Hello QRadar Community!
In this article, let's take a critical look at Windows User Account Control (UAC), some common attack types used to bypass this control mechanism, and some detection methods we can use to detect common UAC bypasses.
We'll go over a number of attack methods at a high level, but don't worry about having to implement detection rules for these all on your own. Adding detection coverage for the UAC Bypass methods detailed below can be as easy as installing a content pack. Version 2.4.0 of the IBM QRadar Endpoint Content Pack - to be released shortly - adds a collection of rules and building blocks that detect all of these attack methods and more.
What is Windows UAC?
Consider the use of administrator privileges in Microsoft Windows. While some users of a Windows machine may need elevated privileges to perform their regular tasks, granting them sweeping privileges all the time is a dangerous proposition. In an attempt to solve this dilemma, Microsoft implemented an elevation control mechanism that allows authorized users to elevate privileges temporarily for specific tasks. As anyone who’s done administrative tasks in Windows since the days of Vista will know, part of this process is a request for consent from an administrator that manifests in the form of a popup window. This control system is known as User Account Control - UAC for short.
This system generally requires explicit consent from a user, otherwise any code running in the context of an authorized user could arbitrarily and silently elevate its own privileges (remember this, as it will come up again later). Additionally, for obvious reasons, the consenting party must also be part of the Administrator group; only a user authorized to have elevated privileges can grant elevated privileges.
Privilege Escalation and Bypassing UAC
To examine how attackers can bypass this control system, it’s important to understand the limits that Microsoft has placed on it. After debuting UAC in Windows Vista, it quickly became apparent that many of Microsoft’s own trusted binaries were producing a significant and sometimes annoying level of UAC prompts. This was dialled back in subsequent releases of the operating system by allowing some trusted Microsoft programs to auto-elevate their privileges without a consent prompt.
Another thing to note about Windows is that when processes are created, they can inherit permissions from their parent process. What this means is that if an attacker obtains access to a user account in the Administrator group and can get one of Microsoft’s auto-elevating programs to run malicious code or spawn new processes, the attacker can execute any program of their choosing with Administrator rights without triggering this UAC prompt.
As it happens, there are many known methods by which attackers can get their code running using these auto-elevated processes. MITRE has this collection of techniques indexed as T1548.002, and UAC bypass methods have been used in the wild by numerous malware families for silent privilege escalation.
The UACMe Project contains a large collection of known UAC bypasses, containing over 70 methods of silently obtaining elevated privileges. Microsoft has since patched many of these, but dozens remain exploitable even in the newest versions of Windows 10 and Server 2019.
Some common methods of exploiting these auto-elevating programs include:
- DLL Search Order Hijacking: Malicious DLLs are implanted to a location early in the DLL search order (often the system directory) with the same name as a legitimate DLL. When an auto-elevating program executes and attempts to load the legitimate DLL, the malicious DLL is loaded instead, and takes over the process when one of its functions is called.
- Shell Handlers: Commands or programs can be registered to these auto-elevating programs in the registry as shell extensions, which can then be executed whenever the program runs.
- Environment Variable Manipulation: By altering environment variables like WINDIR or COR_PROFILER, paths to legitimate images used by these auto-elevating programs can be redirected to malicious images.
- System Directory Mocking: This method attacks the means by which Windows determines if a program can safely auto-elevate. By tricking the system into believing that an image is being loaded from a safe location using flaws in the directory validation mechanism, malicious code can be loaded into auto-elevating processes from unsafe locations on disk.
So, knowing these flaws exist, how easy is it to abuse Windows UAC?
Many of these attacks are relatively simple: modifying a few registry keys, crafting a malicious DLL and dropping it to a specific location on disk, etc. In fact, there are a number of GitHub repositories where researchers have shown that a PowerShell script of only a few lines can open a shell with administrator privileges while entirely bypassing the UAC system. You can see this in action below:
How to Detect UAC Bypass Behaviour
As previously mentioned, silent privilege escalation using known UAC bypass techniques is used by several malware families to obtain the required permissions to execute their payloads; therefor, the ability to detect these privilege escalation methods is another avenue through which a lot of these malware can be caught.
So, what tools can we use? SysInternal’s Sysmon is a good start. Properly configured, this tool can detect file creation, process creation, registry modification, loading of DLLs, and much more. By monitoring registry keys, processes, and file locations associated with known UAC bypass techniques, Sysmon can collect logs generated by UAC Bypass attempts.
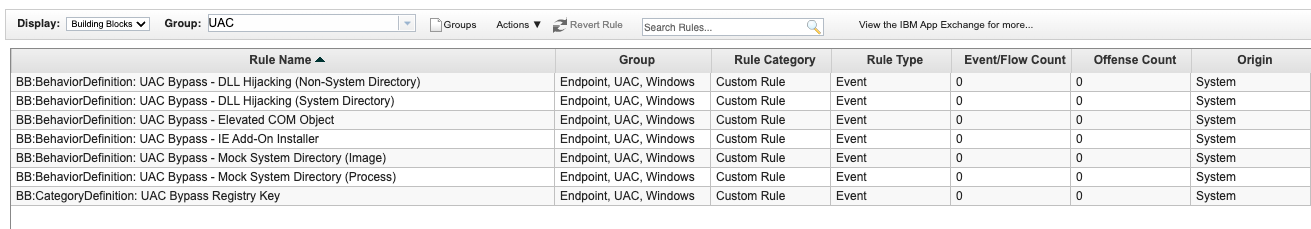
With these logs, analysis and detection rules can be implemented in QRadar by focusing on the behaviours listed above. We can watch for the addition of shell handlers to certain registry keys, the placement of unsigned images in the system directory, the modification of specific environment variables by non-elevated processes, and much more. Here is a sample of the detection coverage included in IBM QRadar Endpoint Content Pack version 2.4.0:
Don't feel you need to wait though; version 2.3.0 of the IBM QRadar Endpoint Content Pack, which provides detection for numerous other attack methods in Windows and Linux, is currently available here. Keep an eye on the app exchange for more info!