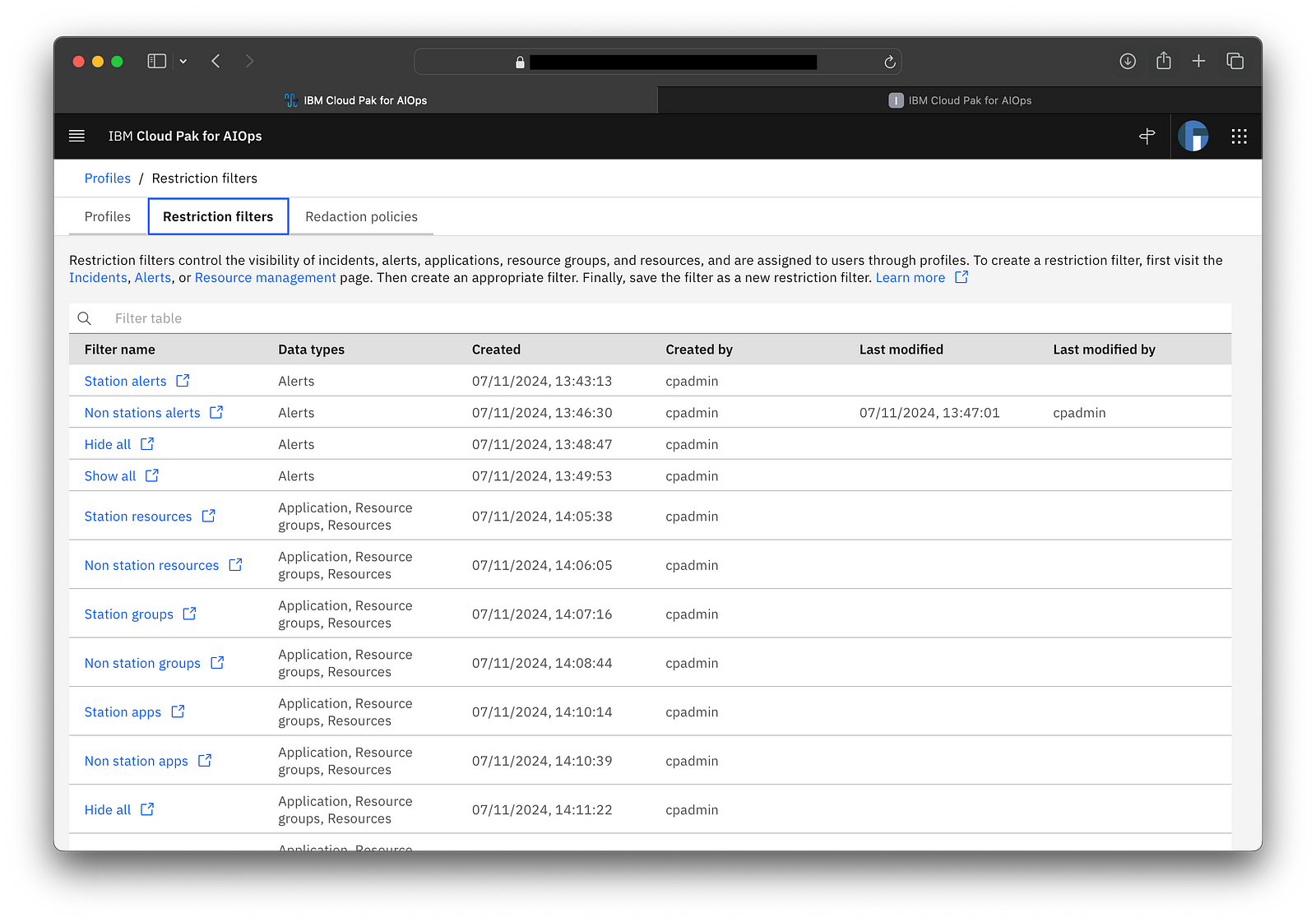 2. Restriction filters serve as a means of filtering data and they’re expressed using the standard filtering mechanisms in the GUI.
2. Restriction filters serve as a means of filtering data and they’re expressed using the standard filtering mechanisms in the GUI.
