Table Of Contents
User Enrollment for iOS has piqued the interest of security minded UEM admins since the day it was announced as a feature in iOS 13. There are a lot of moving parts to the User Enrollment (UE for brevity from here on) feature, so we wanted to take some time to outline implementation, deployment, and management of UE devices in MaaS360.
Let's get started!
Pre-requisites and Configuration of Deployment Settings
Core Prerequisites:
Access to an Apple Business Managed (ABM) or Apple School Manager (ASM) portal.
Devices running iOS 13+
APNSWhile UE may be a streamlined and not nearly as invasive as standard iOS MDM (Supervised or not), it still has its roots planted firmly in many of the same backend features. First and foremost an APNS certificate is required (this is not something that can be deployed to supplement our non-MDM enabled "Standalone Secure Productivity Suite" clients). Users will still install a profile on the device, thought the workflows vary a bit (more on that shortly).
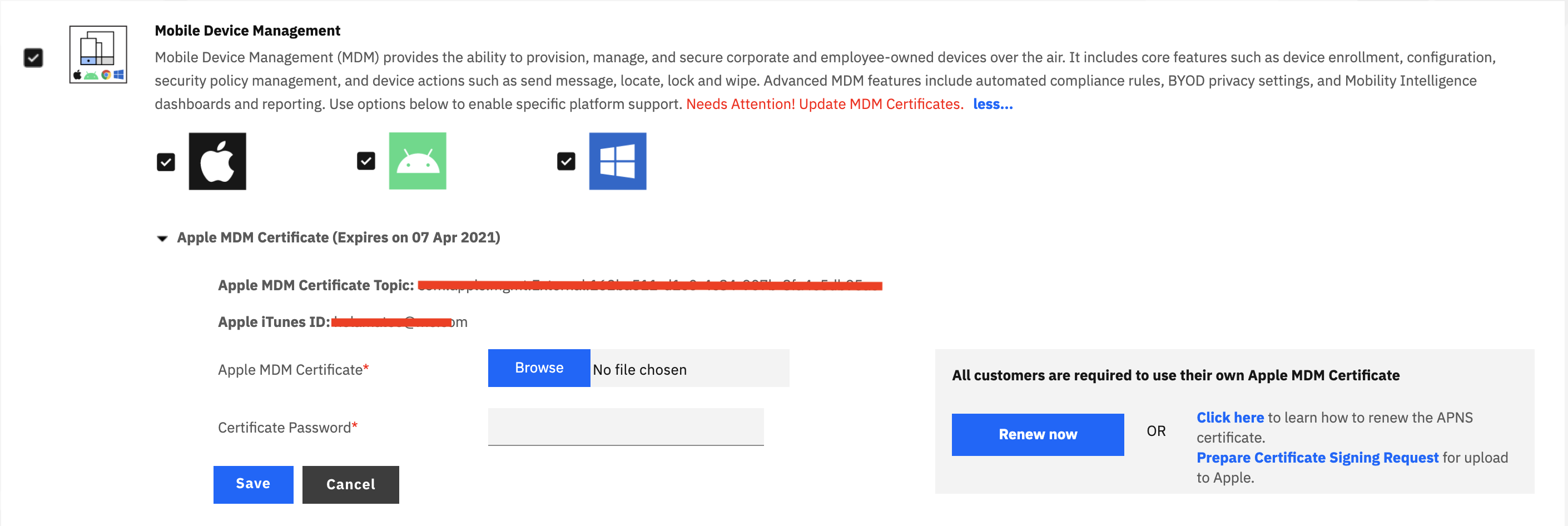
That's the easy part of the setup. The more difficult part, if not already in place, comes in the Apple Business/School Manager portal, more specifically the user record. In order for devices to enroll properly in the user enrollment setup, they require a component called:
Managed Apple ID
The Managed Apple ID is created in the ABM/ASM portal and added to the user record in MaaS360.
This can be done on new and existing users (for more information on managing users in the ABM/ASM portals, please refer to Apple documentation).
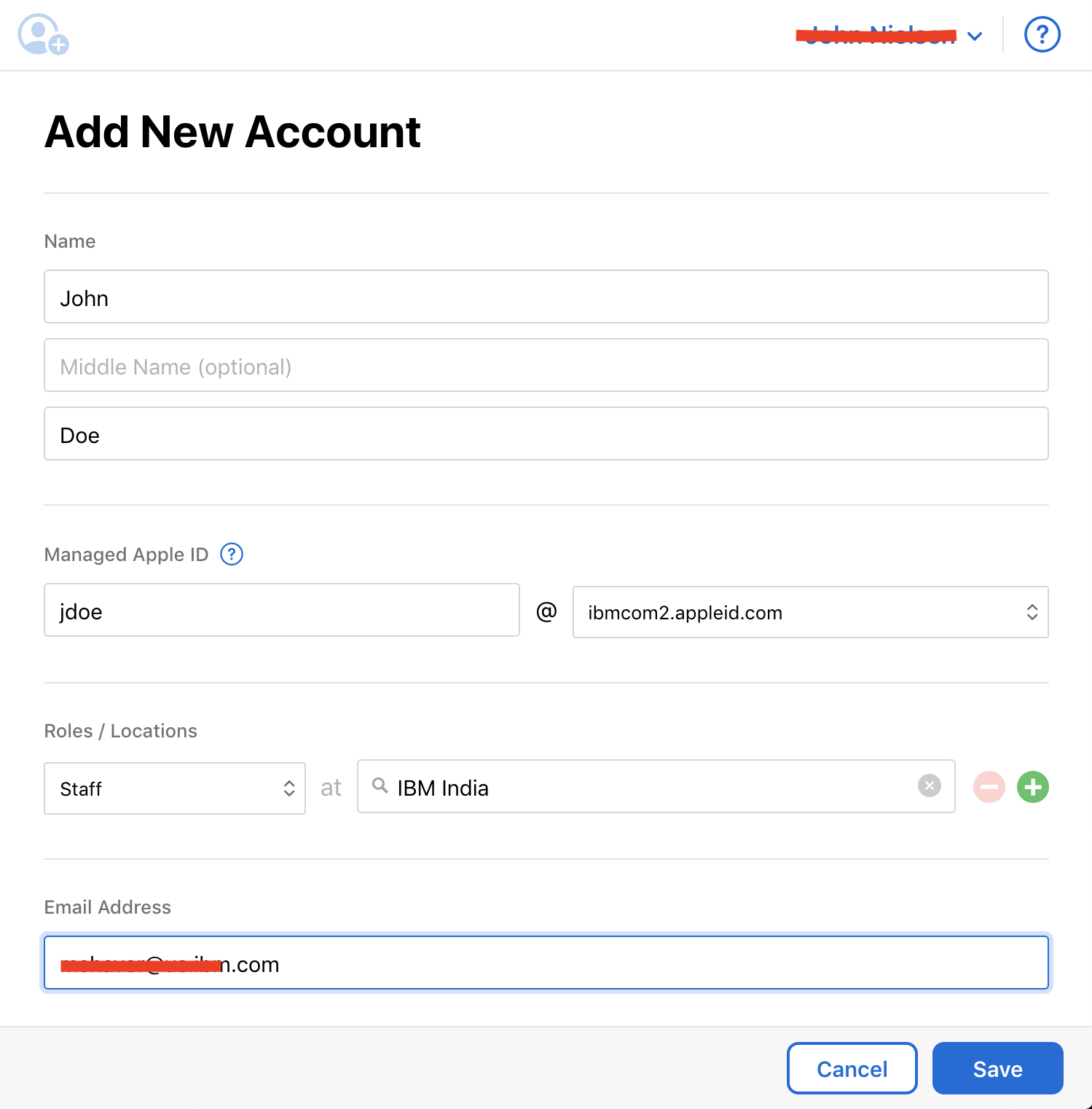
Bulk IDs may be created for all users at once by selecting the full user set in the directory screen of ABM

Then on the left hand pane, select Edit for Accounts.
