Introduction
As data exponentially grows and becomes the lifeblood of every organization, it also creates significant security challenges. Enterprises need to know where critical data is stored, how it’s accessed, and how to best protect it. With an increasing amount of data spread across on-premises systems and multiple cloud environments, protecting sensitive data has become more complex than ever.
IBM Guardium Data Protection helps reduce the risk of data breaches by continuously monitoring access to data, both on-premises and across multiple clouds. It provides real-time security visibility and intelligence, allowing organizations to create and enforce policies that automatically protect and remediate data—whether it’s at rest or in motion—while ensuring compliance with privacy regulations that carry stiff penalties. Guardium also helps organizations regain visibility and control over sensitive data by offering predefined security and compliance policy templates that can be customized to meet specific enterprise needs. These templates provide visibility into user entitlements, dormant accounts, excessive privileges, and access governance controls. Additionally, Guardium’s vulnerability assessments proactively scan databases for vulnerabilities, misconfigurations, authentication gaps, and missed patches, further enhancing your data security posture.
The first step to robust data protection is knowing where your sensitive data resides. IBM Guardium Discover and Classify enables enterprises to discover and classify sensitive data—whether known or unknown—across both on-premises environments and in the cloud, whether structured, unstructured, in motion, or at rest. With its network-based analytics and compliance-ready capabilities, Guardium Discover and Classify provides the insights required to protect your data. When combined with IBM Guardium Data Protection, it offers a complete data security solution, ensuring that enterprises are well-equipped to secure their critical assets.
IBM Security Discovery & Classify (ISDC) acts as the bridge between Guardium and other security platforms. ISDC collects and processes data from multiple sources, including Guardium, to offer deeper insights into your security posture. It integrates with Guardium Data Protection to automate data discovery, synchronize policies, and enable monitoring across a variety of data sources. This integration enables organizations to track data flows and access patterns across the environment, ensuring sensitive data is always protected in real-time.
In this tutorial, we will guide you through the process of integrating IBM Guardium Data Protection with IBM Security Discovery & Classify (ISDC). This integration allows you to automate the discovery of sensitive data, synchronize Guardium policies with ISDC groups, and continuously monitor and protect data across your organization’s hybrid cloud and on-premises environments.
Objectives of the Tutorial
By the end of this tutorial, you will learn how to:
-
-
Configure the necessary prerequisites for integrating ISDC & GDP
-
Automate the synchronization of Guardium groups and policies with ISDC.
-
Monitor sensitive data and manage policies efficiently through the integrated system.
Prerequisites
Before diving into the integration steps, make sure you have the following:
-
-
A functioning Guardium Data Protection environment.
-
A properly set up ISDC instance.
-
Administrative access to both Guardium and ISDC systems.
-
Basic understanding of database security and policy management.
With that, let’s get started by preparing the Guardium environment and configuring the required settings for seamless integration with ISDC.
CHAPTER 1: INSTALLATION
PREREQUISITES
1. DC-Engine installed: version 3.8.x+. (for this tutorial i am running on 3.10.4 version)
2. Login at least once to update user password, or create a user with access to data source catalog.
3. Add kong routes for integration:
3.1. ssh to ISDC terminal
ssh admin@<isdc_ip>
3.2. Edit kong-configuration configmap with the below command
kubectl -n <yournamespace> edit cm kong-configuration
3.3. Add a new route under section by pressing I on the keyboard for Insert mode. Pay attention to spacing. Helm applies only spaces, so you may need to remove all tabs and do spaces instead:

