Integration of IBM Storage Ceph Object with Vault Server (Agent-Based authentication)
Introduction
This blog continues our previous discussion on Ceph Object Storage encryption at rest, where we introduced data encryption concepts, discussed various encryption options, and detailed the integration with IBM GKLM for IBM Storage Ceph Object (refer to the blog by Daniel Parkes).
This document, the second in our series on encryption providers, focuses on integrating HashiCorp Vault with IBM Storage Ceph Object.
Ceph Vault Integration
Integrating Vault with Ceph enhances security in object storage by managing encryption keys centrally. Ceph Object Gateway works with Vault to retrieve encryption keys when needed, supporting two types of Vault engines:
-
K/V Engine: Stores encryption keys as static data. This is ideal when the same key is required for multiple operations.
-
Transient Engine: Provides one-time keys for single-use encryption or decryption, which enhances security by minimizing the exposure of encryption keys.
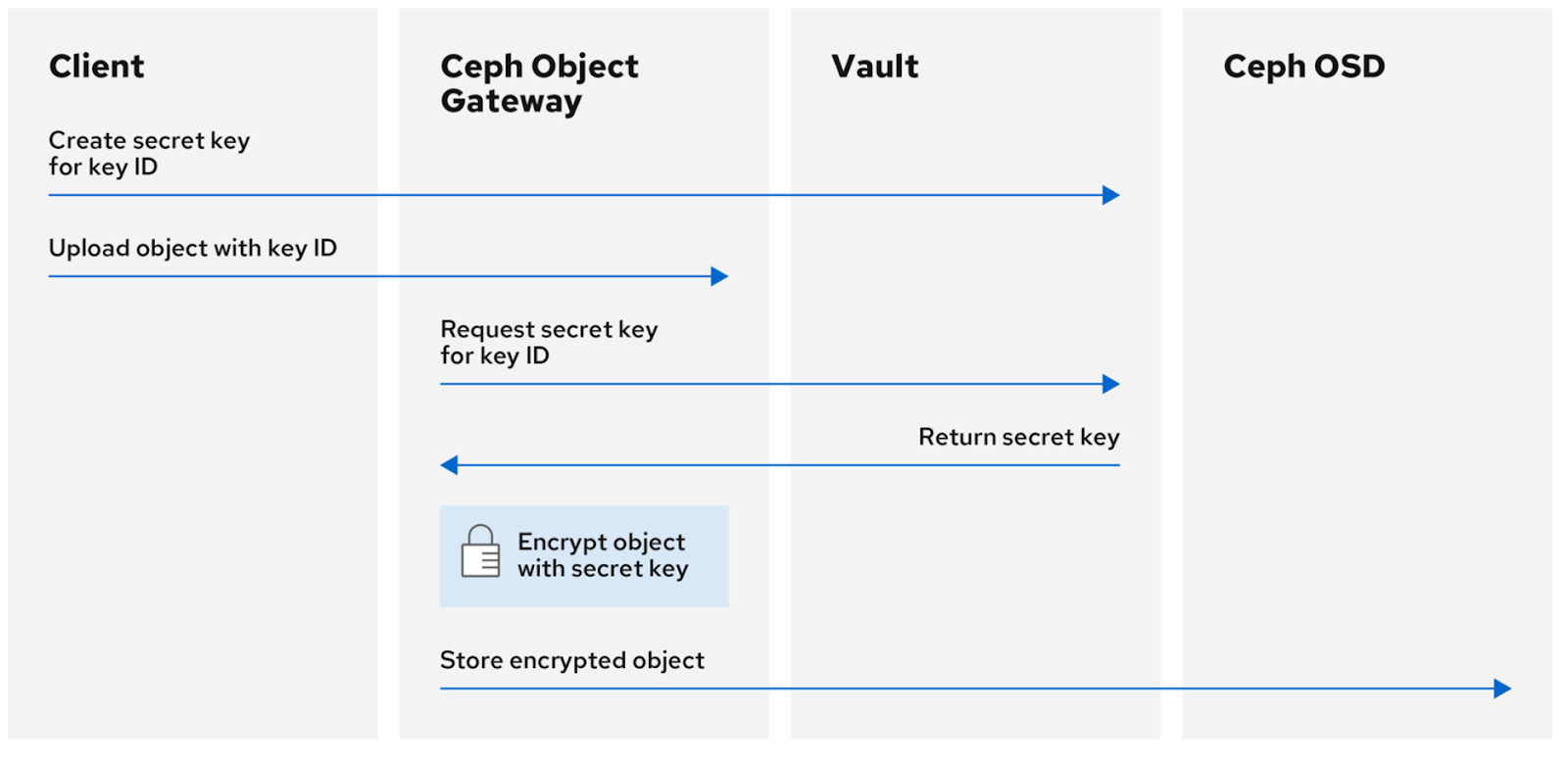
Workflow
-
Client: Creates a secret key for a key ID and uploads the object with this key ID.
-
Ceph Object Gateway: Requests the secret key from Vault.
-
Vault: Returns the key, either retrieved (K/V) or generated dynamically (Transient).
-
Encryption: Ceph Object Gateway encrypts the object with the key and stores it in Ceph OSD.
Goal
This document aims to set up a HashiCorp Vault server and a Vault Agent on RHEL-9.3 to generate and manage encryption keys using Vault's transit engine. These keys would encrypt objects stored in Ceph RGW with AES256 encryption, enhancing data security.
