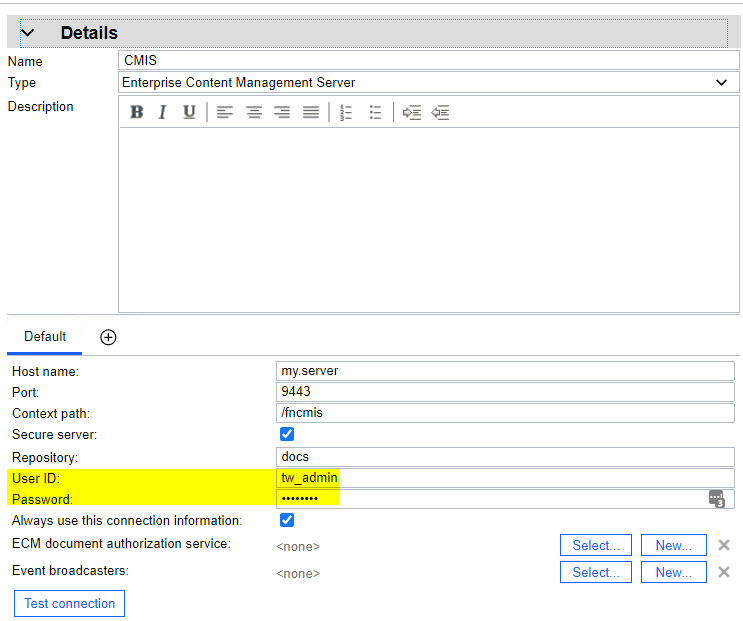
The "User ID" and "Password" specified here are persisted in the database. They can even be included when you move your app from dev through test and staging to prod:
By looking at database content, we can find that all this connection information is serialized in a URL and stored in an environment variable as follows:
Obviously, the password is encrypted, which is good.
We can create a snapshot of this process app, export it in .twx format, and import it into another instance of IBM Business Automation Workflow Center. Or we can use online or offline deploy to install the snapshot in a Workflow Server. Inspecting the export file closely, we will find the exact same URL representation of our ECM server connection information.
In each of these cases, a connection to the Enterprise Content Management System will succeed, that is, somehow the target system was able to read, decrypt, and use the encrypted password - which is convenient, but of course concerning from a security perspective.
This can only be possible when both, the source system and the target system were both using the same key. In fact, the key used in this scenario has been hard coded for many releases and is still used as the default key for backwards compatibility.
Advanced Database Persistence with Configurable Encryption
With IBM Business Automation Workflow 20.0.0.2, we can do better than that.
You can set a new key by updating the server configuration with your own keyphrase, which will be used to derive the effective key.
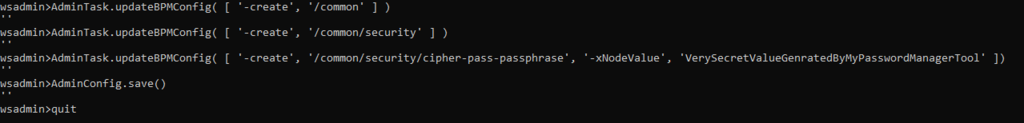
After applying this configuration, all encryption and decryption will use the configured key. Of course, this configuration does not change anything in your database or in .twx files that you may have exported in the past.
While import of .twx will still work, the encrypted credential is no longer understood. You can use Process Admin Console to set the same value again.
The same holds for existing process apps in runtime Workflow Servers. You need to set a new password for in all "affected" snapshots.
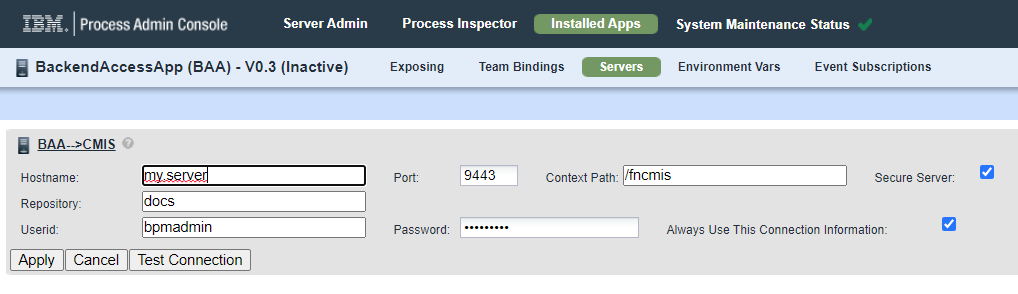
In case you actually "transport" credentials with process apps between Workflow Center environments or as part of install packages, you can set the same keyphrase in all your "related" systems to allow seamless exchange.