Hi Jon Harry,
Thank you for your prompt reply.
We can not upgrade to verify 10 as of now. we are using IBM version 9.0.7 IF2.
I have moved one step forwards where user is prompted for 2FA and after that user gets below exception in trace.
I have below settings for custom totp, where I am setting secret key and username from session.
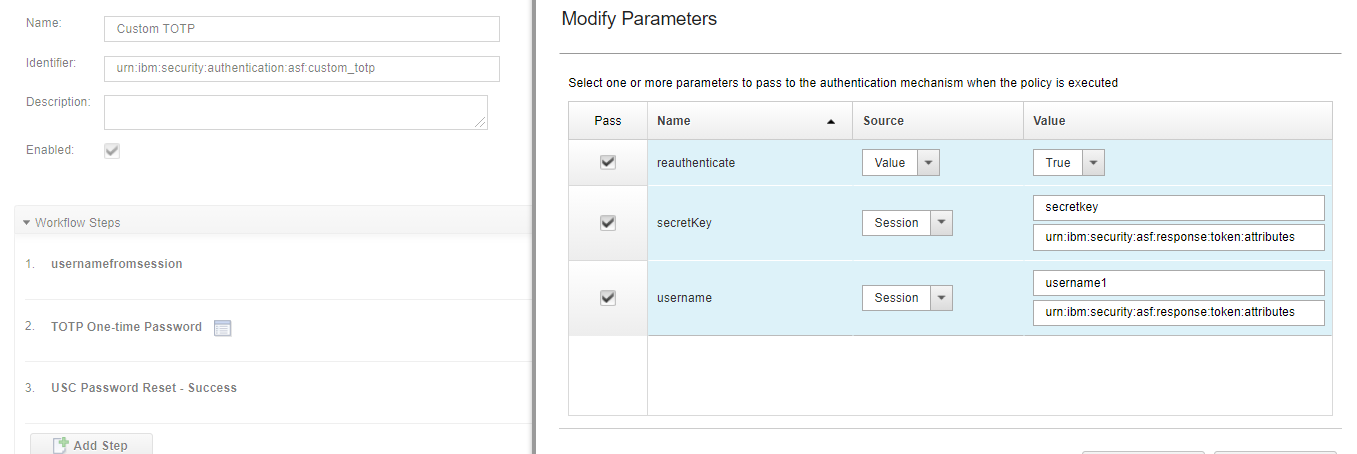
[7/22/21 20:16:49:788 SGT] 000032d6 id=00000000 vc.protocol.delegate.context.store.ResponseTokenContextStore < set(ContextIdentifier, AuthSvcToken) RETURN
[7/22/21 20:16:49:789 SGT] 000032d6 id=00000000 om.tivoli.am.fim.trustserver.sts.utilities.IDMappingExtUtils > traceString ENTRY Read
username from session mech:
admin[7/22/21 20:16:49:789 SGT] 000032d6 id=00000000 om.tivoli.am.fim.trustserver.sts.utilities.IDMappingExtUtils < traceString RETURN
[7/22/21 20:16:49:789 SGT] 000032d6 id=00000000 om.tivoli.am.fim.trustserver.sts.utilities.IDMappingExtUtils > traceString ENTRY Read
secretkey from session :
PO4ZLAEV2INKOGFOGS5K5EFDXR5MMO6P
I am seeing below error message in the trace file:
[7/22/21 20:16:59:594 SGT] 000032c5 id=00000000 com.tivoli.am.fim.authsvc.protocol.delegate.AuthSvcDelegate I processRequest(FederationManagerContext, ProtocolActionChain) java.lang.NullPointerException
at com.tivoli.am.fim.authsvc.action.authenticator.totp.TOTPAuthenticator$4.execute(TOTPAuthenticator.java:255)
Flow:
1.
