User management helps to manage users and their access to the application. Administrators can assign different access to users based on their role and authorization to work with the application.
As part of this article, we would be discussing the user management in IBM Spectrum Fusion appliance.
For information on IBM Spectrum Fusion, see https://www.ibm.com/docs/en/spectrum-fusion/2.1
User Management in IBM Spectrum Fusion
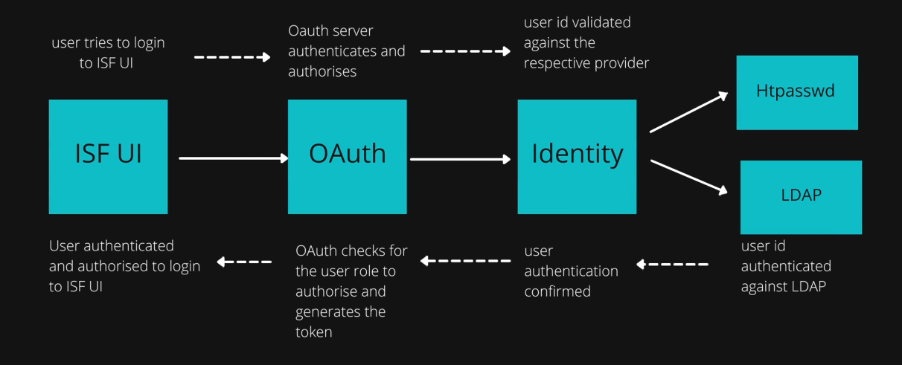
User management in IBM Spectrum Fusion is done through the OpenShift OAuth provider. Both the authentication and the authorization are taken care by the OAuth server. The following diagram shows the integration of the IBM Spectrum Fusion user interface with the Red Hat OpenShift OAuth server.
Authentication:
IBM Spectrum Fusion is integrated with Red Hat OpenShift OAuth provider for user authentication. User identity of the logging in user is determined with the identity against the identity provider. Once the user is authenticated by the OpenShift OAuth server, the user will be able to log in to IBM Spectrum Fusion.
To know more about Red Hat OpenShift OAuth server authentication: https://docs.openshift.com/container-platform/4.7/authentication/configuring-internal-oauth.html
Different identity providers can be configured with Red Hat OpenShift OAuth server. For this tutorial, we will be focussing on configuring HTPasswd and LDAP identity providers.
HTPasswd identity provider:
Steps to add HTPasswd identity provider through OCP console:
Pre-requisite:
OAuth CR should be present on the cluster.
Check for the same by running the command:
>> oc get oauth
The above command should give the oauth present on the cluster. If there is no outh, create an oauth cr first.
- Log in to the oc cli with a valid token.
- Run the following command to create an htpasswd file with a valid username and password:
htpasswd -c -b -B <htpasswd file path> <username> <pwd>
*Note: Multiple users can be added to the file.
- Once done, the HTPasswd identity provider can be added to the cluster by using the Red Hat OpenShift Container Platform console or the oc cli.
Using OCP console:
-
- Open the Red Hat OpenShift console and log in with valid credentials.
- From left menu, click User Management > Users.
- Click Add Identity Provider and select HTPasswd from the identity provider drop-down list.
- Specify a name. Browse and add the htpasswd file that you created in step 2.
- Click Create to add the htpasswd identity provider to the cluster.
*Note: The secret file will be created automatically into the cluster.
Using oc cli:
Create a secret as follows with the htpasswd file that you created in step 2:
oc create secret generic <secret name> --from-file= htpasswd =<path to htpasswd file> -n openshift-config
Once the secret is added, the identity provider gets added successfully to the cluster.
-
LDAP authentication provider:
Users may have their own LDAP servers or organization LDAP server which can be used to login to the IBM Spectrum Fusion user interface. However, authorization of the LDAP users is provided by Red Hat OpenShift itself.
Steps to add LDAP identity provider from the OCP console:
- Click User Management > Users.
- Click Add Identity Provider.
- Select LDAP from the list of identity providers.
- Specify the field values.
- Once done, click Create.
- Add the LDAP secret to the secrets.
- LDAP is now configured successfully.
- User can now login successfully to the Red Hat OpenShift console.
Once the identity provider is configured, we need to bind the users to a specific role to enable them to access IBM Spectrum Fusion user interface.
IBM Spectrum Fusion user interface currently supports two main Red Hat OpenShift roles and role-bindings:
- cluster-admin
- view
Both the roles are at cluster level and given access and permissions to the whole cluster.
Adding user to a user group with role binding:
As part of this article, we will be creating a group, bind it to a role and finally add users to it.
- On the Red Hat OpenShift Container Platform console, click User Management > Groups from left menu.
Click Create group.
- In the YAML editor, enter the following information:
- Name: Specify a relevant name to the group.
- Users: Add users to the group.
- Click Create to create the group.
- Check your created group in the created list of groups.