Method
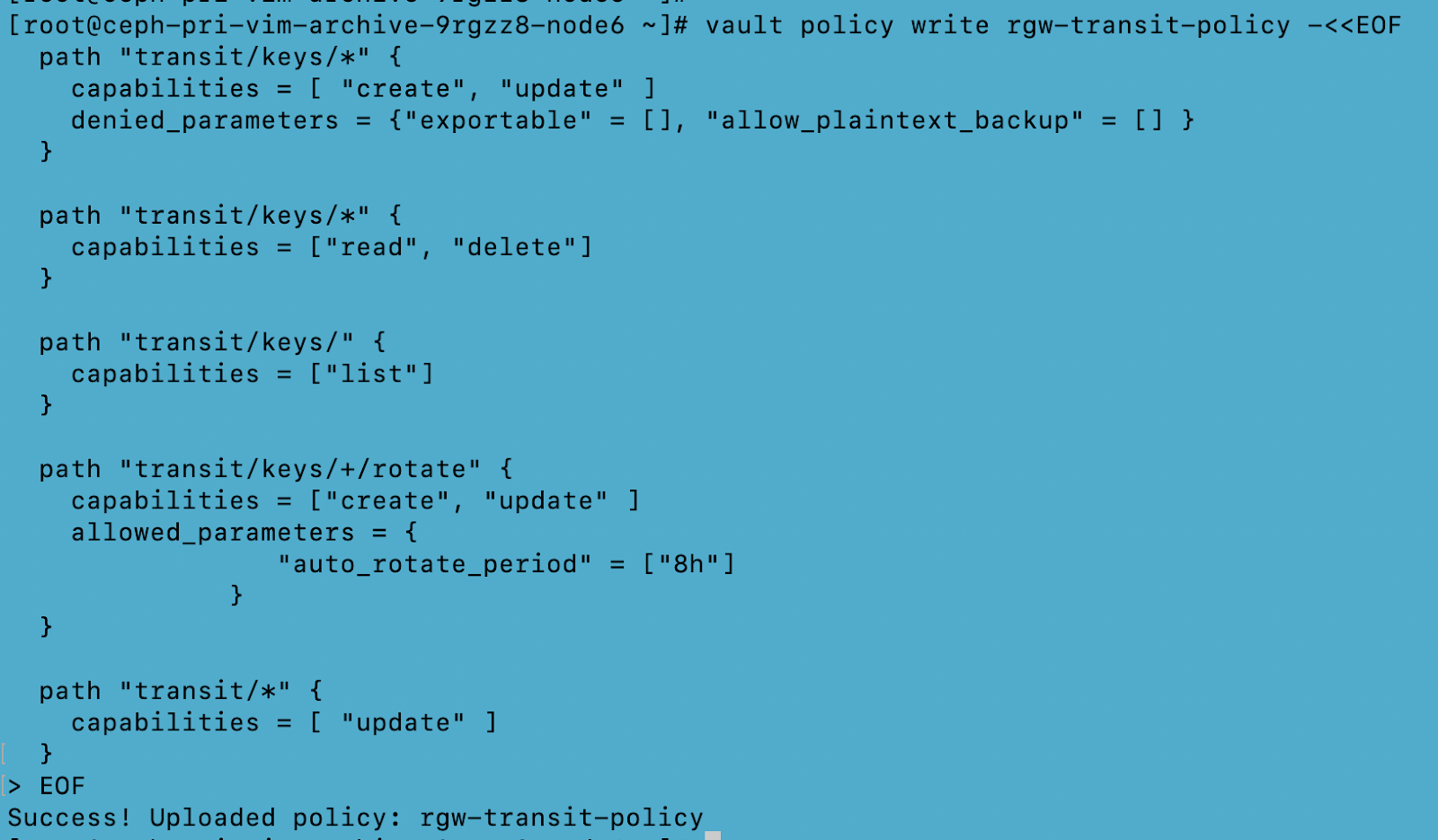
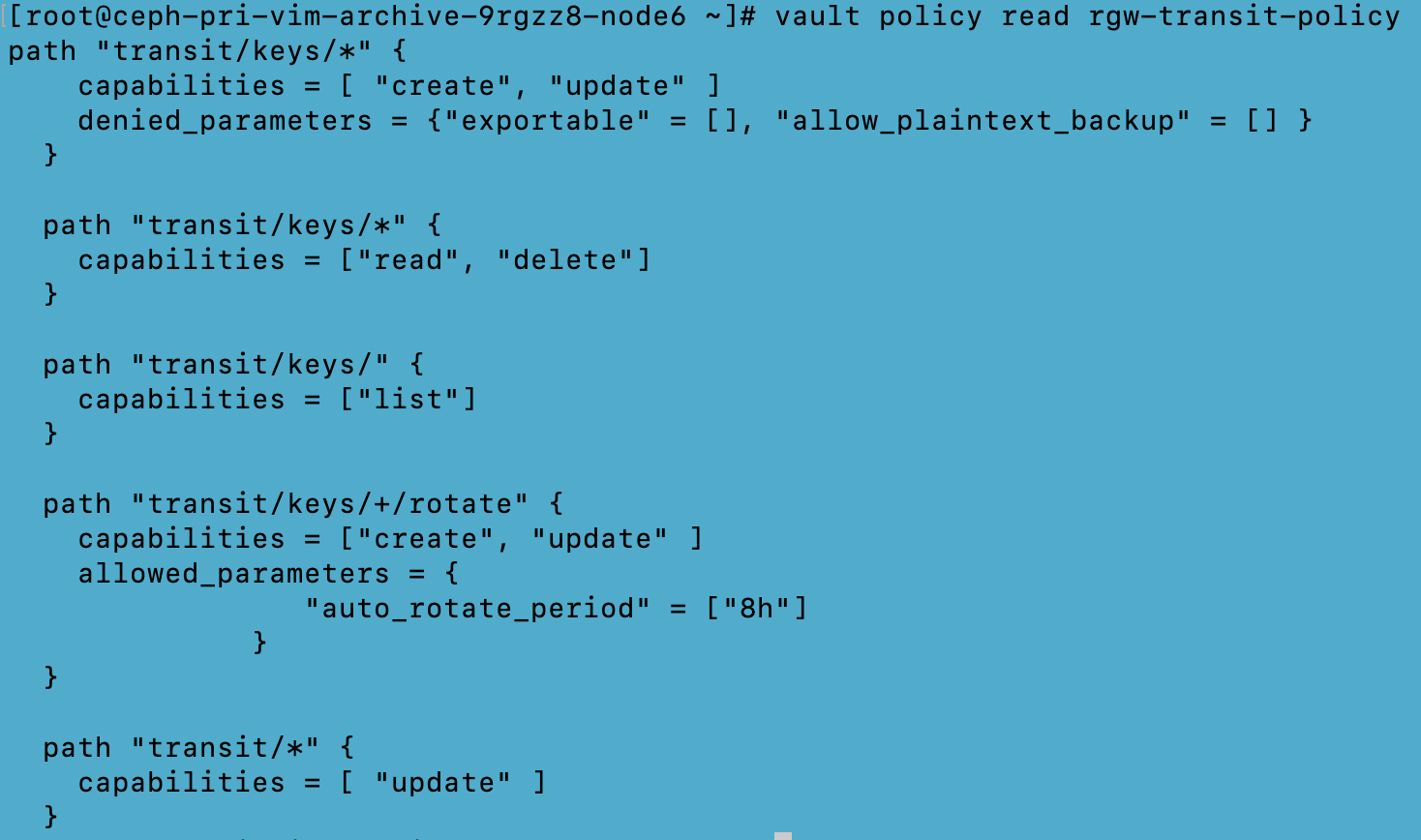
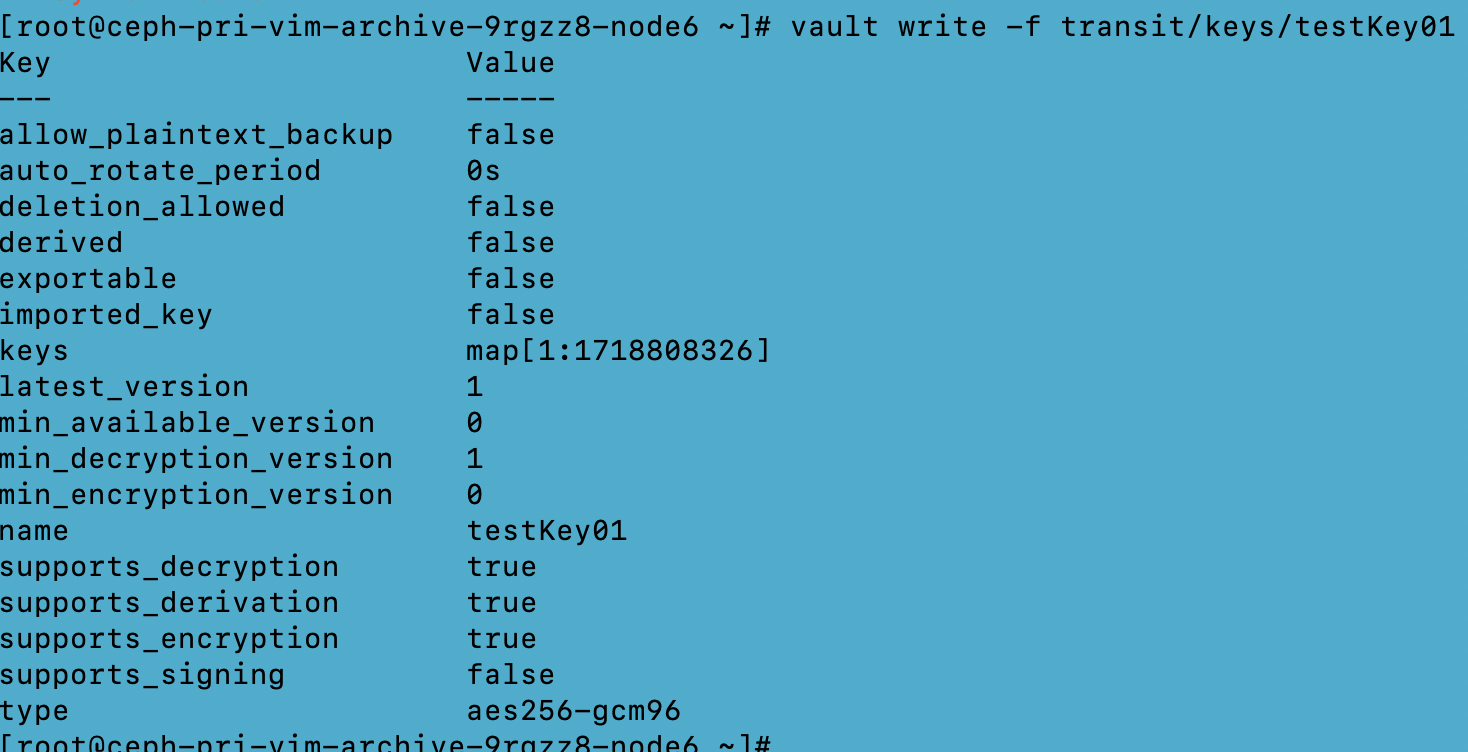