User access below URL to enter username:
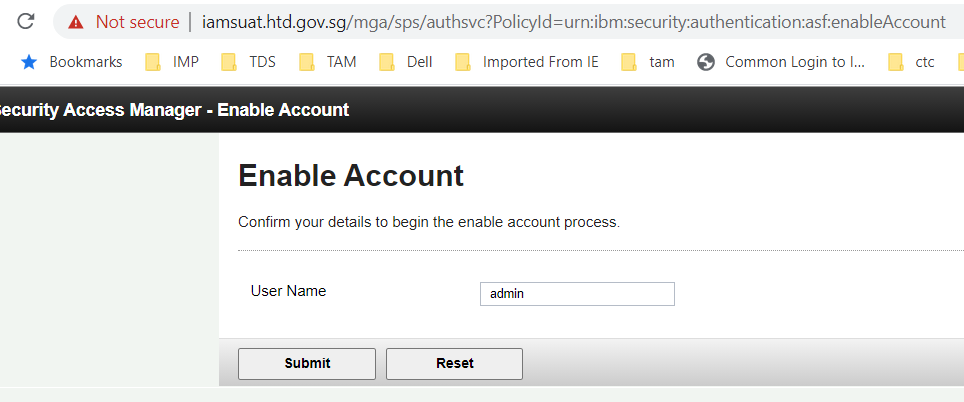
2.
Prompted for 2FA Selection
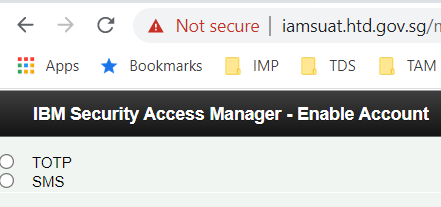
3. Once selected 2FA: (TOTP)
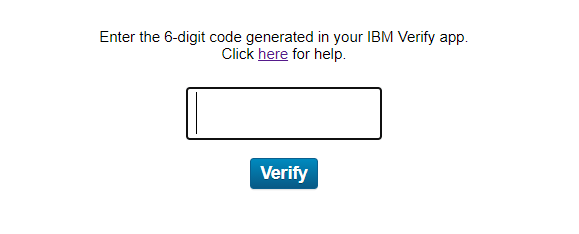
4. gets below error:
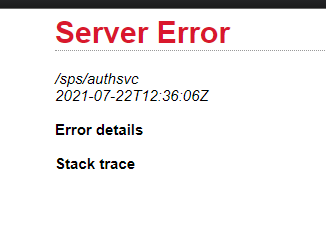
Regards,
Mayur
------------------------------
mayur boob
------------------------------
Original Message:
Sent: Tue July 20, 2021 06:19 AM
From: Jon Harry
Subject: Trigger 2FA (TOTP & SMS ) with un-authenticated session
Hi Mayur,
I think we're going to need some more information on the failure in order to figure out what is going wrong.
What version of ISAM/Verify Access are you using? (can you update to v10 and use native Branching capability?)
What is the failure condition? Are you getting an error message? What is the URL flow?
You'll need to look at the message.log of the AAC Runtime to see if there is any message or exception recorded there.
If you find exceptions, be sure to look for the first exception that is thrown - that is most likely to show the root cause.
Jon.
------------------------------
Jon Harry
Consulting IT Security Specialist
IBM
Original Message:
Sent: Sun July 18, 2021 11:34 PM
From: mayur boob
Subject: Trigger 2FA (TOTP & SMS ) with un-authenticated session
I have referred Shane Weeden blog :
Branching Authentication Policy in ISAM Advanced Access Control - Shane Weeden's Blog
| Shane Weeden's Blog |
remove preview |
 |
| Branching Authentication Policy in ISAM Advanced Access Control - Shane Weeden's Blog |
| PLEASE NOTE (update August 2020): For customers running IBM Security Verify Access v10 and later, branching AAC policy is now a built-in feature. For more information see: https://www.youtube.com/watch?v=msHP1Ha_dUg. The information in the rest of this article is still relevant for older version of IBM Security Access Manager that do not support out-of-the-box branching AAC policy. |
| View this on Shane Weeden's Blog > |
|
|
I am creating self care to enable user account:
1. User enter user name.
2. Mapping rule to fetch username details via SCIM call and setting user name in SPSSession ("IDMappingExtUtils.setSPSSessionData(key,value)").
3. Asking user to select 2FA either SMS/TOTP. (note: if is do not provide this option and trigger 2fa as default totp it works fine).
4. Trigger respective 2FA mechanism. currently it fails at this step.
------------------------------
mayur boob
------------------------------