Admins will be able to select the format for the Apple IDs and auto-generate them for every user.
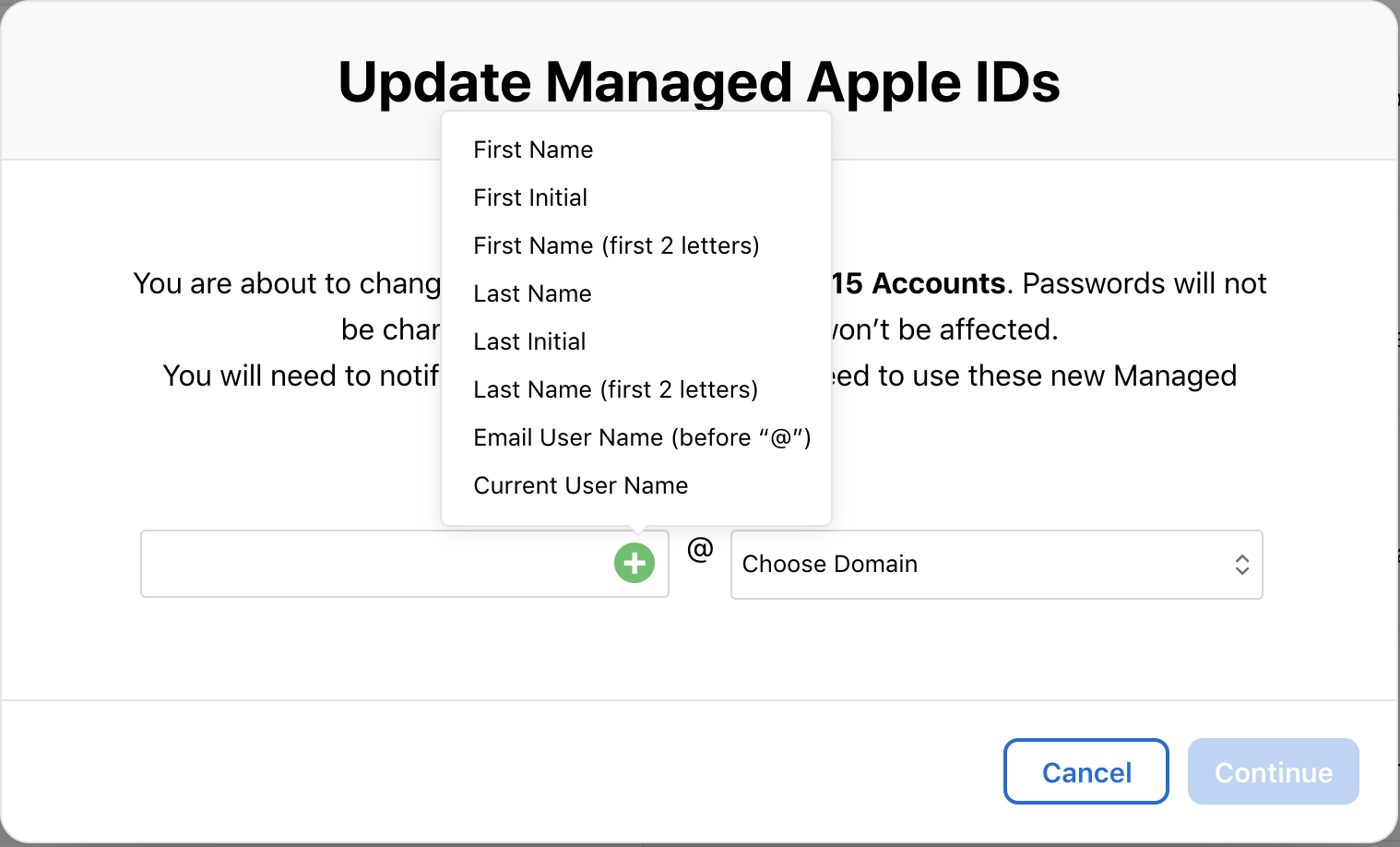
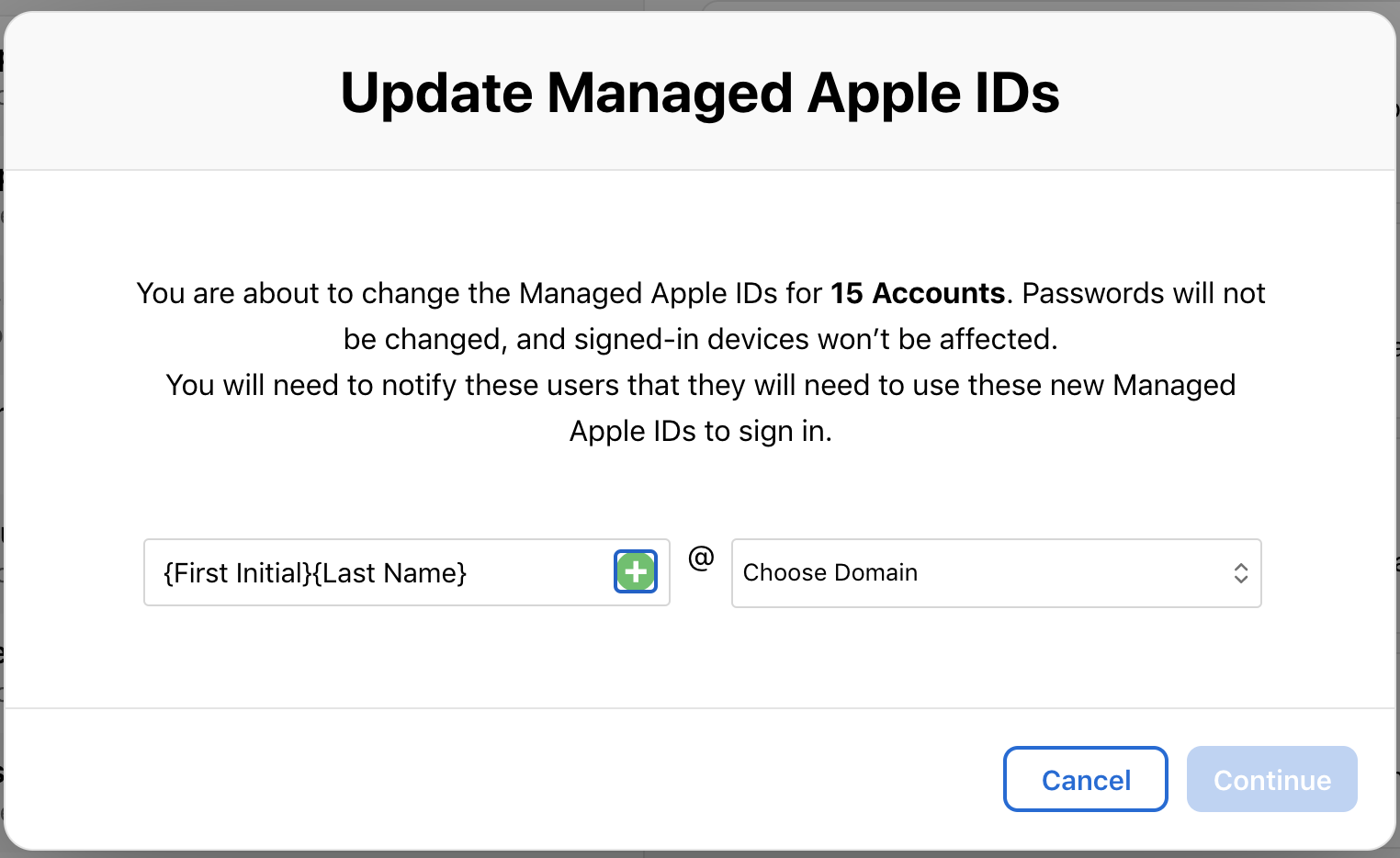
After the Managed Apple ID is created, it must be "activated" by the end user. First, the admin must generate a sign in - either in the individual user record or in bulk in the same screen as the bulk ID creation.
Admins will have the option of generating a spreadsheet with credentials for sharing or emailing users directly.