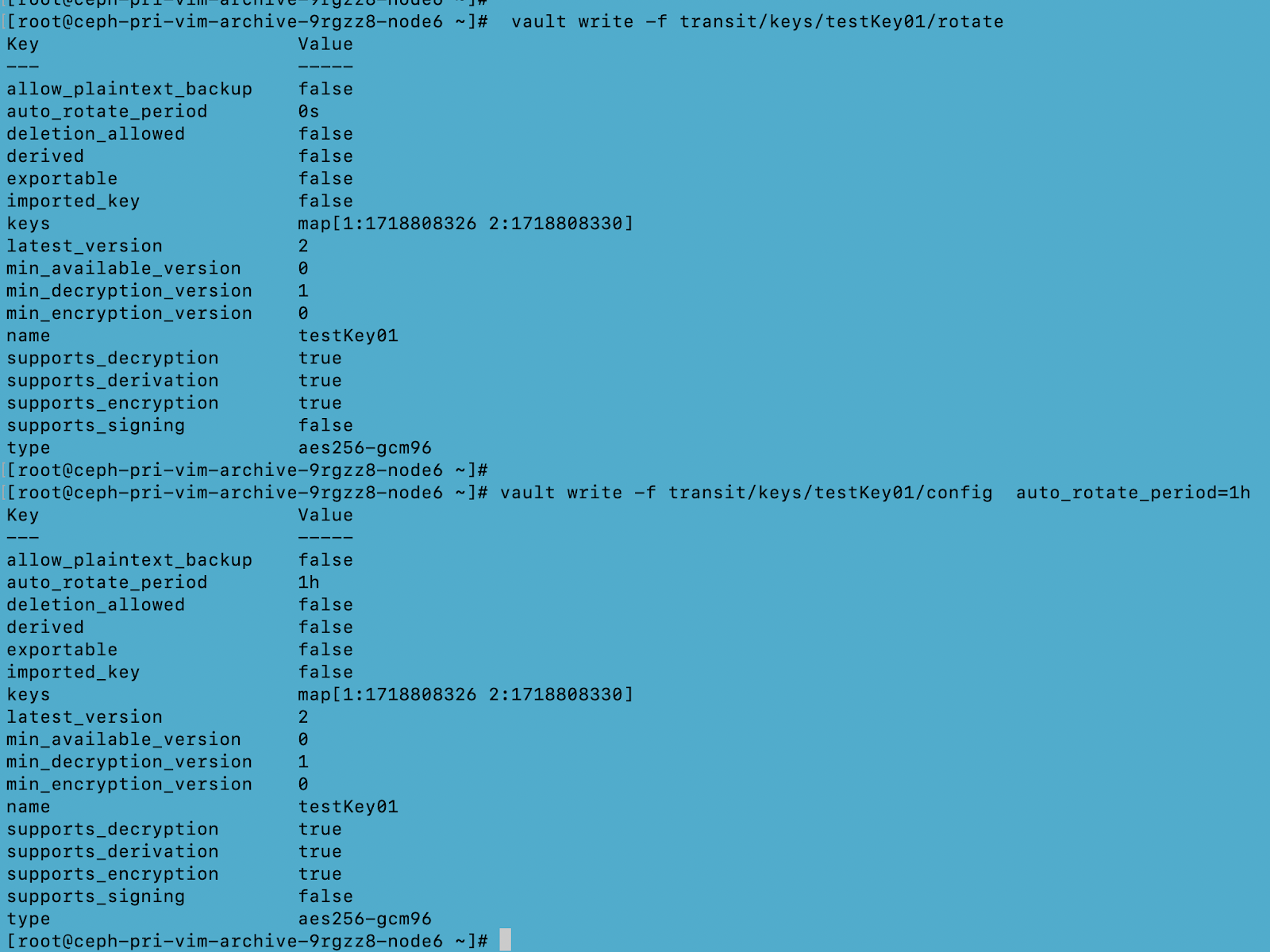
We have used “Agent” based authentication and a “Transit” secret engine for secret/encryption key generation.