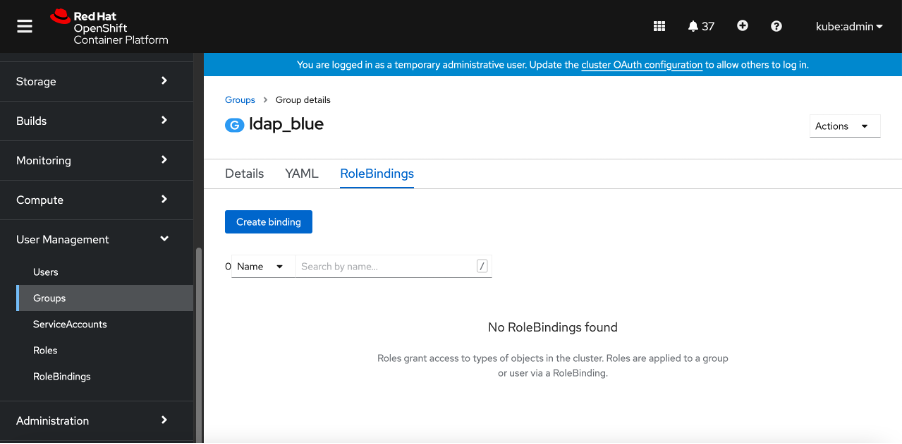
5. Next, select the created group.
6. Click
Role Bindings. Click
Create Binding.
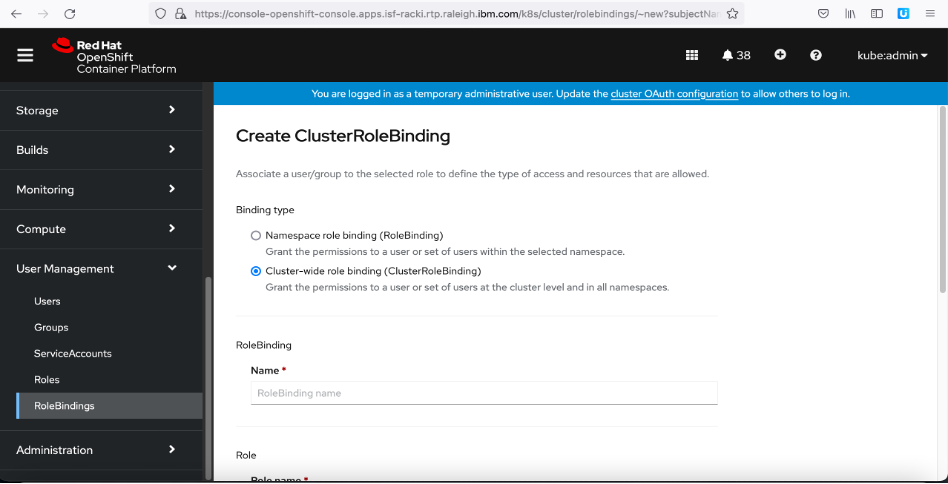
7. Click the
Cluster-wide role binding option.
8. In
Name, specify to add a role-binding name.
9. Next, from the
Role name drop-down list, select one of the two roles as per your requirements:
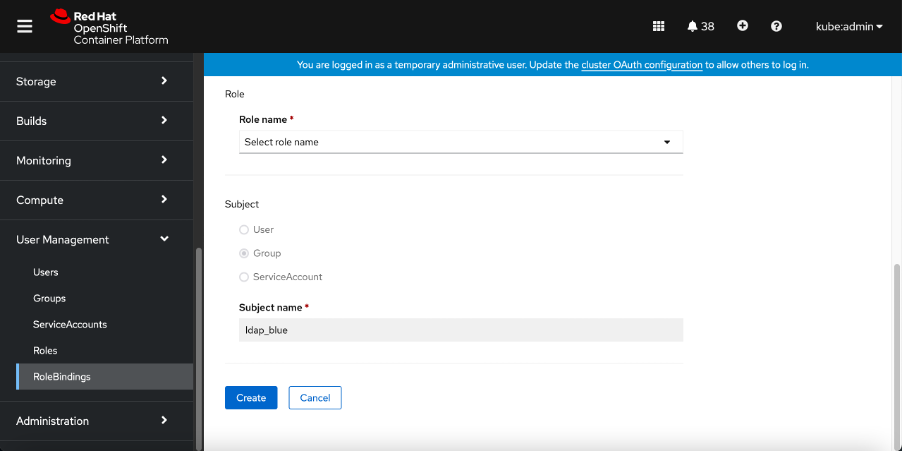
Review the specified information and click
Create to bind the role to the group. We have now successfully created a user group with added users for a specific role.
It's time now to log in to the IBM Spectrum Fusion interface by following the below steps:
- Go to the IBM Spectrum Fusion user interface by using a web browser.
- On the login page, select the identity provider for which the user is created.
- Enter valid user credentials and log in to the user interface.
Now, the user should be able to successfully login to IBM Spectrum Fusion user interface. Access to the IBM Spectrum Fusion interface will differ as per the logged in user's roles and permissions.
Cluster-admin – Cluster admin is the super-user. The user with cluster-admin access has admin level access to all the resources of the cluster. On IBM Spectrum Fusion user interface also, the user with cluster-admin role will be able to access all the functions on all the pages of the IBM Spectrum Fusion user interface.
- Access to all the pages of IBM Spectrum Fusion user interface
- Can add nodes, links, and storage disks
- Can deploy IBM Cloud Satellite locations
- Can download logs
View – A user with view access will have access to the entire cluster but with read-only access. Based on the role definition, a few resources may also not be available on the Red Hat OpenShift console. On the IBM Spectrum Fusion user interface, the following permissions will be available to the user:
- Access to all the pages of IBM Spectrum Fusion user interface
- Cannot add nodes, links, or storage disks
- Cannot deploy IBM Cloud Satellite locations
- Cannot download logs
With these steps in the article, you can now successfully manage users for the IBM Spectrum Fusion user interface by using the Red Hat OAuth authentication server.