
The threat actor behind the LockBit ransomware gang that uses Ransomware-as-a-Service (RaaS) released a version of their encryptor, dubbed LockBit 3.0 or LockBit Black in June. In conjunction with the release of a new version of the ransomware, the threat actor also published a bug bounty program for their site and tools. LockBit 3.0 comes just about a year after the summer 2021 deployment of LockBit 2.0. As with LockBit 2.0, LockBit 3.0 includes service features such as an option for users or affiliates to download files stolen from the victim machines.
What is Ransomware as a Service (RaaS)?
RaaS is a subscription-based model that allows users or ‘affiliates’ to carry out cyberattacks using ransomware tools. RaaS is different from your usual, run-of-the-mill ransomware in the way it provides crafty tools to enable subscribers - who pay to be an affiliate of the program - the use of malicious software.
As a RaaS model, the LockBit design is intended to be used by a wide range of separate threat actors paying to use the LockBit encryptor. RaaS pricing adds certain challenges for threat hunting, as the tactics, techniques, and procedures (TTPs) can vary widely, based on the affiliate leasing the RaaS service. Typically, the deployment and execution of ransomware will fall towards the end of the attack chain. By the time the ransomware is executed, and the damage of the initial breach has been fully realized, sensitive files have been stolen under the threat of being published and these files are now inaccessible on the victim machine.
As with previous iterations of LockBit, IBM Security QRadar EDR, formerly known as ReaQta, successfully detects and blocks the LockBit 3.0 ransomware execution automatically.
IBM Security QRadar EDR immediately detects ransomware behaviour then prevents its execution.
Differences between LockBit 2.0 and LockBit 3.0
There are some notable differences between LockBit2.0 and LockBit 3.0. Most prominently, security researchers have noted code similarities to the DarkSide or BlackMatter ransomware strain, in addition to obfuscating Win32 API calls.
LockBit 3.0’s main routine must be decrypted via a key passed as an argument to the executable. Without this key, the ransomware will not successfully execute.
Using IBM Security QRadar EDR platform’s DeStra to detect strains.
IBM Security QRadar EDR detects and stops ransomware activity based on ransomware behavior. While this provides complete visibility and protection of endpoints against ransomware activity, an additional layer known as DeStra — a real-time scripting engine that allows security operators to write custom detection and response rules — can provide simple ways of identifying specific strains of ransomware behind the observed activities.
DeStra enables threat hunters and analysts to deploy custom detections, for example, the activity observed during a successful threat hunt, which can provide custom alerting on specific behavior. In addition to detecting specific process behavior, DeStra rules can also use Yara rules that can be tested against files and in-memory processes.
In order to detect a specific strain of ransomware with DeStra using its Yara module, the DeStra user can bind the Process Created and In Memory Executable events for the DeStra script to examine.
With these events, a Yara rule can be loaded by DeStra to identify matches. During the review of LockBit 3.0 with QRadar EDR, a DeStra rule examining these two events against several Yara rules detecting specific ransomware strains identified the execution of LockBit 3.0 as BlackMatter ransomware. The rule published by bartblaze (strings previously adjusted by QRadar EDR simply changing ‘DarkSide’ to ‘BlackMatter’) triggered a match on one LockBit 3.0 sample prior to the decryption of the ransomware’s main routine:
0x8876:$: C7 00 2A 00 72 00 C7 40 04 65 00 63 00 C7 40 08 79 00 63 00 C7 40 0C 6C 00 65 00 C7 40 10 2A 00 00 00
A Yara rule originally detecting DarkSide included in a DeStra rule also detected LockBit 3.0
Adding credence to the heavy influence of the DarkSide or BlackMatter code includes other existing Yara rules to detect LockBit 3.0 samples as BlackMatter ransomware.
Additional observations of LockBit 3.0
During the full execution of the latest LockBit ransomware sample, QRadar EDR detected registry modifications which would restrict access to Windows’ Event Logs by adding permissions to each application and service log under HKLM\Software\Microsoft\Windows\CurrentVersion\WINEVT\Channels\
LockBit 3.0, when allowed to execute, modifying permissions to access Windows' Event Logs via the registry.
The value used is in the security descriptor definition language (SDDL) format. A translated version of the permission added is as follows:
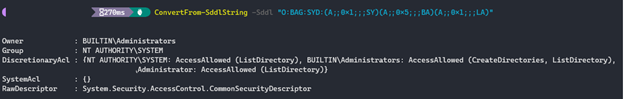
While the technique does bar access to viewing Windows event logs, it has little effect on overall detection capabilities, provided the endpoint is being monitored with an effective endpoint detection and response (EDR) tool. Additionally, such a high volume of suspicious registry modifications makes detection of the LockBit behavior easier:
LockBit 3.0 iterates over permissions for Windows Event Logs
In order to stay protected against new, evolving ransomware strains and next generation cyber threats, organizations need to opt for an autonomous EDR security that is able to leverage behavioral-based monitoring. Also, having accurate and near real-time response can help protect sensitive data that matters.
IBM Security QRadar EDR helps customers stay protected from known and unknown ransomware threats like LockBit 3.0, among others.
Looking for the right EDR tool for your business? Download our Buyer’s Guide to find out which questions to ask when opting for a modern EDR solution.
For more information about IBM Security QRadar EDR, visit our website