Steps Overview
-
Setting Up Vault Server: Install and configure a Vault server to manage encryption keys on RHEL-9.3
-
Utilizing the Transit Engine: Configure Vault's Transit Engine for secret key generation and encryption operations.
-
Configuring Vault Agent: Deploy Vault Agent/s for authentication and automatic retrieval of secrets.
-
Integrating with Ceph RGW: Use the generated keys to encrypt objects in Ceph RGW with AES256 via either SSE-KMS or SSE-s3
Steps in detail
-
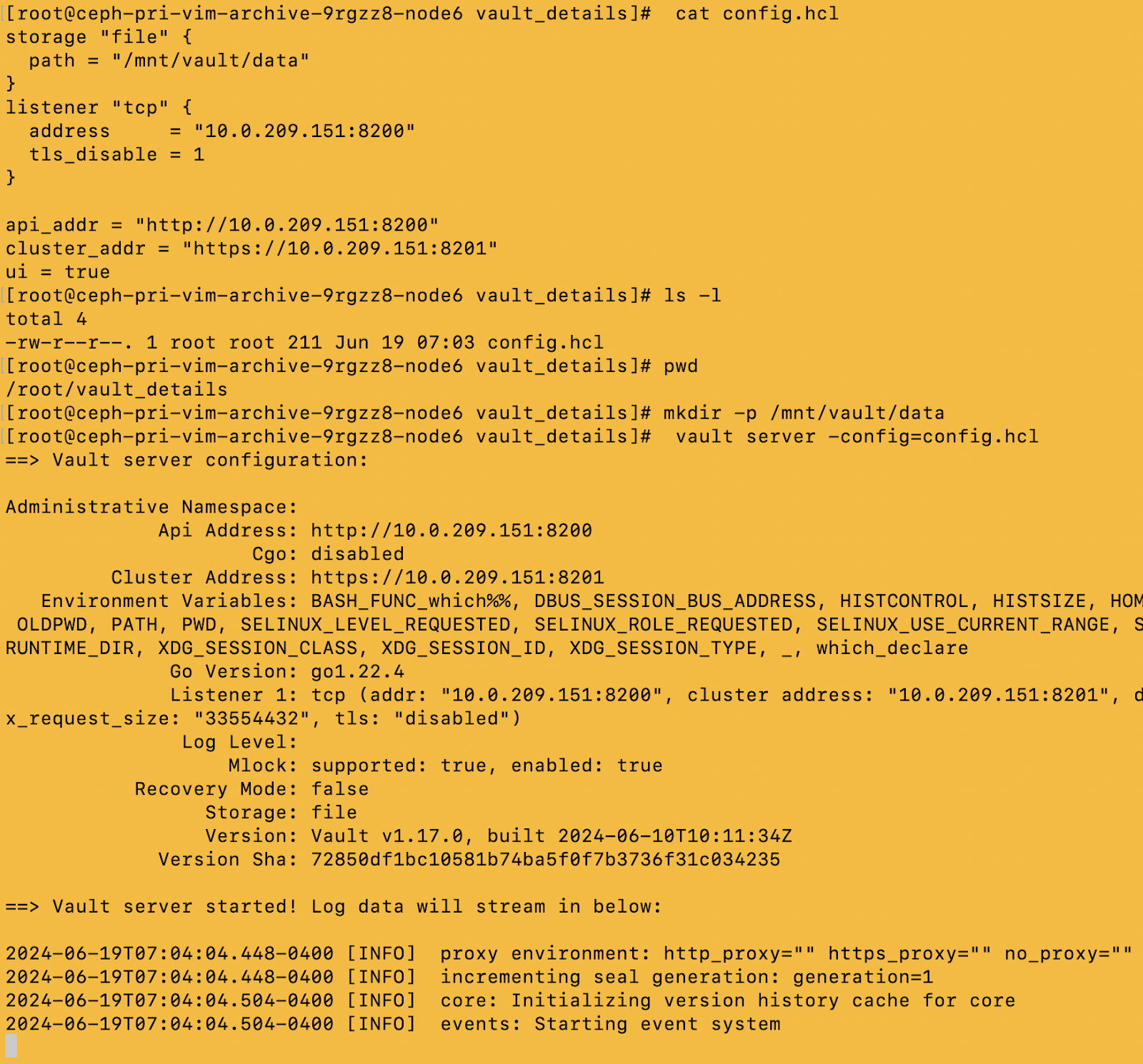
Setting Up Vault Server