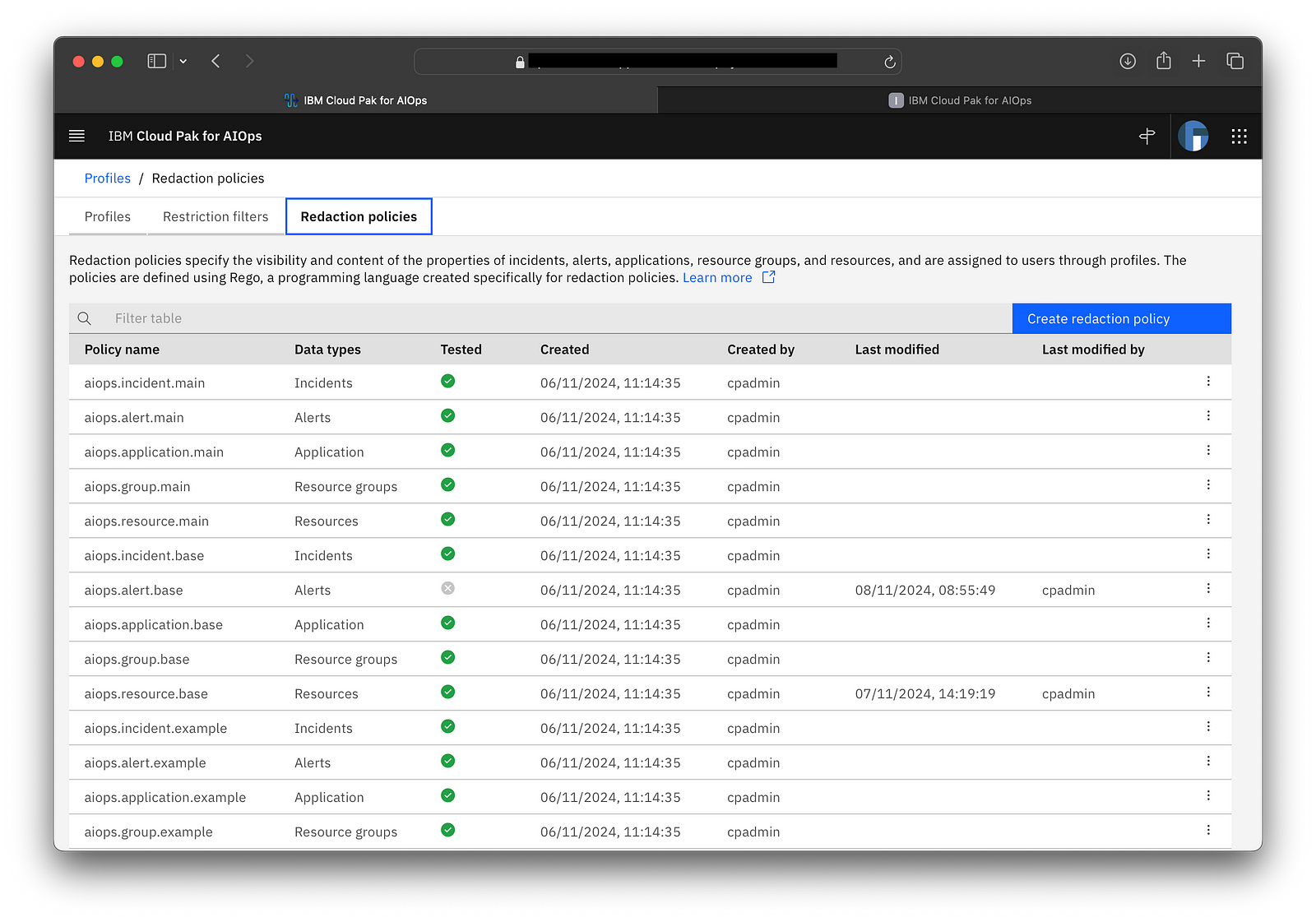 3. Redaction policies provide the ability to manipulate data by policy using OPA’s Rego language. This provides great flexibility as, for example, users can use regular expressions to help determine which properties should be displayed and how. The admin UI also provides good visibility of whether policies have been tested.
3. Redaction policies provide the ability to manipulate data by policy using OPA’s Rego language. This provides great flexibility as, for example, users can use regular expressions to help determine which properties should be displayed and how. The admin UI also provides good visibility of whether policies have been tested.