Sample email:
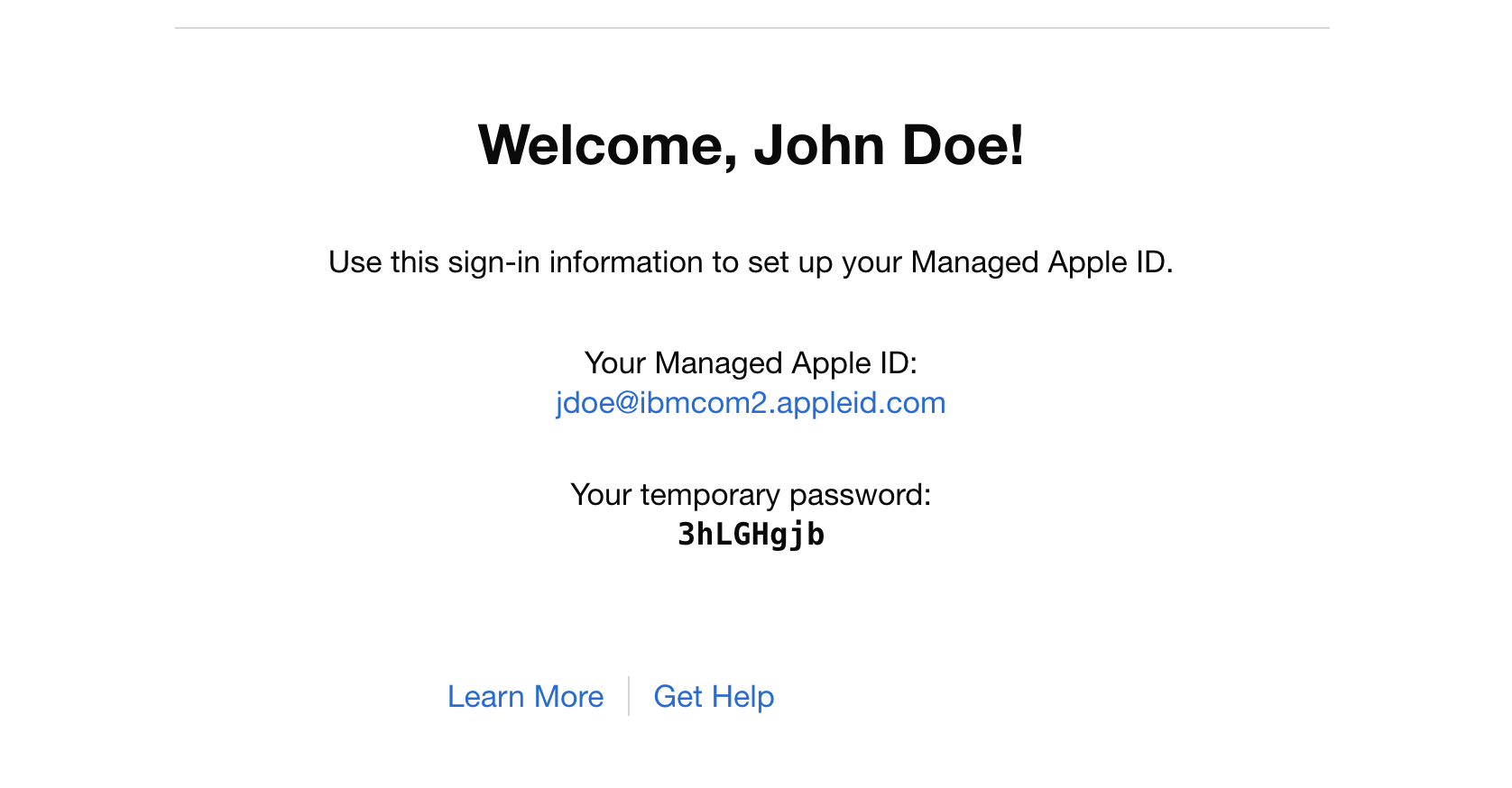
Users may then navigate to https://appleid.apple.com where they may login with the temporary credentials and then set their password. Two-factor authentication is on by default for managed Apple IDs (and may not be disabled by the user) so there will be a phone number prompt as well. Once these steps are complete, the Managed Apple ID is ready for use with relevant services.