-
Utilizing the Transit Engine

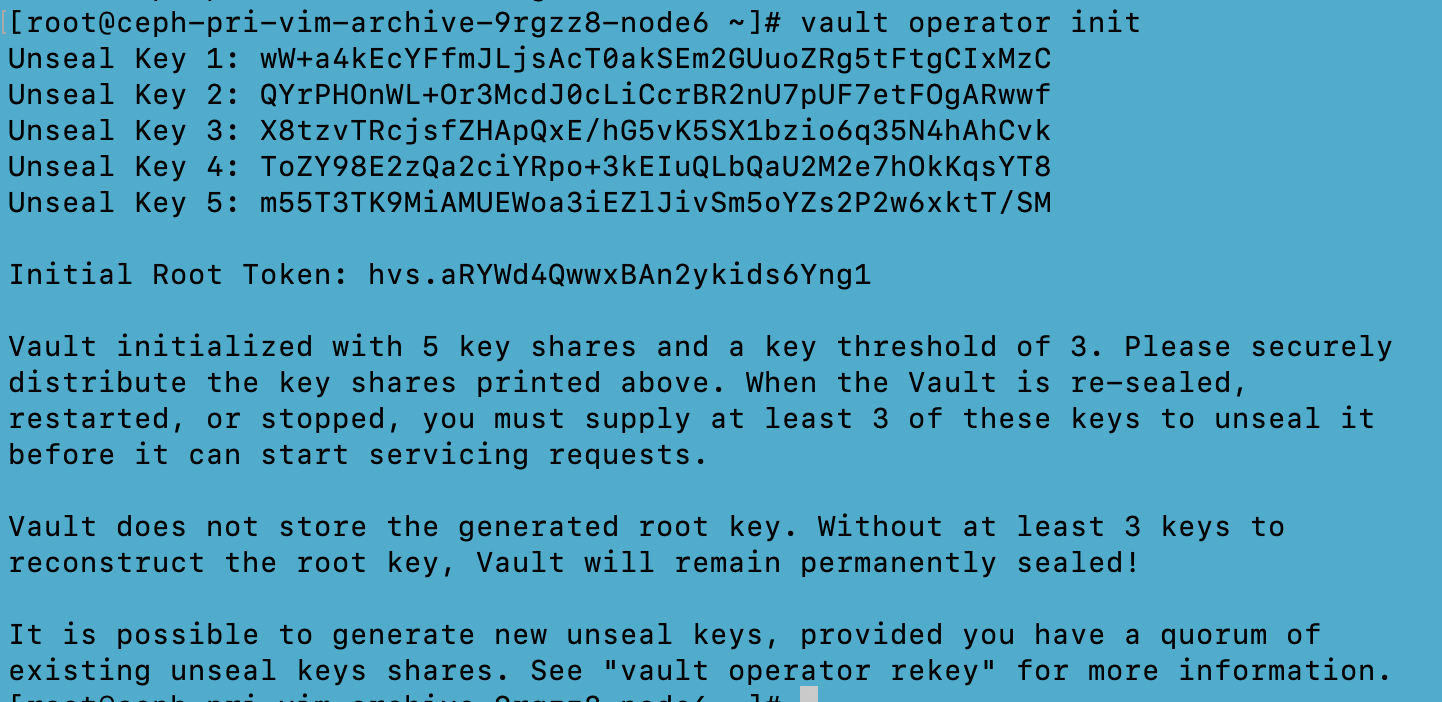
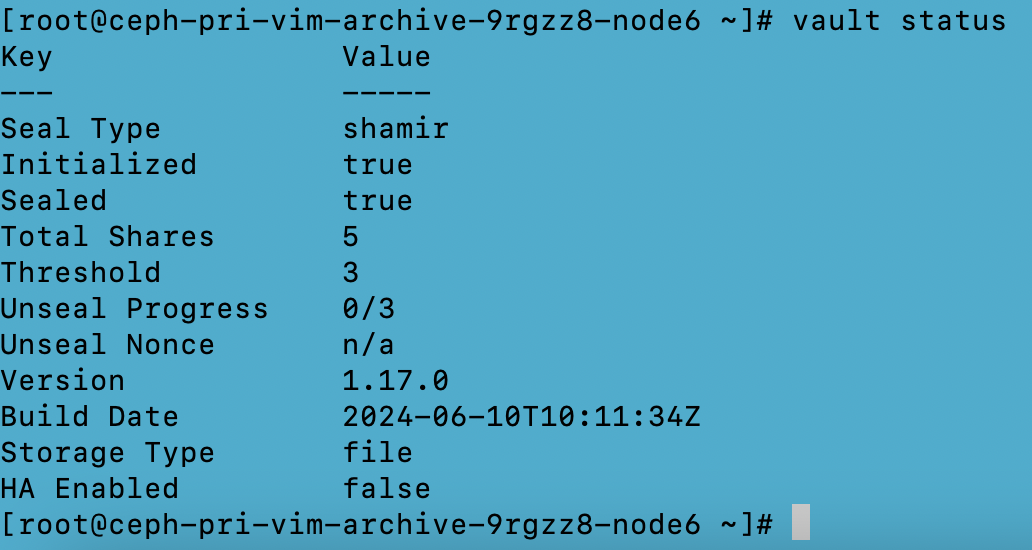
Note: Every initialized Vault server starts in a sealed state. Vault can access the physical storage from the configuration, but it can't read any of it because it doesn't know how to decrypt it. The process of teaching Vault how to decrypt the data is known as unsealing the Vault
Perform ‘vault operator unseal’ 3 times (as the threshold no. of keys for unsealing the vault is 3). After the vault server is unsealed, we will receive the below output:
