I am writing this while the industry is in panic finding and patching log4j after CVE-2021-44228 ("Log4Shell") was reported.
Of course IBM and probably all other vendors inspect their products and come out with patches as fast we can. You have probably seen many security bulletins announcing patches for all types of products. There are also technotes like
Is Business Automation Workflow affected by CVE-2021-44228?IBM Business Automation Workflow has one special characteristic that makes your life as a system admin even more complex: The product's purpose is to run custom applications and no matter how fast and well it is patched, custom code can introduce all types of vulnerabilities.
There are obvious application level mistakes like incorrect authorization and less obvious issues with missing validation of user input leading to injection vulnerabilities and similar issues. In the light of recent events another aspect that needs (constant) care is the use of open source libraries.
Application developers can include open source libraries in process apps by uploading "Server Files" in Process Designer:
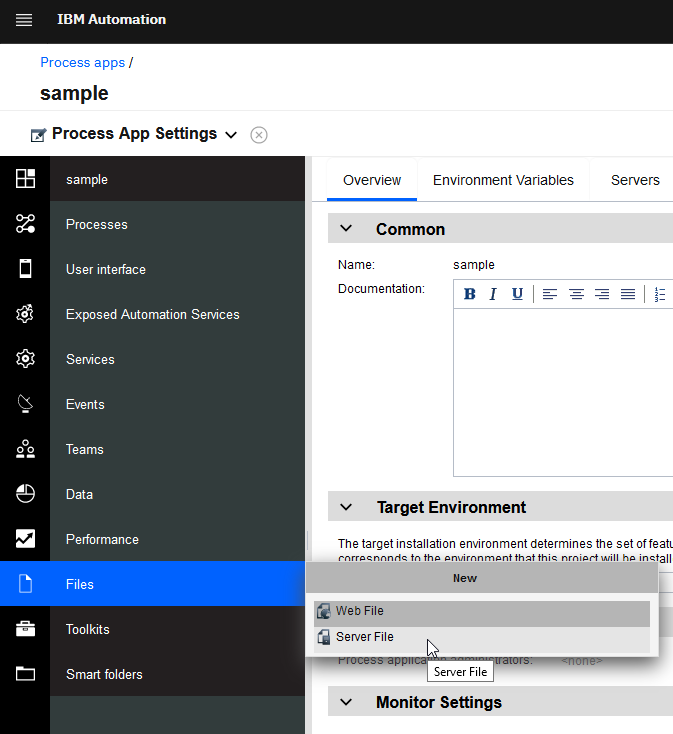
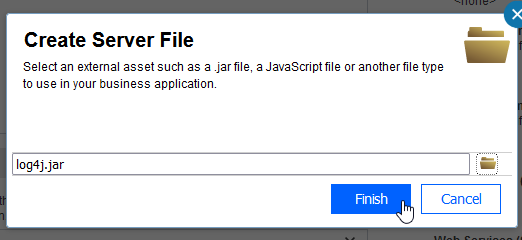
Unlike JEE apps or BPM Advanced SCA modules (for which you can see the entire app in the
installedApps of you appsever node), these files end up as "managed assets" in the product database and will not be easily detected by typical open source scans using OWASP dependency checker or AppScan on Cloud.
The following script is calling BAW REST APIs to list all managed assets in all snapshots. It works for me on bash with
cURL and
jq installed.
Other platforms need modifications of course, e.g.
cURL and Command prompt on Windows are significantly different.
user='some_admin'
pwd='********'
bawrest='https://my.server:9443/rest/bpm/wle/v1'
curl -sku $user:$pwd $bawrest/processApps | jq > projects.json
curl -sku $user:$pwd $bawrest/toolkit | jq >> projects.json
for project in $(cat projects.json | jq '.data.processAppsList[].ID' -r)
do
cat projects.json | jq --arg project $project '.data.processAppsList[] | select(.ID==$project) | "\(.name) (\(.shortName))"' -r
snapshots=$(cat projects.json | jq --arg project $project '.data.processAppsList[] | select(.ID==$project) | .installedSnapshots[].ID' -r)
for snapshot in $snapshots
do
curl -sku $user:$pwd "$bawrest/assets?processAppId=$project&snapshotId=$snapshot&filter=type%3DManagedAsset" | jq > $snapshot-assets.json
echo " > --- snapshot: $snapshot ---"
cat $snapshot-assets.json | jq '.data.ManagedAsset[] | " > \(.name)"' -r
done
done
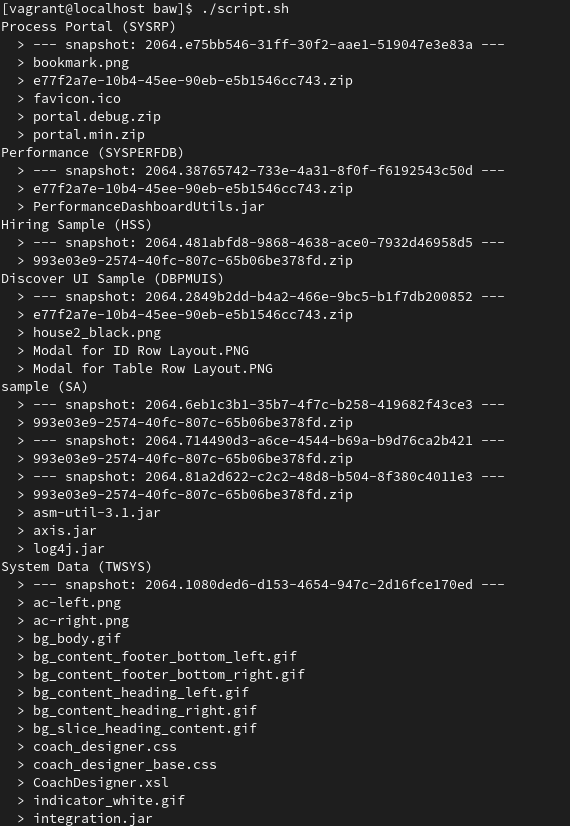
The result should look like this and my "sample" app should catch your attention.
#BPM#BusinessAutomationWorkflow(BAW)#BusinessProcessManager(BPM)#Featured-area-2#Featured-area-2-home#IBM-BPM#log4j