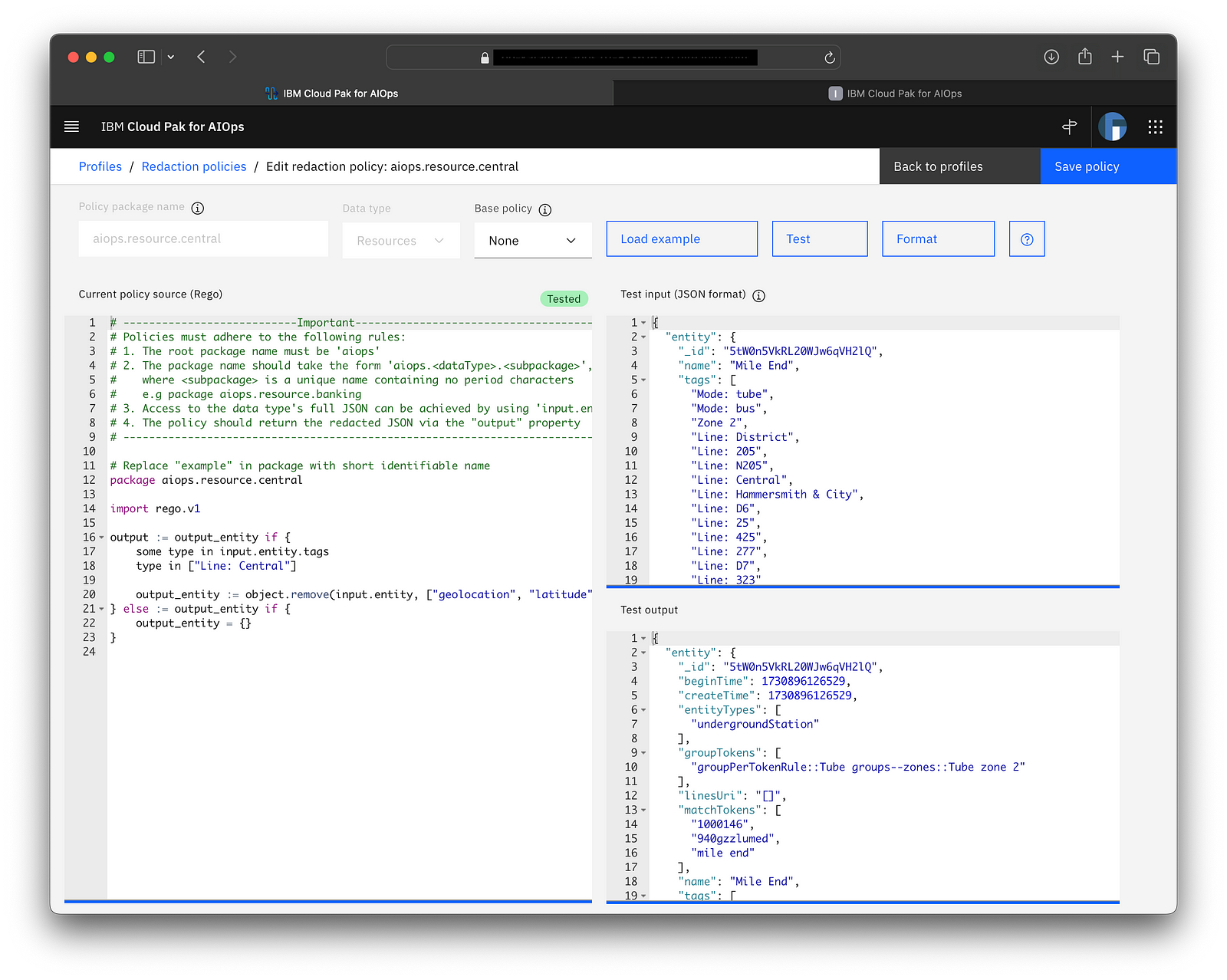 4. Authoring a redacton policy in Rego and note the ability to load sample data and test it. When tested, that gets stored along with the data used to test the policy.
4. Authoring a redacton policy in Rego and note the ability to load sample data and test it. When tested, that gets stored along with the data used to test the policy.