-
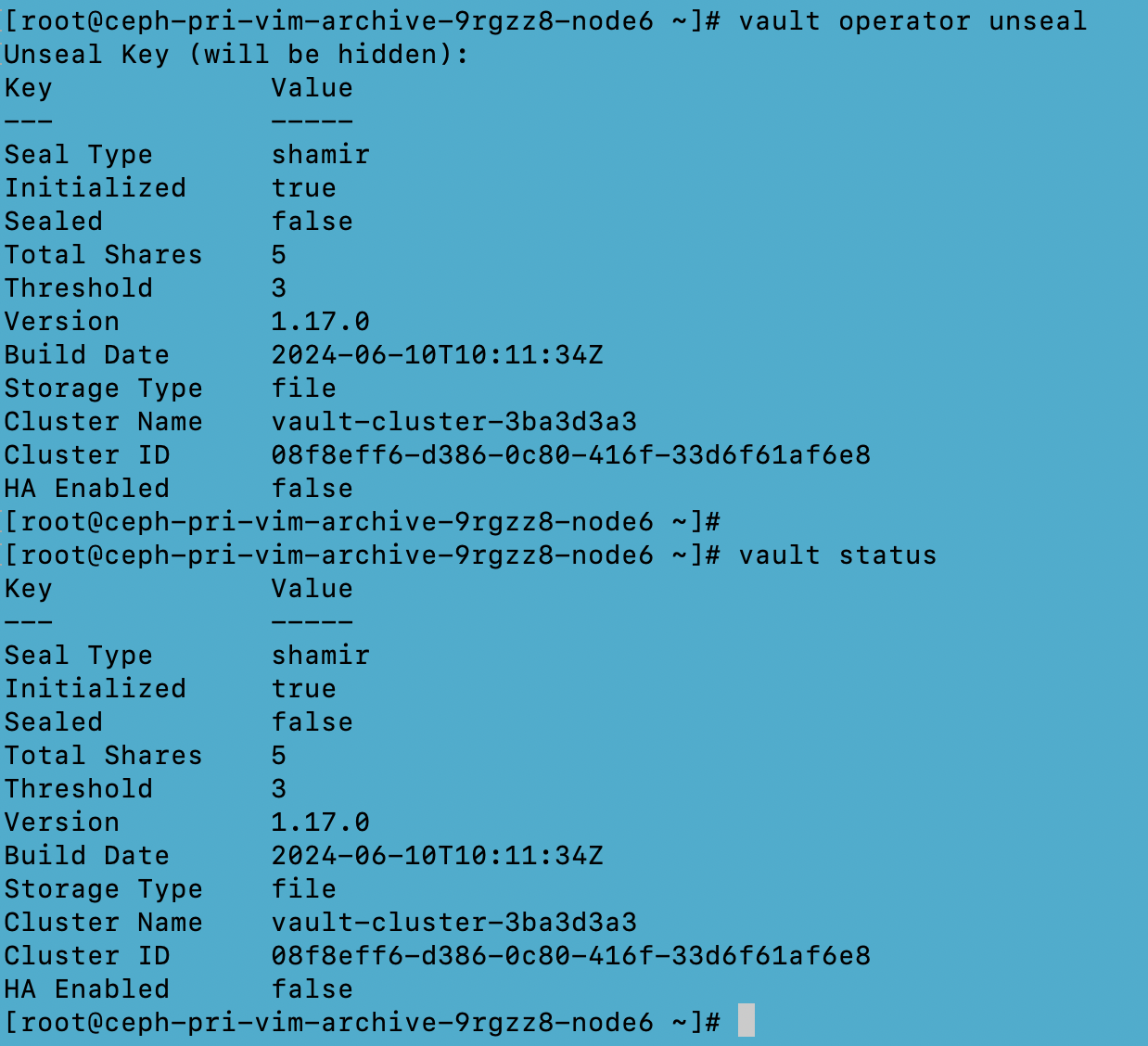
To unseal the vault server, use any of the three the Unseal keys obtained through the “vault operator init” and perform the “vault operator unseal” command three times, each time giving a unique unseal key.
-
The vault server will be unsealed when the vault status shows “sealed false”


-
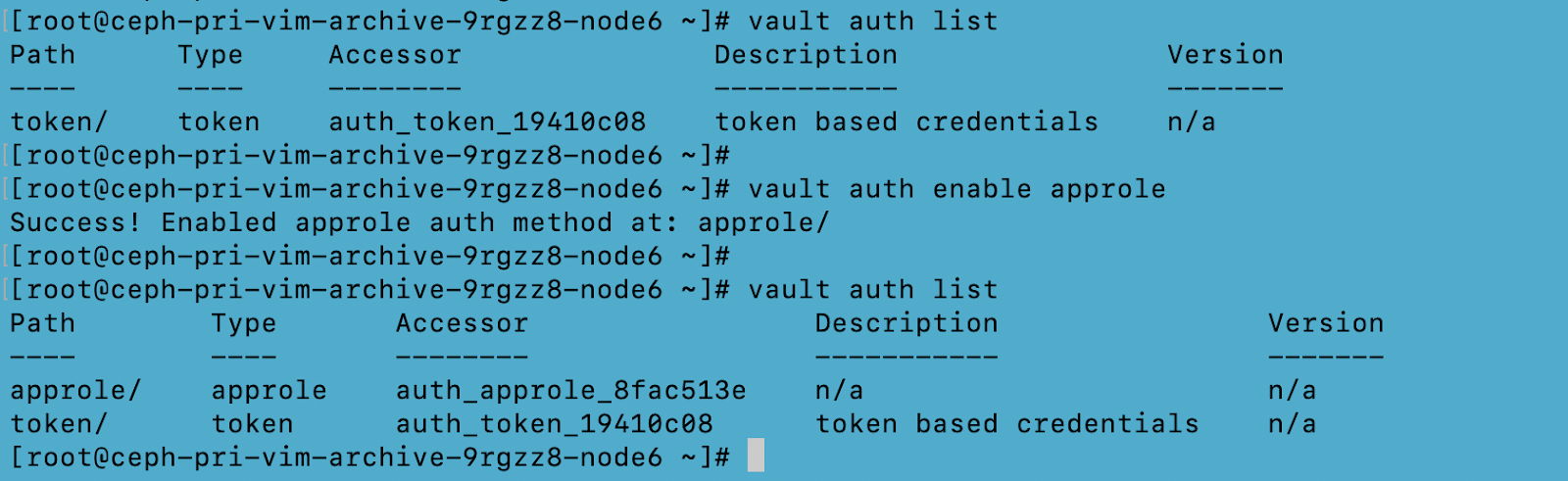
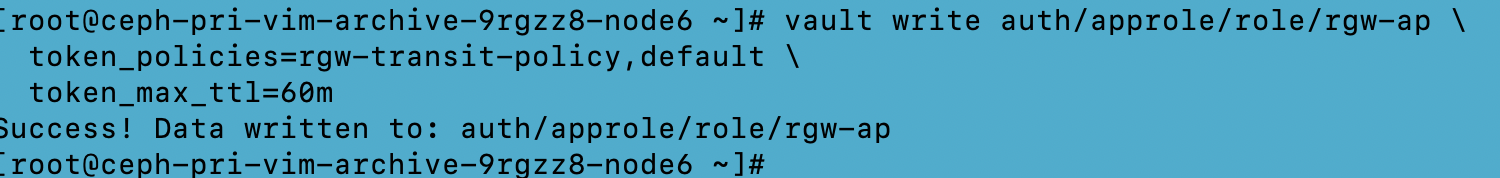
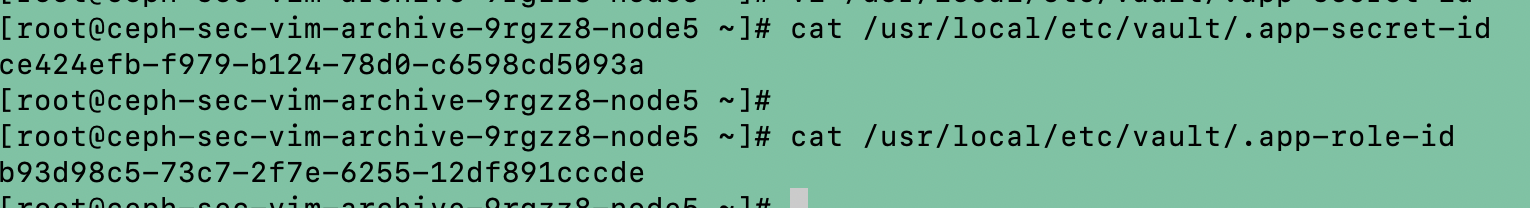
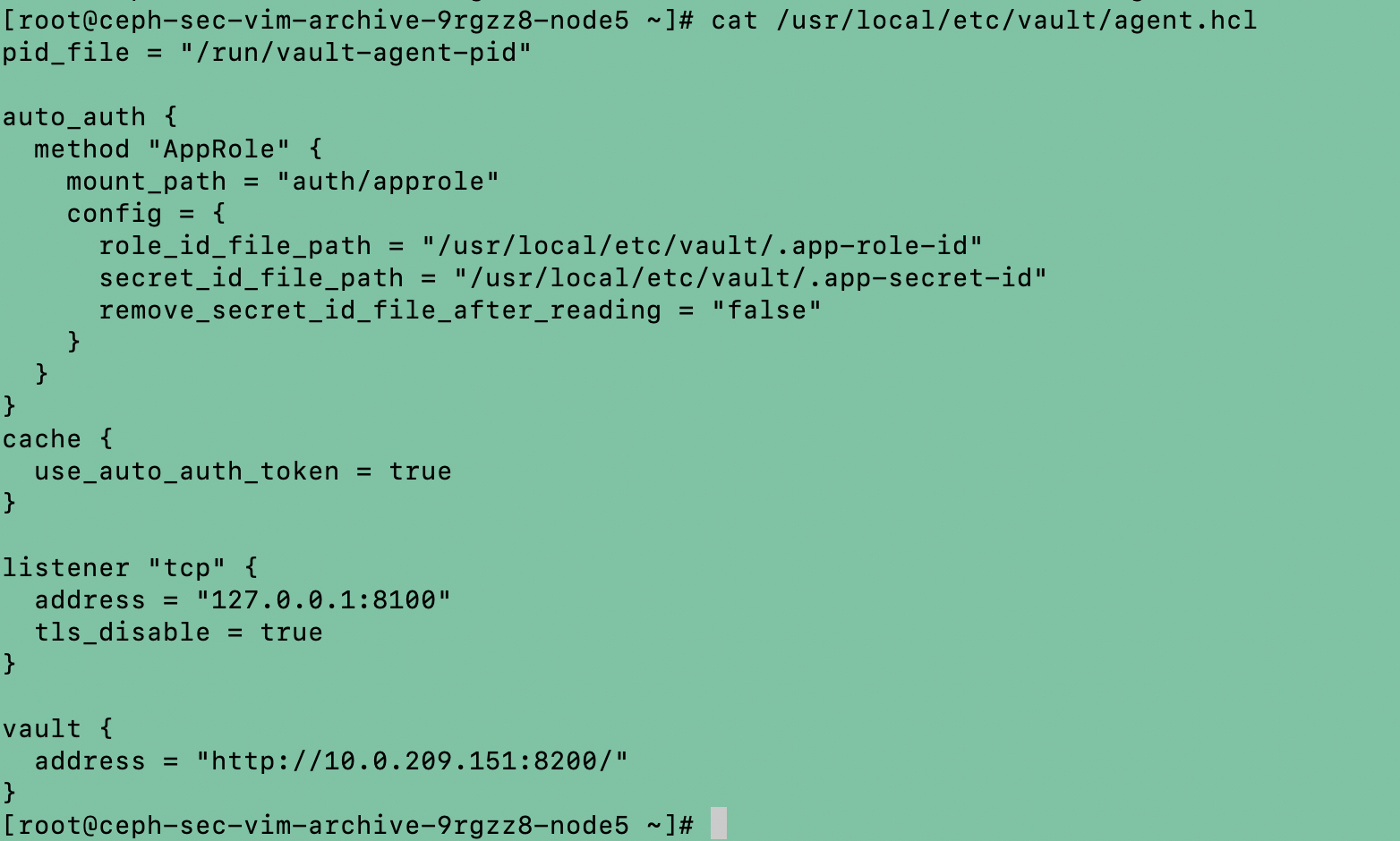
