The financial effects of cyberattacks continue to rise. Cyberattacks can occur in various ways. They can take the form of malware or ransomware, which is targeted at stealing confidential data or holding valuable information for ransom.
Sometimes, these attacks are designed to destroy confidential data to cripple organizations. In many cases, the data breaches involve internal threat actors.
Detecting a threat before it starts can help speed recovery even more.
Now, IBM QRadar can proactively start the Safeguarded Copy function to create a protected backup at the first sign of a threat.
The IBM FlashSystem Safeguarded Copy function helps businesses recover quickly and safely from a cyberattack, which helps reduce recovery to minutes or hours. It also creates multiple recovery points for a production volume. These recovery points are called Safeguarded Copy backups.
If an attack occurs, the orchestration software (IBM Spectrum/Storage Copy Data Management) helps create and identify the best Safeguarded backup to use. It also automates the process to restore data to online volumes. Because a restore action uses the same snapshot technology, it is almost instant; that is, it is much faster than the use of offline copies or copies that are stored in the cloud.
We’re talking about a layered approach to security here. Unfortunately there is no single silver bullet. The solution presented here too makes use of various IBM products that involve Storage, Orchestration and an early warning system. Let’s look at the storage feature first.
IBM Storage FlashSystem Safeguarded Copy function
The IBM FlashSystem Safeguarded Copy feature creates safeguarded backups that are not accessible by the host system. It also protects these backups from corruption that can occur in the production environment. A Safeguarded Copy schedule can be defined to create multiple backups regularly (such as hourly or daily).
Safeguarded Copy can create backups with more frequency and capacity compared to IBM FlashCopy® volumes. Creating Safeguarded backups also affects performance less than the multiple target volumes that are created by IBM FlashCopy.
The Safeguarded Copy function provides backup copies to recover data if a logical corruption occurs or primary data is destroyed.
The second product we want to discuss is from Orchestration / Automation stand point.
IBM Storage Copy Data Management
IBM Spectrum Copy Data Management, now Storage Copy Data Management, is a Copy Data Management (CDM) platform that can bring modernization to an environment without disruption.
IBM Spectrum Copy Data Management delivers “in-place” copy data management to enterprise storage arrays from IBM, NetApp, and Pure Storage, which allows the IT team to easily use its existing infrastructure and data in a manner that is efficient, automated, and scalable.
And finally, no organization security can be seen complete without an early warning system at the first sign of threat. This is where IBM QRadar comes into picture.
IBM QRadar Security Intelligence Platform
IBM QRadar Security Intelligence Platform products provide a unified architecture for integrating SIEM, log management, anomaly detection, incident forensics, and configuration and vulnerability management.
It is one of the most popular SIEM solutions on the market today. It provides powerful cyber resilience and threat detection features, such as centralized visibility, flexible deployment, automated intelligence, machine learning, and proactive threat hunting.
IBM QRadar can detect malicious patterns by using various data sources and analysis tools and techniques, including access logs, heuristics, correlation with logs from other systems (such as network logs or server logs), network flow, and packet data. Its open architecture enables third-party interoperability so that many solutions can be integrated, which makes it even more scalable and robust.
Having seen the core components used in the solution, lets now understand the solution itself with a scenario most application / business owners can relate to.
3-tier applications are co-existing alongside modern container based platforms. No matter which presentation layer is used by the application, the core is always data and it cannot exist in vacuum. Both relational and non-relational databases are the needed by modern or so called legacy applications. And, we know threat does not always have external origin, so how will we protect our precious data?
Let use discuss one possible solution here.
Solution overview
An SQL database audit is created at the database level that allows forwarding of SQL audit events to IBM QRadar. IBM QRadar understands the authorization events that are forwarded by SQL database and categorizes them correctly.
After the event classification is completed, the IBM QRadar administrator can define several rules to detect threats that are categorized under control and data path.
Upon threat detection, a cyber resiliency response is started in the form of a Python script that uses API commands to run a predefined SCDM scheduled job. The scheduled job feature of SCDM is chosen to restore the last known good configuration to clean space.
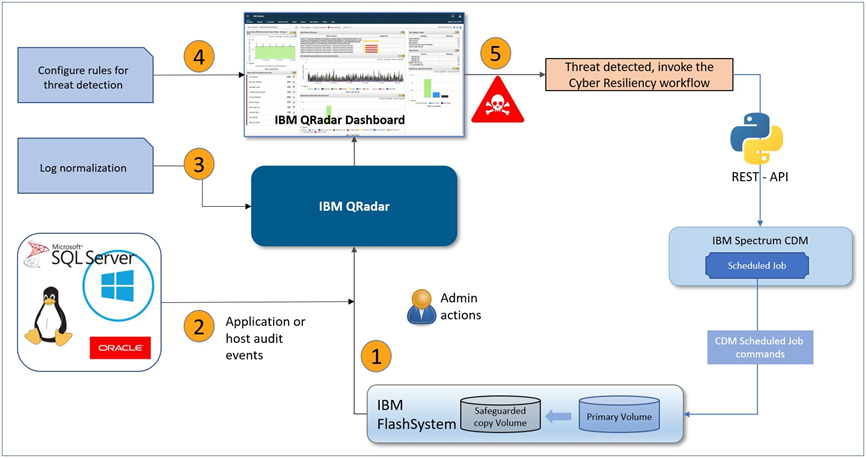
The solution discussed covers both data path use cases ranging from detection of threat of internal malicious user to ransomware attack and on control path side, it will also keep a tap on authorized users actions or compromised/shared credentials.
Moreover, it will also attempt to take preliminary actions such as identifying last backup and automatically mapping it to a host for further data scrutiny.
The solution describing the lab setup including threat response is documented in REDP-5691.
We have also created a video of the solutions.
Happy viewing and reading !!
#Featured-area-2#Featured-area-2-home#Highlights#Highlights-home