3.4. Save changes by pressing ESC on the Keyboard and type :wq and restart kong by executing below command
kubectl -n <yournamespace> delete pod kong-<pod id>
3.5. To get the kong id execute
Kubectl -n <yournamespace> get pods
INSTALLATION INSTRUCTIONS
1. For ISO deployment, copy the installation tar into /home/admin directory of ISDC server or download it from the storage.
NOTE: Get the credential for the storge path from the 1touch team
cp /opt/install/guardium-data-protection-0.0.1.tgz /home/admin/
2. Extract the archive using tar:
tar xvf guardium-data-protection-0.0.1.tgz
3. Change directory to guardium-data-protection chart data.
cd guardium-data-protection
4. Now you need to know what kind of install used - helm install or dc-engine cli. In case dc-engine cli install edit values-test.yaml and add/edit below content:
5. To get the Appliance ID, execute the below command. Rest of the needed parameters are highlighted in yellow in the last step.
kubectl -n <yournamespace> get pods -l app=analytic-core -o jsonpath='{.items[].spec.containers [].env[?(@.name=="APPLIANCEID")].value}'
6. Now Installing the Helm Chart by executing the following command
helm -n <yournamespace> upgrade --install guardium-data-protection . --values values-test.yaml
7. Execute the below command to get the pod details and also the name of newly created pods for guardium-data protection
kubectl -n <yournamespace> get pods
8. Execute the below command by providing the Guardium pod name that we got from the previous step to confirm the chart has been installed successfully.
kubectl -n <yournamespace> get pods <guardium-data-protection-podname>
9. Once the Pods are in running state, access the below url where you will be redirected to the swagger documentation site.
https://<cm_hostname>/integration/guardium-data-protection/docs
10.Expand and run the endpoint below. Confirm it passes connectivity to db and sftp storage:
Endpoint: /connection_statuses

11.Run the endpoint below. Confirm you can see if any repos from GPD come through into ISDC:
Endpoint: /get_repositories_data
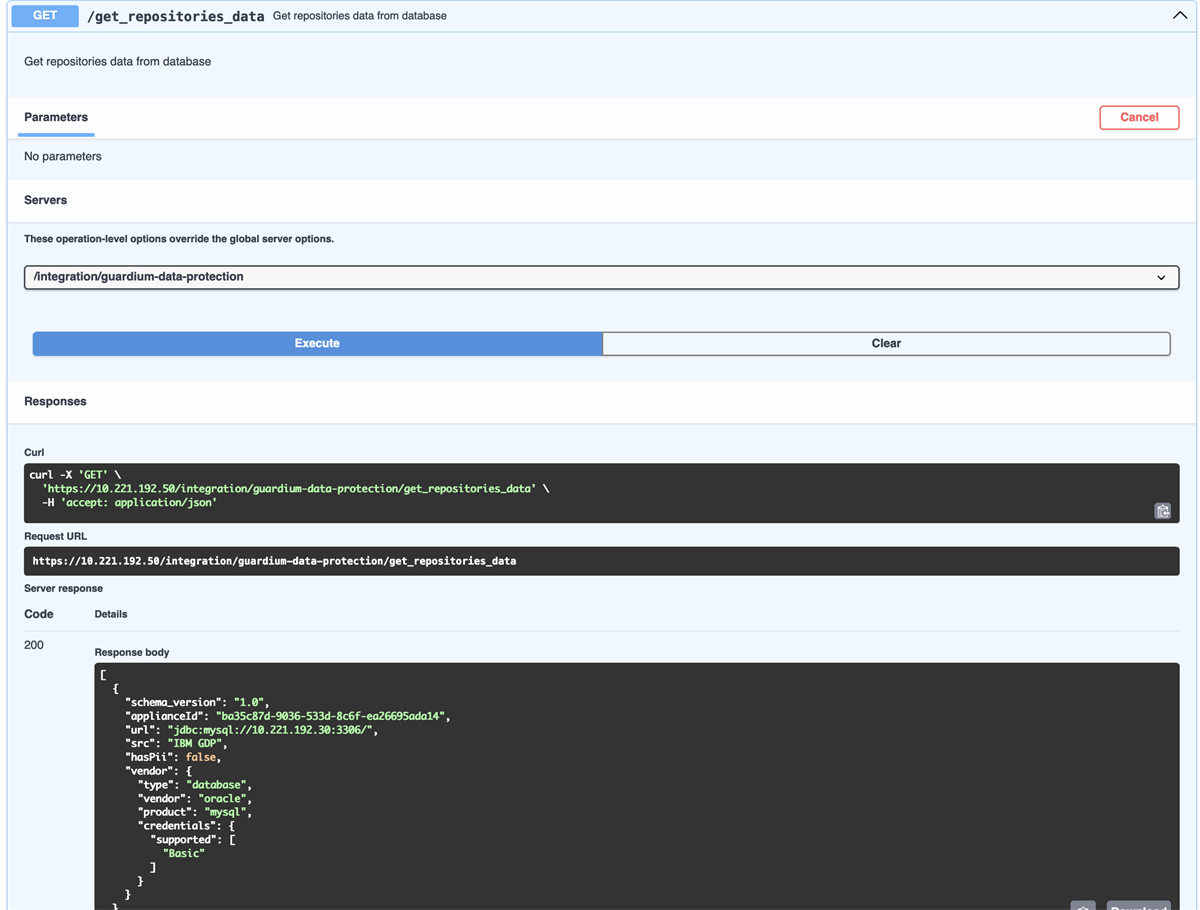
This Confirms a Successful integration between ISDC and GDP
CHAPTER 2: Use cases of Integrating GDP with ISDC
Use case 1:- GUARDIUM DATA PROTECTION DATA SOURCE SYNC
Prerequisites
Workflow
The synchronization process is automated and runs on app startup. By default, it also re-syncs every hour, controlled by the TASK_DELAY_IN_HOURS parameter. The process can be manually triggered using the Integration API.
Here’s how it works:
-
-
It checks for data sources supported by ISDC and imports them into ISDC through a Kafka API connection.
-
Note: Credentials are not imported. Once a data source is created, you must configure the credentials separately.