Configuring Vault Agent
Run the below commands on the vault agent node
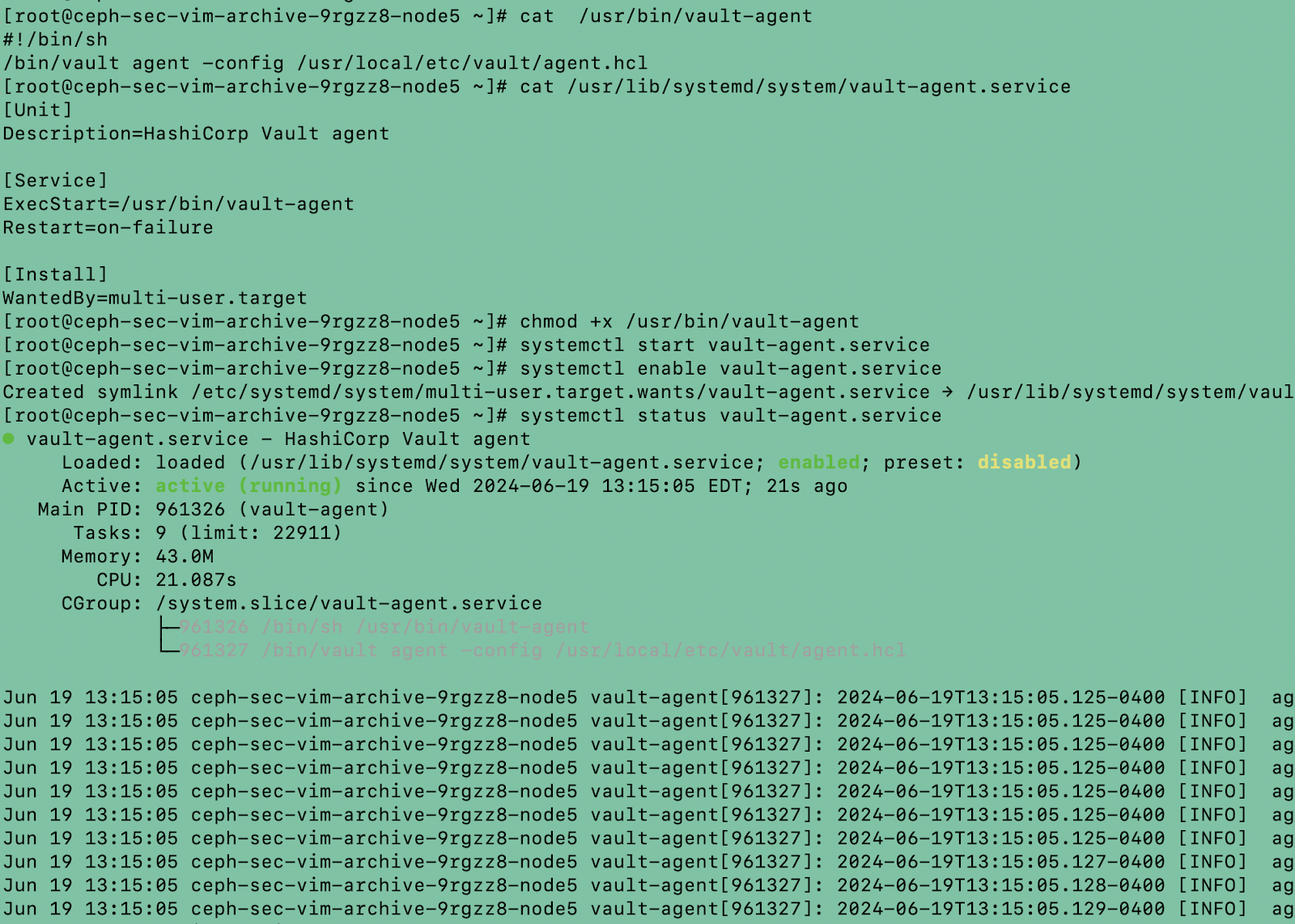
-
Integrating with Ceph RGW
-
Enable the below ceph configurations for the Vault to be used as an SSE-KMS for the Ceph. Assuming that the rgw service name is “rgw.1”
-
ceph config set client.rgw.1 rgw_crypt_s3_kms_backend vault
-
ceph config set client.rgw.1 rgw_crypt_vault_addr http://127.0.0.1:8100
-
This will be the vault_agent
-
ceph config set client.rgw.1 rgw_crypt_vault_auth agent
-