MaaS360 User Records
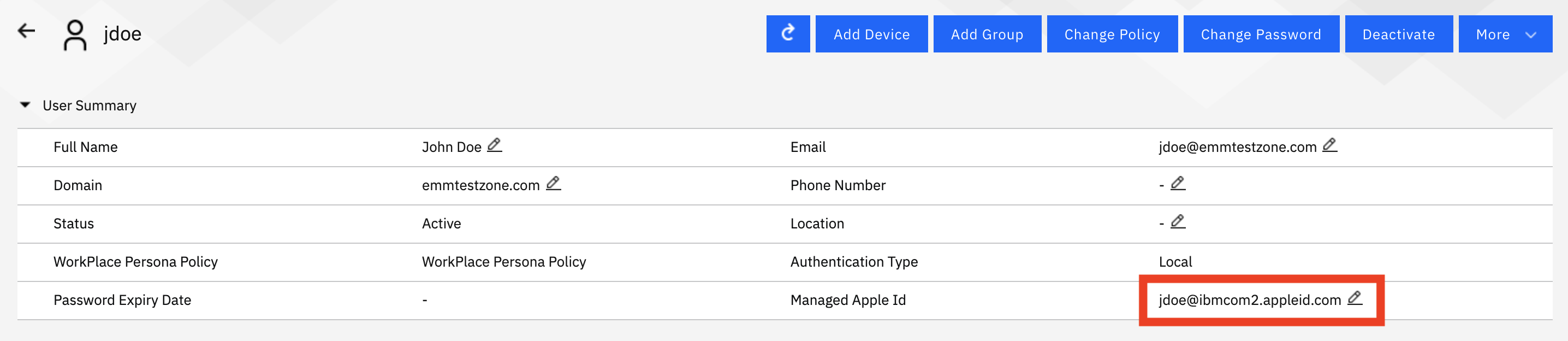
Now that the IDs are sorted out, they must be associated with the proper user record in MaaS360. Currently this is a manual action in the user record for ABM portals (ASM client portals can have the fields imported automatically). Bulk import functionality for ABM clients will be available in the near future (I'll update this blog to reflect the workflows when it is).
Local Users - Manually enter the information by clicking the pencil icon next to the field
AD/LDAP Users - This field must be manually edited in the portal for now (this can be done in bulk via spreadsheet). In the near future we will offer syncing capabilities within the Cloud Extender tool itself.
Important Note: The MaaS360 user record information doesn't need to match the Apple portal word-for-word by any means. The important field is the Managed Apple ID, so just ensure that they're assigned to the proper users, the rest of the information is only really pertinent to MaaS360 functionality and enrollment.
Deployment Settings
The APNS cert is valid, user records are set, the Managed Apple IDs are created, and the users have their devices on iOS 13+. Now it's time to setup enrollment. The handling of user enrollments for our initial release is an all-or-nothing setting for devices marked as "Employee" owned, whether by an admin sending an enrollment request, or the user selecting the ownership during enrollment.
Navigate to Setup-->Settings-->Device Enrollment Settings-->Advanced and find the section titled Advanced Management for Apple Devices.
The final option in this section is for user enrollment settings - either MDM or User enrollment can be selected.
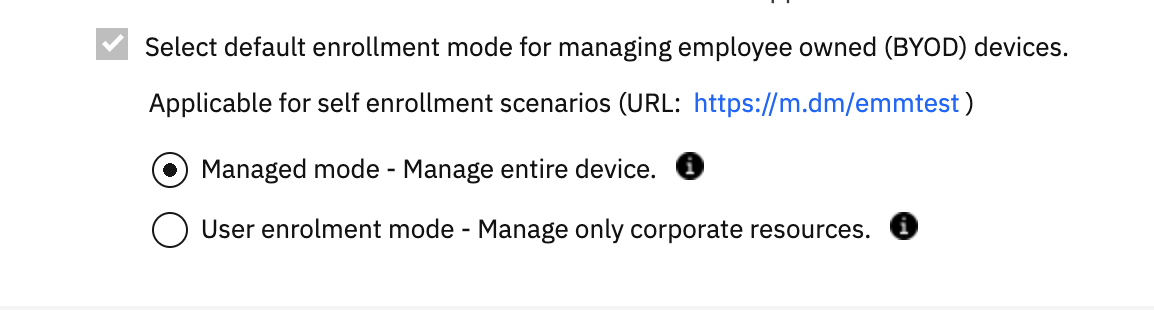
There are a couple of caveats for these settings that require attention-getting BIG RED TEXT!
First - macOS MDM enrollments will not function properly for devices tagged as Employee owned while UE enrollment is set. They will need to be enrolled as corporate, corporate shared, or not-defined.
Second - All iOS 13+ devices with the Employee ownership flag will attempt to enroll with UE while this is activated, whether using AD/LDAP credentials, Local User credentials, or One-Time-Passcodes.
Third - UE enrollments will not work for devices enrolled via Apple Configurator or Streamlined (DEP) enrollments. It is not intended for those workflows.
Lastly - devices that are being enrolled to users with no Managed Apple IDs listed in the user record, Managed Apple IDs that are not setup properly, or on devices with iOS versions prior to iOS 13 will be enrolled in standard MDM.
Now that everything is in place, it's time to enroll some devices!
Enrollment and Portal Features
Enrollment
Enrollment in to UE requires a couple of extra steps that haven't been seen prior to this feature. As many have noticed, Apple hasn't been shy about adding prompts to MDM enrollment on non-supervised devices so that users have a clear understanding of what they're going through. UE doesn't change that - there is still an MDM profile going on to the device - and it actually adds a few steps to the enrollment process, some of which may confuse less technical users, so we'll go through it step-by-step.
Users will authenticate against the MaaS360 URL as normal - nothing has changed here. Terms and conditions will also be the same as with all other Safari based iOS enrollments. Once the web based portion is over, that is where the changes will come in to play. The user will have to navigate to Settings on the device and tap on "Enroll In MaaS360" and the UE enrollment will take over.
Step 1: MaaS360 authentication *make sure ownership shows as "Employee."
