Security vendor stories are blurring together, particularly within the identity and access management space. Whether it’s identity as the new perimeter, providing the right access to the right users at the right time, wrapping context around every transaction or the age-old balance of security and user experience, these stories and claims can feel a bit empty on their own. Most security and IT stakeholders agree by now that the principles behind zero trust are important, from “least privilege” and “assume breach” to “never trust, always verify,” so how do they actually get implemented? When wrapping context around every transaction, are vendors’ capabilities deep enough? Or is “contextual access” a convenient marketing message to fit into the current security landscape, falling short when the technical details surface? Context is good, but protection is better—is your IAM vendor’s context deep enough to really make a zero trust program successful?
The good and bad of additional authentication
With compromised credentials still the top initial attack vector for data breaches in 2021, the need behind multifactor authentication (MFA) seems clear. An extra layer of security can protect against stolen credentials, whether an SMS code, a mobile push notification, fingerprint scan, or hard key. Certain MFA methods have proven to be more secure than others, and dated methods like knowledge-based questions are not preferred as they can easily be guessed or otherwise looked up. Is your mother’s maiden name or the street you grew up on really as secure as your fingerprint?
Moving on from knowledge-based questions is not a groundbreaking recommendation. More concerning is the false sense of security generated by other commonly adopted MFA methods that are assumed to be more secure, like SMS one-time passcodes. Between device spoofing, malware attacks, social engineering, session hijacking, and SIM swaps, this intended extra layer of security starts to seem a little less secure as methods to circumvent MFA abound.
On the other hand, MFA can also be intrusive and often unwelcome friction for both employees and consumers that are simply trying to access their everyday accounts. Our patience as consumers in particular is as low as ever. In fact, 40% of consumers have recently given up on an online purchase, application, or transaction based on negative experiences logging in, signing up, or completing a payment.
So, MFA isn’t perfect. And it can also get in the way. To help, organizations have been adopting risk-based authentication (RBA) and adaptive access strategies that check additional vectors of context, calculate risk scores, and only prompt for MFA when deemed necessary.
Adaptive access seems to be the answer. What’s the catch?
The theory behind adaptive access makes complete sense, but many organizations have yet to implement it. Some vendors may also mention that “contextual access” or other adaptive access synonyms (adaptive authentication, adaptive MFA, conditional access, etc.) are included within their solutions already, but not all context is treated equal.
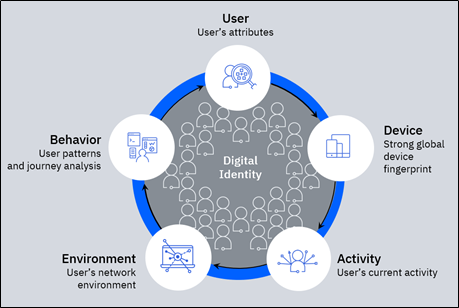
Let’s look at device context, which evaluates device footprint for risk. Most vendors would check basic, static context like whether a user has used the same device in the past, if the device is jailbroken, or if it’s being managed by an organization’s existing security policies. Or behavior context, like whether the time of day logging in is typical for an individual.
IBM Security goes deeper in each case, knowing there’s more to the story. As device malware evolves, IBM has a team that focuses on reverse engineering it. Risk signals can also detect virtual machines, emulators, device spoofing, and remote access trojans. And while basic behavioral anomalies are important to check, IBM’s behavioral biometrics go deeper to look at how users move their mouse, how they interact with their keyboard and how they interact with their mobile device, to help uncover unauthorized usage. Is the user holding their mobile phone at a new angle, moving their mouse erratically, or cutting and pasting their credentials instead of typing them? Context matters.
When evaluating an adaptive access implementation, you can ask yourself some foundational questions:
- When a user is prompted for MFA, do I fully understand why?
- Are there gray areas in which MFA might be overly used now, in which other background risk signals could fulfill authentication needs?
- How confident am I in protection against more advanced forms of account takeover?
Infuse risk confidence into IAM systems to deliver smarter authentication.
IBM Security Verify Trust provides deep risk assessment to IAM systems, covertly analyzing context behind every transaction to help achieve zero trust design principles. Based on the IBM Security Trusteer risk engine, Verify Trust helps to protect against malicious actors while balancing MFA requirements. Recognized as a leader in the RBA space, IBM helps you:
- Build on existing IAM investments. Integrate with your IAM system, vendor agnostic and through any deployment method, to configure RBA and adaptive access without starting from scratch. Current single sign-on and MFA implementations can adopt a deeper risk engine behind the scenes to make them more effective.
- Deepen trust. Holistic risk context evaluated using AI and machine learning across device, network and behavior parameters helps provide more secure authentication. Anomaly detection, fraudulent patterns and consortium data combine to maximize risk identification and keep protections up to date alongside evolving threats.
- Reduce MFA rate. Higher confidence in risk detection helps to limit false positives and unwarranted MFA prompts, providing smoother experiences for both consumers and remote workers that help improve satisfaction and brand health while also condensing OpEx.
The business value of trust
With deeper risk context verified for each transaction, there is less need for prompting MFA in uncertain gray areas where a challenge is used “just in case.” Businesses should consider the value of a happy, uninterrupted user. It’s hard to say exactly how many users would get frustrated and leave a brand if they received one additional, unnecessary SMS one-time passcode and the exact effect to the bottom line. Authentication is only a one part of larger consumer identity and access management (CIAM) strategies that aim to deliver personalized, on-demand, and repeatable experiences between consumers and brands. But CIAM strategies do bring tangible benefits to organizations when implemented holistically toward their desired business outcomes. In a recent EMA survey, organizations that implemented CIAM programs saw on average a 27% increase in sales conversions and a 16% increase in visitor registrations or logins. While MFA and adaptive access are only a part of the full strategy, 58% of those same EMA survey respondents indicated that “identifying users with malicious intent” was the hardest part of CIAM administration.
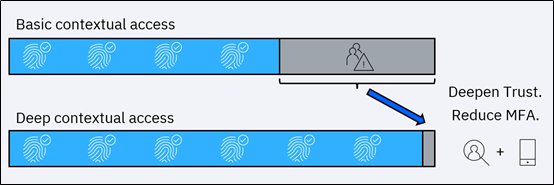
One IBM client in the financial services space recently improved its digital experience across mobile and online channels by integrating Verify Trust into their existing IAM environment. They were experiencing a 30% MFA rate based on limited context checking and were feeling pressure from the business to heavily reduce this friction, while accommodating numerous authentication journeys based on user profile. By implementing Verify Trust, they decreased MFA rate from 30% to 2% for all sessions, while enhancing their security protection along the way. This improvement not only provides a more streamlined experience for customers but reduces MFA-related expenses as well.
The Trusteer risk engine that powers Verify Trust protects over 120 million mobile devices and processes 70 billion data events every month. With over 500 customers worldwide, IBM’s cloud-based risk engine is closely maintained by a dedicated team of fraud and identity experts.
Industry analysts too have seen the value in the depth of IBM’s risk-based authentication capabilities. The 2021 Quadrant Knowledge Solutions Spark Matrix for RBA report names IBM as a leader, detailing its wide inspection of identity risks and robust feature set.
See the Verify Trust product page to check out a demo and read more about IBM’s recent analyst recognition in the RBA space.