ceph config set client.rgw.1 rgw_crypt_vault_prefix /v1/transit
-
ceph config set client.rgw.1 rgw_crypt_vault_secret_engine transit
-
ceph config set client.rgw.1 rgw_crypt_require_ssl false
-
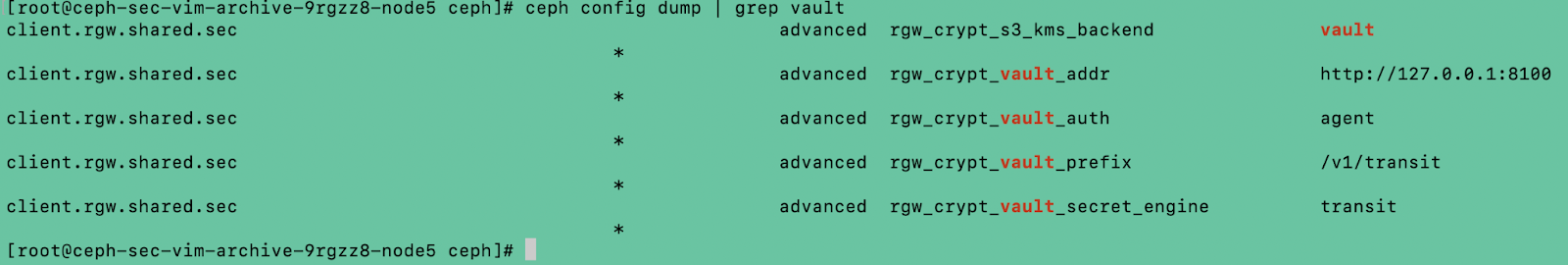
The image below shows Vault configs for the rgw service with the name “rgw.shared.sec”.
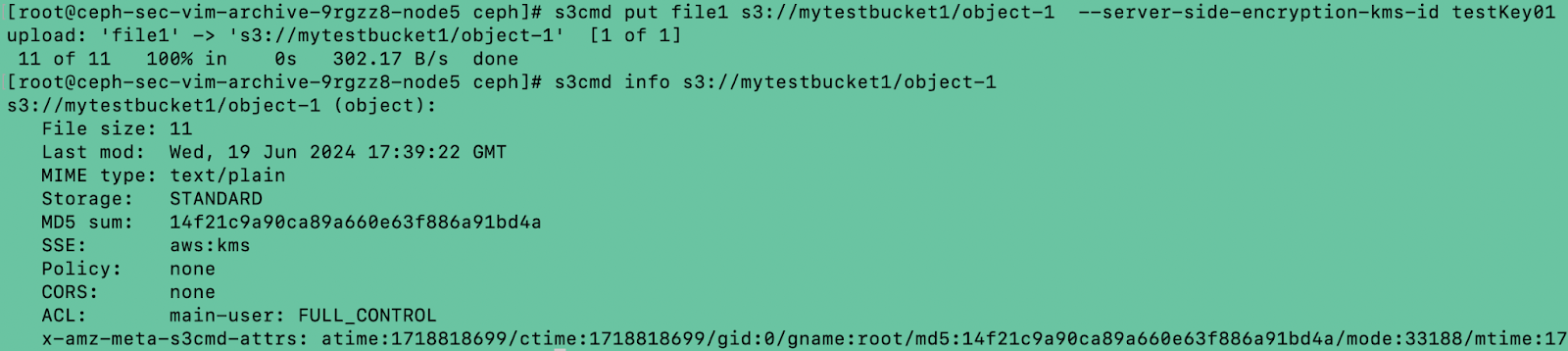
# s3cmd put file1 s3://mytestbucket1/object-1 --server-side-encryption-kms-id testKey01
# Download of the object will be similar to normal object "s3cmd get s3://mytestbucket1/object1"
#Highlights-home