Use case 2:- Guardium Groups and Policies Synchronization
Prerequisites
Before setting up the Guardium Groups and Policies Sync, ensure the following properties are defined to control the groups created based on ISDC discovery results. If a group with the specified name already exists, it will be updated. If it does not exist, a new group will be created:
-
-
DB_VENDOR_GROUP_NAME=Inventa_db_vendor
-
HOST_GROUP_NAME=Inventa_hosts
-
DB_GROUP_NAME=Inventa_db_name
-
TABLENAME_GROUP_NAME=Inventa_db_tablename
Workflow
The synchronization process is automated and follows a scheduled workflow:
The sync process is triggered automatically when the application starts.It is set to resync once every hour by default, controlled by the TASK_DELAY_IN_HOURS parameter. Future versions of this functionality will be controlled via API.Policies are applied based on templates from Guardium Data Protection.The integration automatically assigns the required groups to these policies, ensuring that data imported into ISDC-related groups is continuously monitored.This synchronization ensures that the Guardium groups and policies remain aligned and up to date for effective data protection.

Use case 3:- REPORTING
|
PREREQUISITE
|
DESCRIPTION
|
|
GDP instance up and running
|
Prerequisites: Preconfigured Oauth2 app in Guardium CLI. See instructions in the Guardium documentation.
Parameters to be shared with 1touch for integration:
• clientID
• clientSecret
• username/password of user with admin permissions (Guardium Data Protection
web UI)
|
|
Integration with ISDC
|
For connecting ISDC with GDP please follow the steps mentioned in the CHAPTER 1: INSTALLATION
|
|
Enabled and configured reporting
|
Report is an XML file generated manually in Security assessment GDP functionality.
You can configure assessment, that contains a lot or all CVEs GDP knows about.
After running it, a user can click, view results, export those results as an XML and upload the XML into Integration Extension API.
This will generate a DPS topic message, containing aggregated assessment results and all the info on the data source, if there are policies or S-TAP associated with it.
To transfer info on data sources from GDP to ISDC:
1. On GDP side, configure and export an XML report on data sources.
2. In integration API UI, upload the xml report and execute POST/parse_xml_report.
|
|
Data source analysis by ISDC
|
Run the data source analysis in the ISDC Data Source Catalog (CM > Inventory >Data source catalog).
|
Workflow to achieve the reporting part mentioned in the above Box
1. Log into IBM GDP. Go to Harden > Vulnerability Assessment > Assessment Builder.
 Fig 1: Assessment Builder
Fig 1: Assessment Builder
2. Create a new assessment.
 Fig 2: Assessment creation
Fig 2: Assessment creation
3. In Security Assessment Builder, enter the new assessment description. Then click Add Datasource or Add Datasource Group.

Fig 3: Adding data sources
4. In the Datasource Finder, add the data sources that must be assessed and later exported into ISDC dashboards.

Fig 4: Data source finder
5. You can add all available data sources in a bulk by clicking Add Data source Group.
6. Once all data sources are added, click Apply.

Fig 5: Applying data sources
7. After applying the assessment, click Configure Tests.

Fig 6: Configuring tests
8. In the Assessment Test Selections, configure tests to be run against the selected datasources.

Fig 7: Assessment test selections
9. Return to Security Assessment Finder, select your assessment from the list and run the tests by clicking Run Once Now.

Fig 8: Running tests
10.After running the tests, click View Results.