 Profile is downloaded
Profile is downloaded
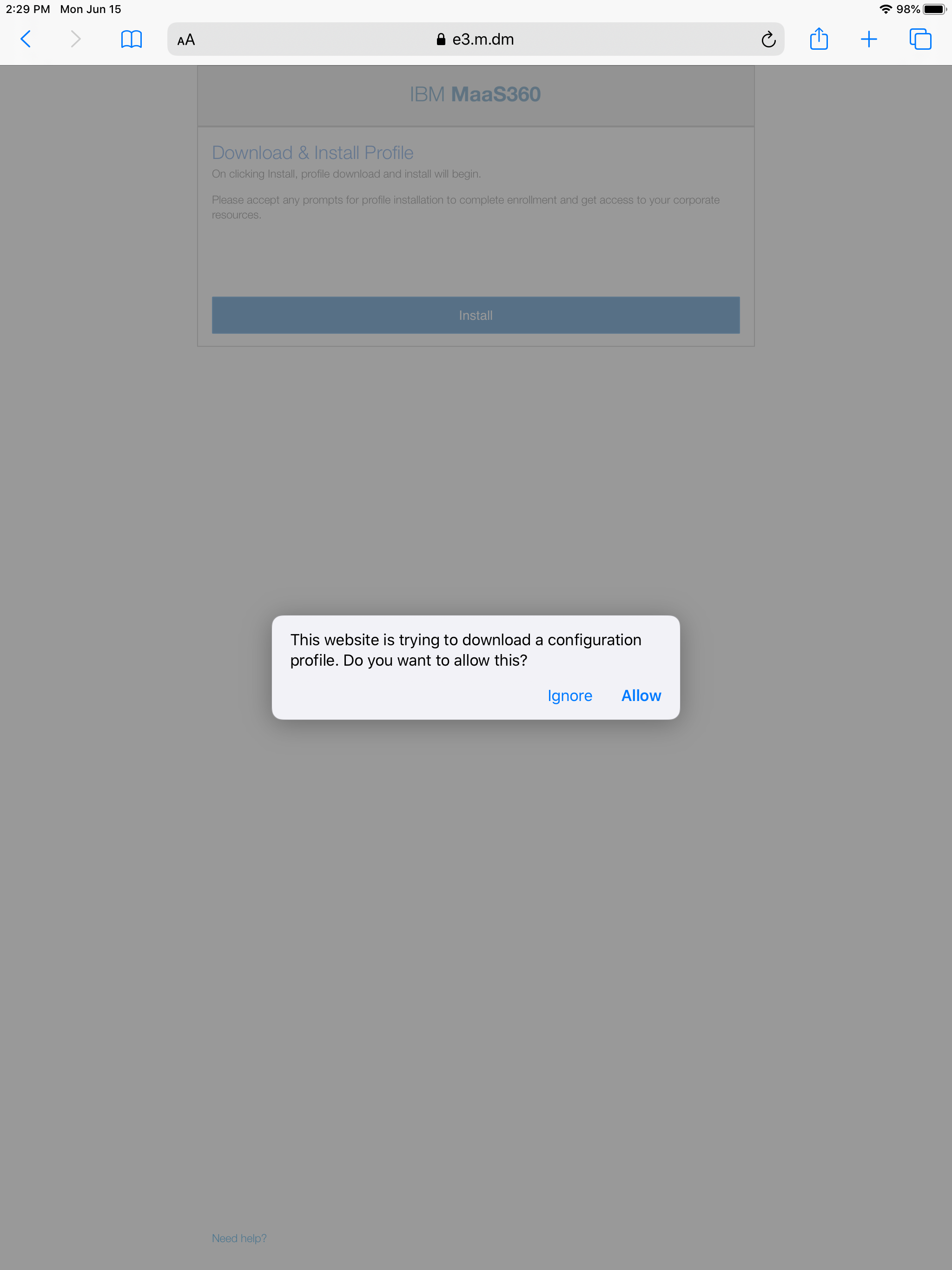
Step 2: User must navigate to "Settings" and tap on "Enroll in MaaS360"
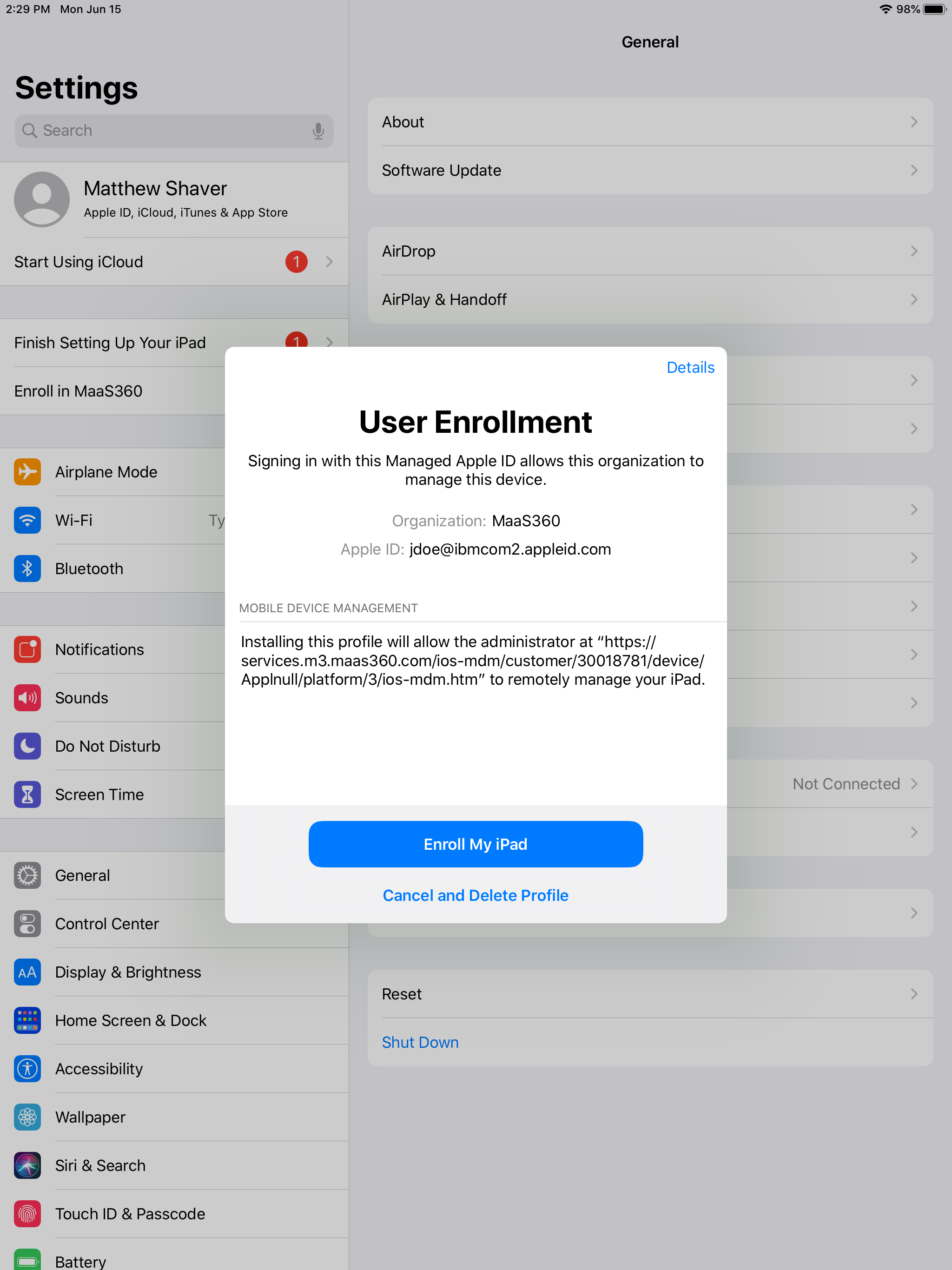
Step 3: User will be prompted to sign in with the Managed Apple ID. The username field can not be altered by the user, which is why it is important to ensure that the user record contains the proper ID. 2 Factor Authentication is also enabled and can not be disabled, so the user will need their 2FA device nearby.
