This live lab example today is about the interaction between SIEM360 security (detection) and security SOAR (response). It is about a possibility in which a QRadar Offense is automatically forwarded to the Security SOAR system. In order to realize this, a plug-in is established in the QRadar system, which establishes this connection to the SOAR system. This plugin offers two options for this:
Manual Escalation
Manual transfer via buttons of a QRadar Offense directly from the Offense Panel

Automated Escalation
Automated distribution of a QRadar Offense based on preset rule conditions and template settings

Activity Feed
In the SOAR system, a “new incident” is automatically created from the “forwarded” QRadar Offense and information that has already been collected is adopted from the QRadar Offense. So far so good.

SIEM Use-Case Example- Context
But first of all a little bit of context to the SIEM application example. What exactly is it about?
It is a typical scenario in which privileged admin rights can be activated in a collaboration system (Notes / Domino). With these "Full Administration Access Rights" the security level of the "Access Control List" in Domino databases is circumvented.
Database - Access Control List

After activating this extended right, this administrator has the option of accessing data records and information in databases without being included in the respective access list of the database! So much for the technical depth of detail of this surveillance scenario.
Domino Administrator - Full Access Rights
This “rights extension” is a very helpful feature for Domino administrators when it comes to troubleshooting or database migrations, where settings of the database access list cause “problems” or “rightly” for security reasons.
At the same time, however, these extended rights enable unauthorized access to sensitive data sets and databases to take place "unnoticed". Administrators who are allowed to activate this extension can "process" data records / databases without being noticed. And with it a possible compliance / policy violation!

Crown Jewels Container - Notes / Domino
For this reason it is a good decision to monitor / audit the activation of these extended "Full Administration Access Rights" in every Domino infrastructure!
One of the added values of a Domino platform is "Rapid Application Development". Some may still remember :)
What does that mean? With relatively easy to use board tools, @ formula and script language, applications or workflows for departments or business processes can be provided quickly and easily.
Domino - History
For this purpose, unstructured data records are generated via masks, safely stored in a .nsf container (Notes Storage File). These data records within the nsf container are accessed through different views, or the data records are processed and presented using select statements.
And the internal PKI structure and access control down to the field level enables these data records to be protected or controlled flexibly for access.
This technology approach has resulted in countless databases in a domino environment, in which many of the so-called "crown jewels" are certainly stored.
Detect - Full-Access-Administrator Events
And that's exactly what this specific SIEM scenario is all about.
If this extended "full access administration function" is activated in the Domino system, this specific event is generated in the Domino system and forwarded to the central SIEM system via SNMP trap.

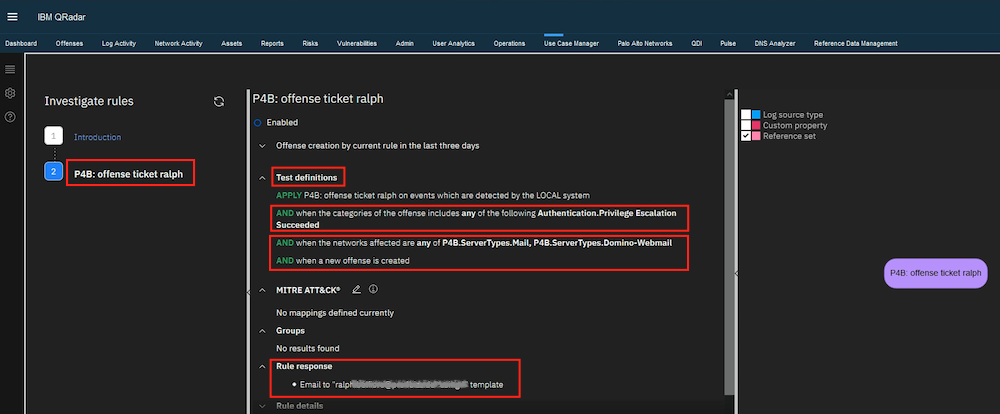
Custom Rule - DominoFullAccess Testdefinition
As soon as the SIEM detects this event in the central rule monitoring (Custom Rule Engine), an offense is automatically generated. I created and provided a specific custom rule in the SIEM to recognize this scenario.

Custom Rule - Response Options
This offense generated from the rule recognition is automatically assigned a corresponding “offense category” in this scenario - Authentication / Privilege Escalation Succeeded.

Offense Notification
The peculiarity here is that the subject for this e-mail has been modified in the SIEM e-mail template and a prefix “P4B-SecMngt” is added.
The category Authentication.Privilege Escalation Succeeded (classification in Cyber Kill Chain) ensures in the detection process that a prioritized offense notification is generated and sent to a specially stored e-mail address.
E-Mail Example
This prefix is then typically used in an IT service management tool to generate an internal service ticket.

Detection - IoC / Response
In this example, the email address is used by the internal SOC team. In the first step, the offense within the SIEM is analyzed by a SOC team member and assigned manually to an internal team member.
This assignment is the trigger for the Security SOAR plugin and forwards this QRadar Offense to the SOAR system.

Response / SOAR Playbook
This is one way of how an offense can be automatically forwarded from the SIEM QRadar to the SOAR system and the IT service management process and remediation can be initiated.
After the detection phase, further analysis, administration and structured processing of the detected “now” incident continues in the SOAR system. For this purpose, so-called “playbooks” can be created and stored manually or automatically.

Dynamic battle plan / automated Response
These playbooks then provide methods, actions, procedures and additional tools to deal with this incident in a structured manner. In short: a dynamic battle plan for countermeasures.
In addition, the documentation of the steps to resolve the incident helps to make IT security management sustainable, resilient and more resilient.

SIEM - long-term campaign
Experience has shown that SIEM is more of a long-term campaign. If the factors mentioned are subjected to regular reviews and supplemented with newly acquired knowledge, the degree of maturity of the SIEM process increases automatically.
An additional result in the development of the SIEM maturity level are KPIs that can be used to show trends and further optimization potential.
Automated Cyberdefense / paradigm shift
Maybe i overlooked some points, but: from my point of view the following organizational factors must be monitored in the entire SIEM process:
- why do we do what we do?
- what is the mission
- Connect “silos” across departments - do all the people involved know the mission?
- Which business processes are of particular importance for the company?
- Identify IT systems which belong to these business processes.
- Paradigm shift: Develop a mindset from compliance (manual and reactive) to risk management (automated and proactive)
- Regular feedback and adjustments in the SIEM process