Fig 9: Viewing test results
11.A popup with assessment results will open. These results in XML format must be imported to ISDC Dashboards.
12.Click Download XML and select Export as AXIS/SCAP xml. The file will be downloaded according to your browser settings.

Fig 10: Report export
13.Open the Integration API endpoint via link: https://<cm_hostname>/integration/guardium-data-protection/docs.
14.Find the Parse XML request report and click Try it now.

Fig 11: Report parsing
15.Upload the XML report file by clicking Choose file and then Execute.

Fig 12: Report upload
16.After request is done, you'll see the JSON representation of XML report. The data has been moved to ISDC kafka.

Fig 13: JSON representation of XML report
17. Use Case Summary:
This integration supports proactive data security by providing real-time insights into vulnerabilities associated with diverse data sources.
Security teams can achieve:
-
-
Centralized Risk Assessment: Aggregate and analyze vulnerabilities across all monitored databases and data sources in a single dashboard.
-
Compliance Enforcement: Streamline adherence to regulations like GDPR, HIPAA, and PCI-DSS by identifying and mitigating risks in sensitive data repositories.
-
Enhanced Auditability: Maintain detailed records of vulnerabilities and actions taken for compliance audits.
This use case ultimately helps enterprises strengthen their data protection strategies while optimizing operational efficiencies.
Chapter 3: - Troubleshooting Tips
1. For Checking the error logs of a specific pod
2. Troubleshooting Pod Status Errors for guardium-data-protection-app
Example 1:- Pod Status: guardium-data-protection-app showing Init:ImagePullBackOff
The above error suggests an issue with the image or init image value in the values-test.yaml file.
Steps to resolve:
cd /home/admin/guardium-data-protection
sudo vi values-test.yaml

Example 2:- Pod Status: guardium-data-protection-app showing Init:CreateContainerConfigError
To resolve the above error, please verify that the values in the ConfigMaps (CMs) and Secrets are consistent with those shown in the screenshot below.

Example 3:- Pod Status: guardium-data-protection-app showing CrashLoopBackOff
APP_PORT value is not a valid integer (type=type_error.integer)
KAFKA_PORT value is not a valid integer (type=type_error.integer)
To resolve this issue:
-
-
Navigate to the directory:
cd /home/admin/guardium-data-protection
-
-
Edit the values-test.yaml file:
sudo vi values-test.yaml
-
Important Commands which you can execute to identify multiple other issues related to any pod:-
kubectl -n dc-engine exec -it <podname> -- printenv| grep GUARDIUM
This command is typically used to:
It's useful for checking configuration values like GUARDIUM service URLs, ports, credentials, or other settings that are passed as environment variables.
kubectl -n <namespace> get cm
Usage:
-
-
-
This command retrieves a list of ConfigMaps (cm) in the namespace.
-
ConfigMaps are used to store non-confidential configuration data as key-value pairs for applications running in Kubernetes.
-
Example usage: You can use this to see all the configuration settings for applications in the dc-engine namespace.
kubectl -n <namespace> get secrets
Usage:
-
-
-
This command retrieves a list of Secrets in the namespace.
-
Secrets are used to store sensitive data, such as passwords, tokens, or keys, securely in Kubernetes.
-
Example usage: You can use this to view the names of Secrets available in the dc-engine namespace, which might be used to manage secure access for applications.
helm -n <namespace> delete guardium-data-protection helm -n <yournamespace> upgrade --install guardium-data-protection . --values values-test.yaml
Usage:
-
-
- To remove a specific package, you can run the above command.
Note: It is recommended to run this command after modifying any values in the values-test.yaml file. Once the changes are made, executed the second command to reinstall or the package:
Summary:
This tutorial provides a comprehensive guide for integrating the IBM Security Discovery & Classify (ISDC) with the Guardium Data Protection (GDP) package. It covers the installation of the GDP package, detailed configuration steps for seamless integration, and instructions for sending Vulnerability Assessment (VA) reports from GDP to ISDC. Additionally, the tutorial includes troubleshooting strategies for common pod status errors related to the guardium-data-protection-app and a list of essential Kafka commands beneficial for managing and monitoring the integration. By following this tutorial, users will acquire the knowledge and skills necessary for an effective and efficient data protection setup.
"Special thanks to @Sudhagar Tiroucamou for reviewing and supporting the publication of this blog."