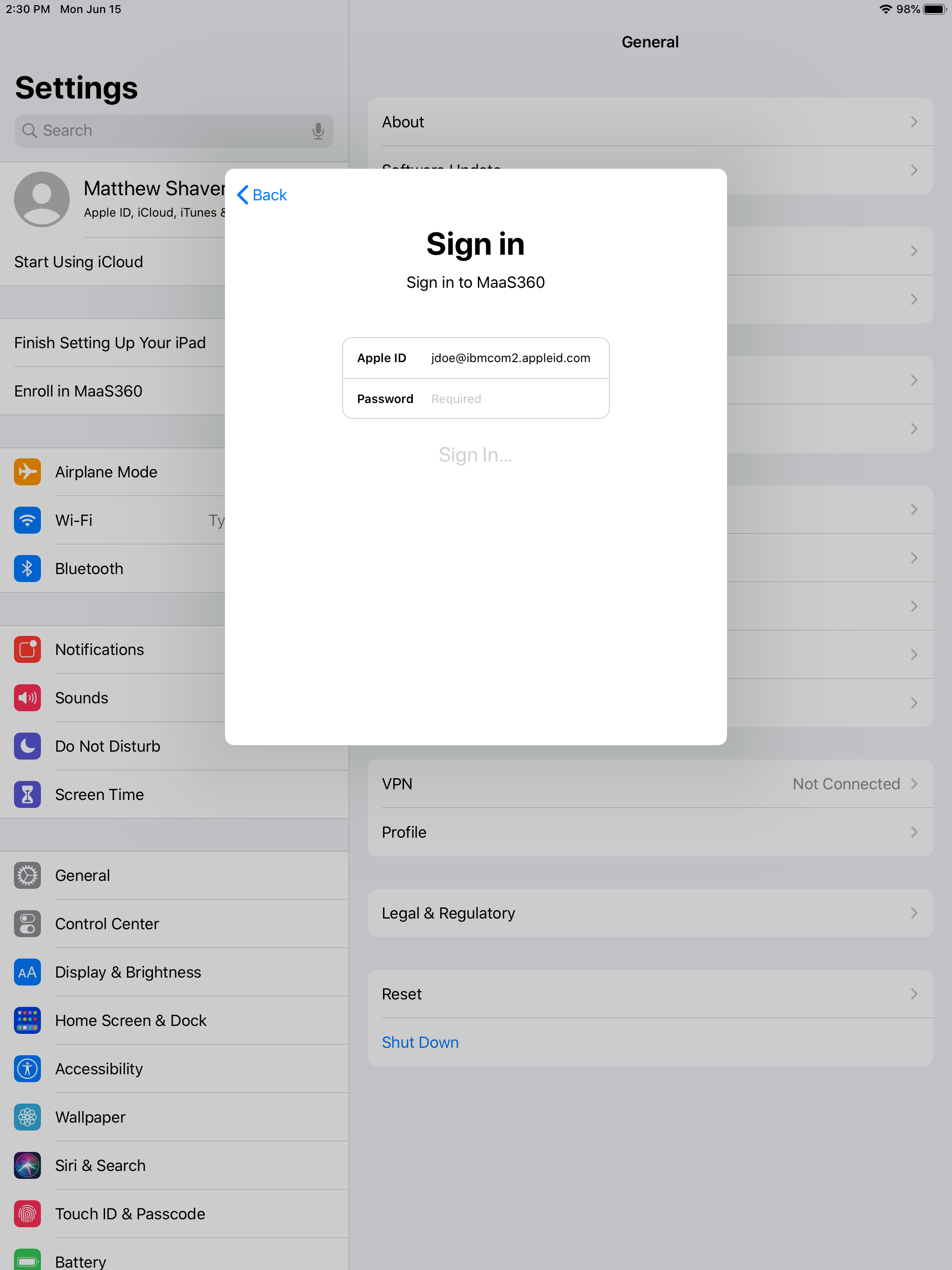
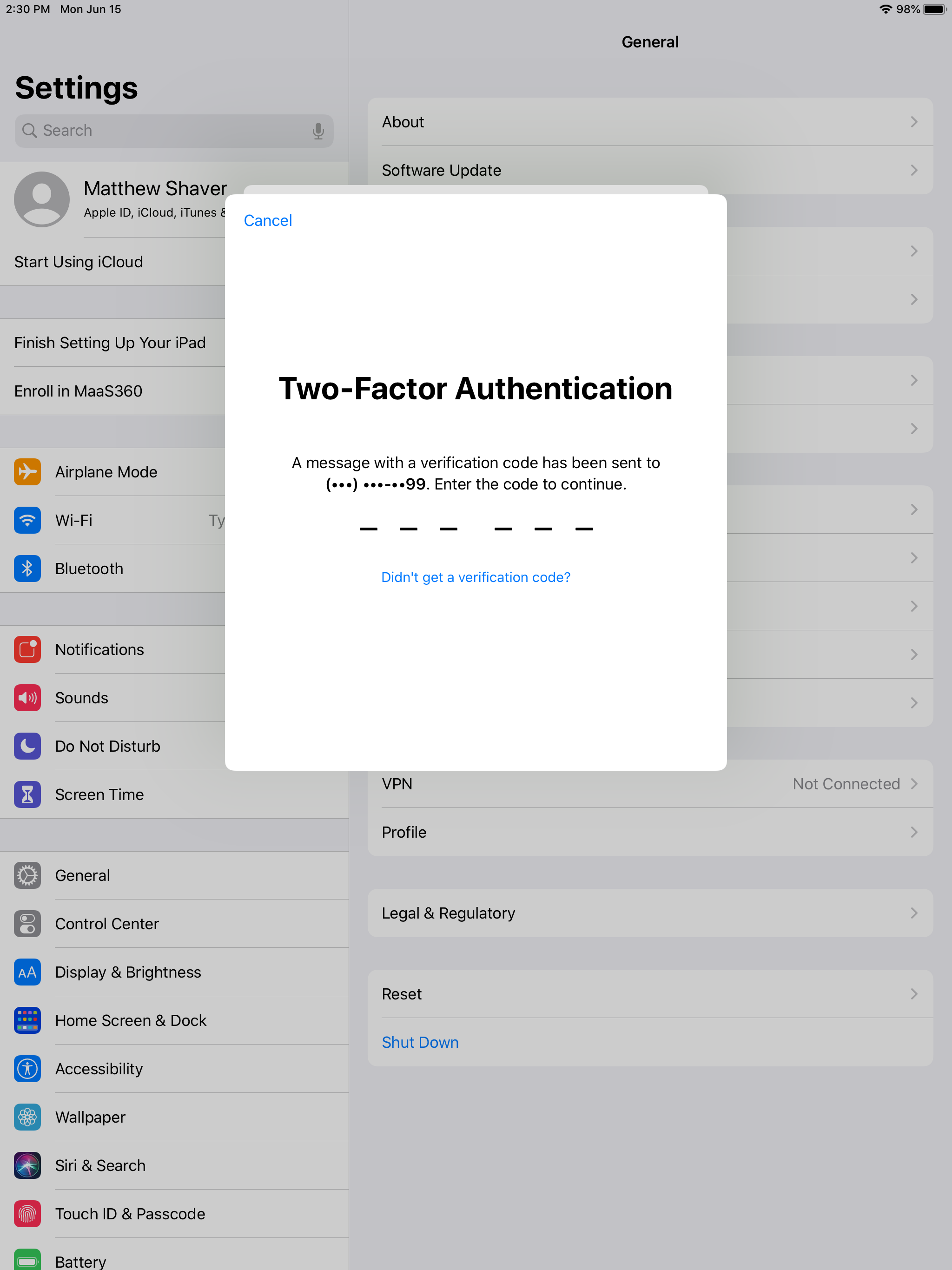
Please Note: After signing in with the Managed Apple ID, the user *may* receive a secondary prompt for an Apple ID (this will pop up in a full window, rather than the smaller Managed ID window). This is asking for their personal account. If they attempt to sign in with the Managed Apple ID again, they will receive an error.
