Hi Piyush,
I wasn't aware that an error was caused when non-existing groups were specified in the groups list of an external users assertion from AAC->Reverse Proxy. I would have expected that the groups that didn't exist would be ignored. I expect a change in that behaviour would require a Request for Enhancement.
You can't assign groups that don't exist to a user. Part of a group's definition in Verify Access is a UUID which is what links it to entries in ACLs. Adding a group that doesn't exist wouldn't make sense.
If you just want the group names to be available in the user's credential, but you don't need to use them in ACLs, you could pass the group list as a standard attribute rather than as the group attribute. You should be able to make this change somewhere in the OAuth mapping rules or in the mapping rule of the STS chain that is validating the JWT.
If you do want some groups from the JWT returned as "real" groups (because they exist in Verify Access and you want to use them for access control) but there are others that you want to ignore, I would suggest that you need to add some logic to the mapping rule or STS chain so that it filters out any groups that don't exist. You could do this with real time checking of the group names but it would probably be more efficient and easier to implement just to have a hard-coded list of groups you care about and just use this for a filter.
Jon.
------------------------------
Jon Harry
Consulting IT Security Specialist
IBM
------------------------------
Original Message:
Sent: Fri June 11, 2021 06:09 AM
From: Piyush Agrawal
Subject: AAC - Global setting - Point of Contact
Hello,
We have a situation where Authentication with "jwt bearer assertion" fails due to the claim on jwt token contains groups which are non "Access Manager groups".
We are using prebaked profile "Non-AM Username, AM groups and extended attributes"
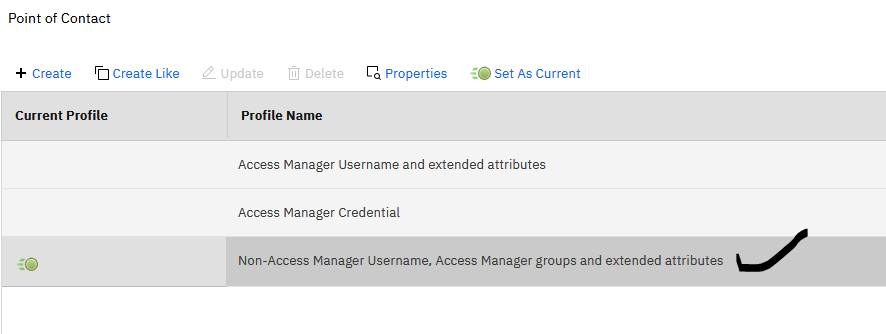
Now we have two solutions
- import/create all groups Access manager (which looks practically impossible as we don't know which groups need to be added in advance before we see actual 401)
- And if possible create a profile that allows sessions for non-access manager groups also.
Is it possible to create a profile in "point of contact" with non-access manager groups and users?
Do you think it will work with solution 2?
------------------------------
Piyush Agrawal
https://www.linkedin.com/in/piyush-norway/
------------------------------