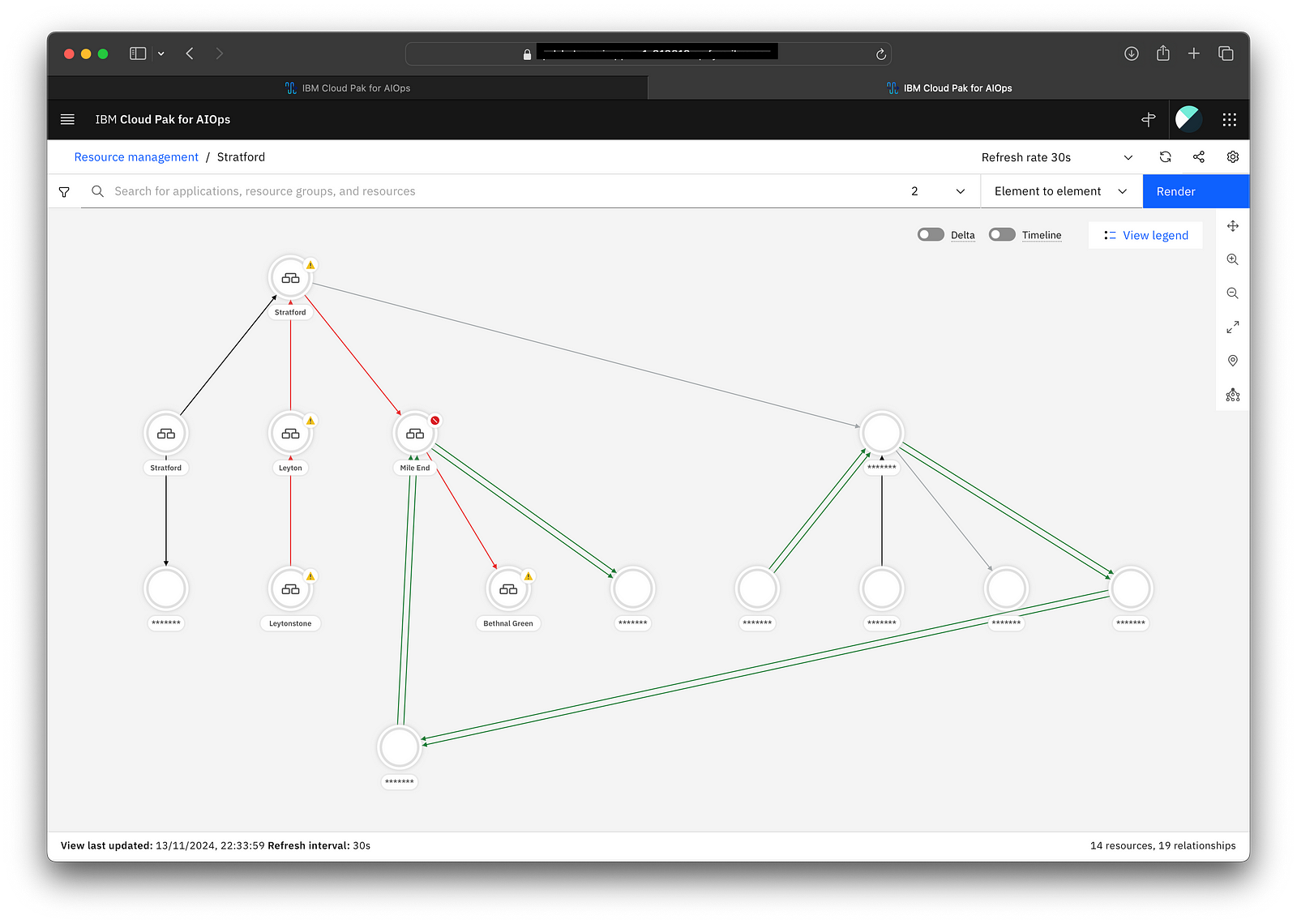 5. An example of redacted topology where the user can see central line stations but no details of stations on other lines related to those, note the resource name is hidden.
5. An example of redacted topology where the user can see central line stations but no details of stations on other lines related to those, note the resource name is hidden.