User will now see the installed UE profile and the account will appear under Passwords and Accounts in the settings.
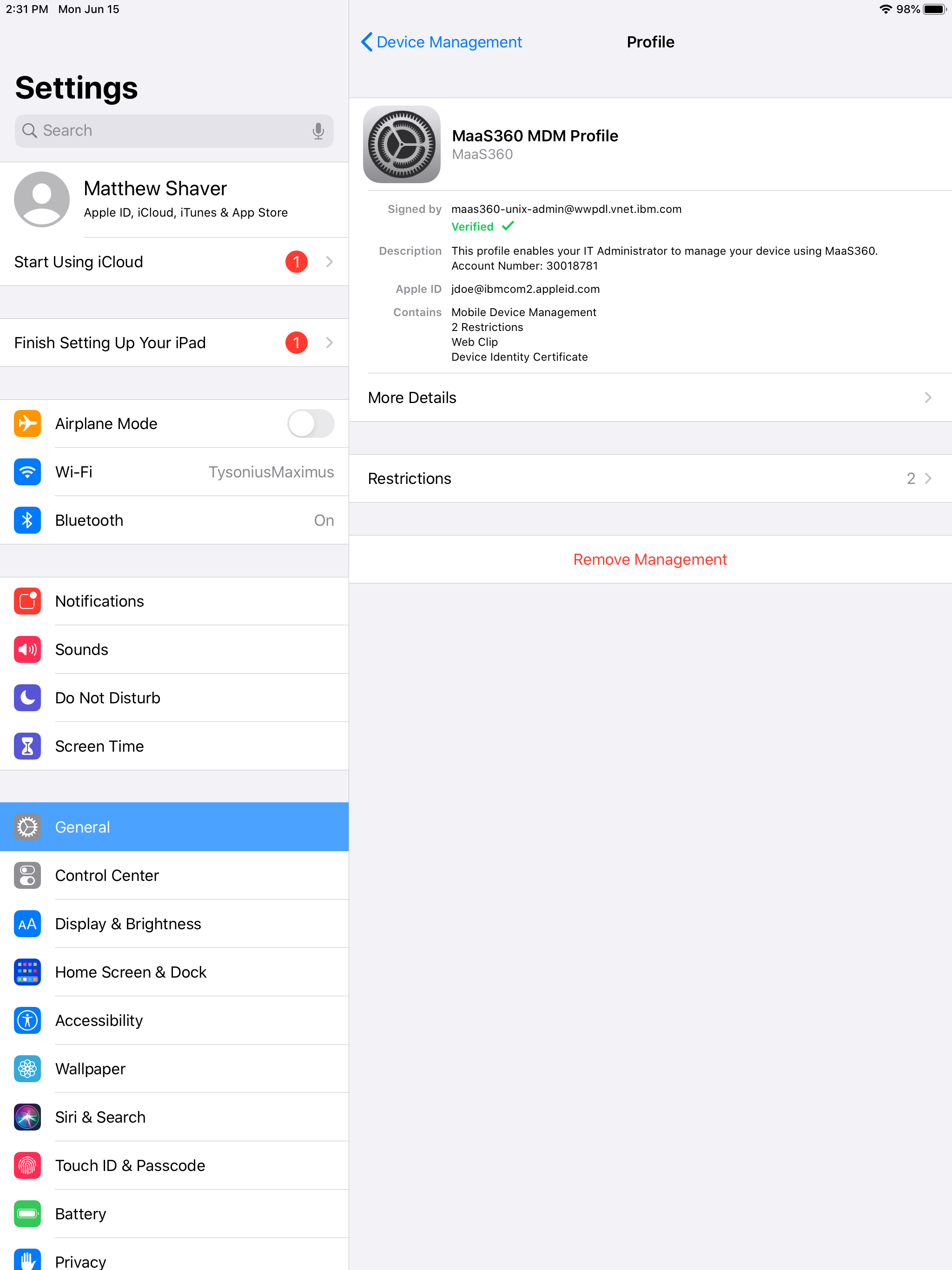
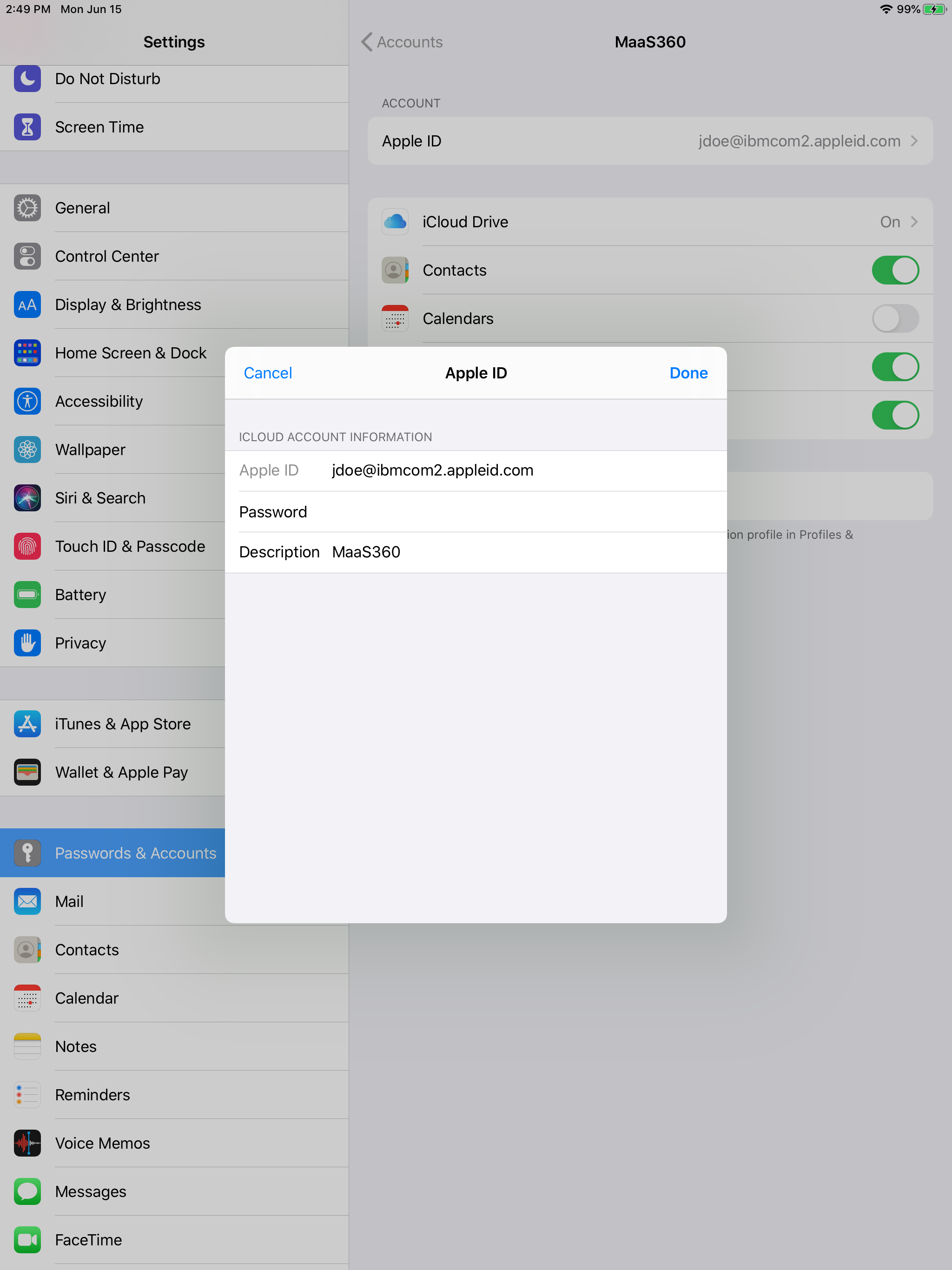
The device is now UE enrolled!
Policies and Device Actions
One of the primary initiatives of UE is to give organizations some capabilities to distribute and (lightly) secure information on personally enabled devices, whilst removing some of the more restrictive actions. UE enrollments remove many of the invasive device actions as well (such as full