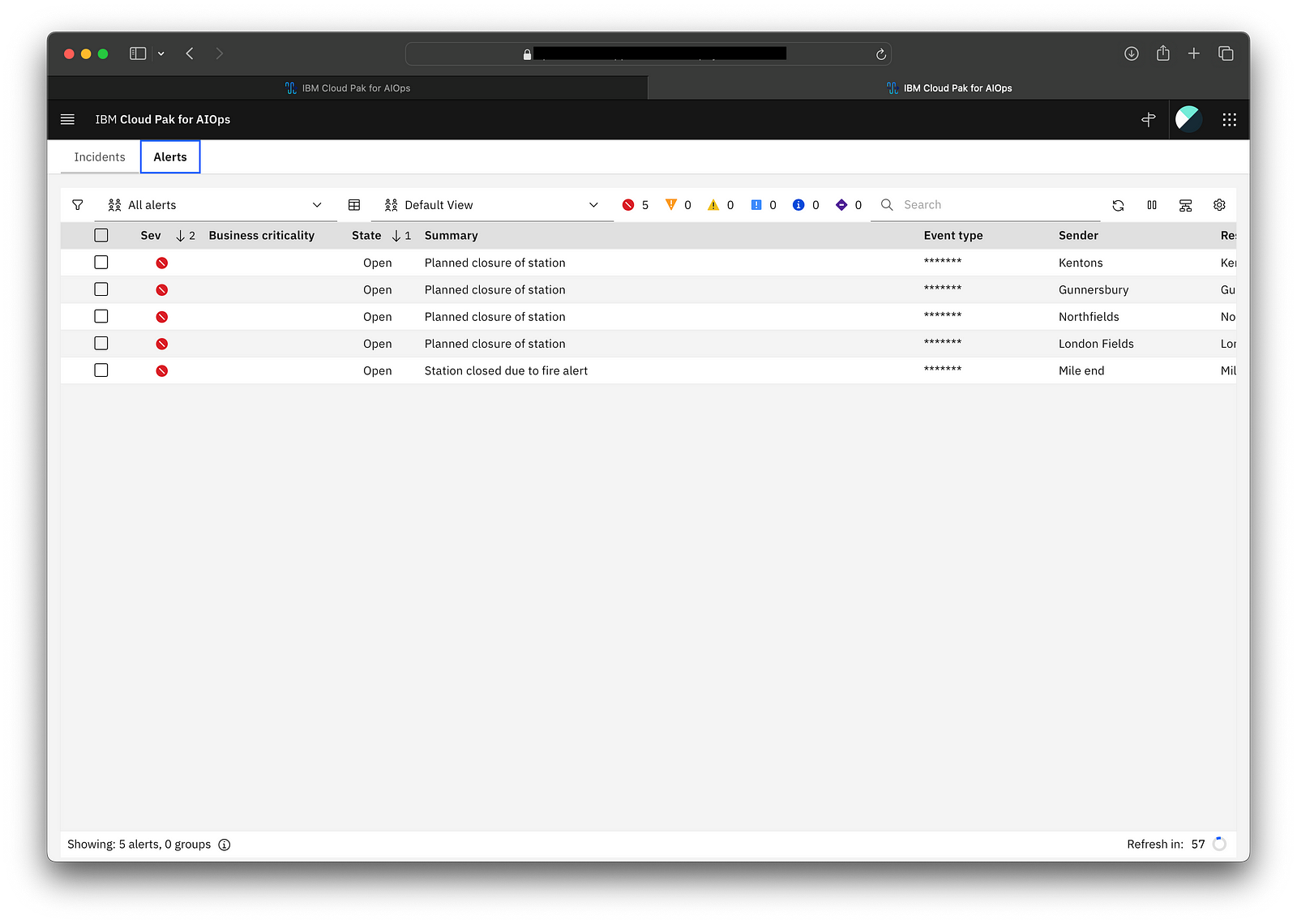 6. An example of alerts subject to policy controls with redacted fields.
6. An example of alerts subject to policy controls with redacted fields.
The Value of Flexible Access Control
Why is this level of flexibility and control so valuable? Here’s a few reasons:-
- Enhanced Security: By ensuring that sensitive data is only accessible to the appropriate individuals, organisations can ensure that they reduce the risk of their teams accessing data that is not appropriate to their role.
- Operational Efficiency: Users can only see what they need, minimising distractions and allowing them to better focus on their core responsibilities. This improvement in efficiency can translate to quicker decision-making and a more streamlined workflow.
- Compliance: An organisation may need to meet regulatory requirements about data access and handling. With the appropriate control mechanisms, compliance becomes easier to manage and achieve.
- Something for Every Environment: No two customer environments or business processes and needs are the same. The flexibility of profiles, restriction filters and redaction policies and the unified authoring and testing experience allows organisations to tailor their access controls to their needs, accommodating unique requirements and evolving circumstances.
Build Your Base
Just as constructing base defences in Command & Conquer protects your resources, implementing robust and flexible access control mechanisms in IT operations helps ensure your operations data is only seen by those with a need to see it. IBM Cloud Pak for AIOps, with its new profile, filter and redaction capabilities, offers a comprehensive strategy for providing teams with the data necessary to do their job through a unified administration and testing experience. I’d love to hear about your experiences and requirements when managing data access control.