wipe capabilities) and reporting is also stripped down (Network settings will not appear at all, for example). None of these limitations change the way that devices are handled and policies implemented in MaaS360.
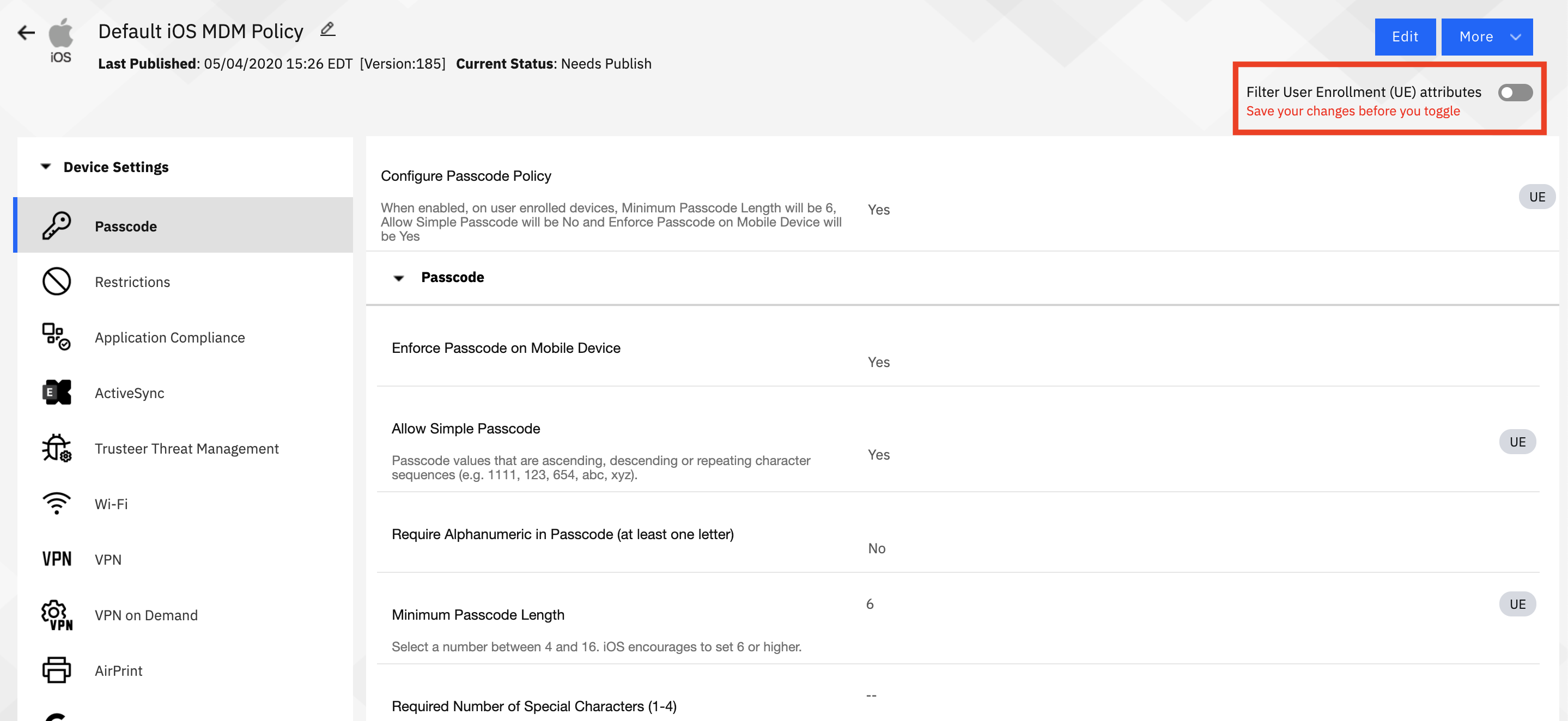
Policies themselves now contain a "UE" flag for features that are available on enrolled devices. Admins may also toggle to show only UE features (make sure to save settings before flipping that switch, as it will revert all unsaved changes to their previous setting).

Before toggle
After toggle
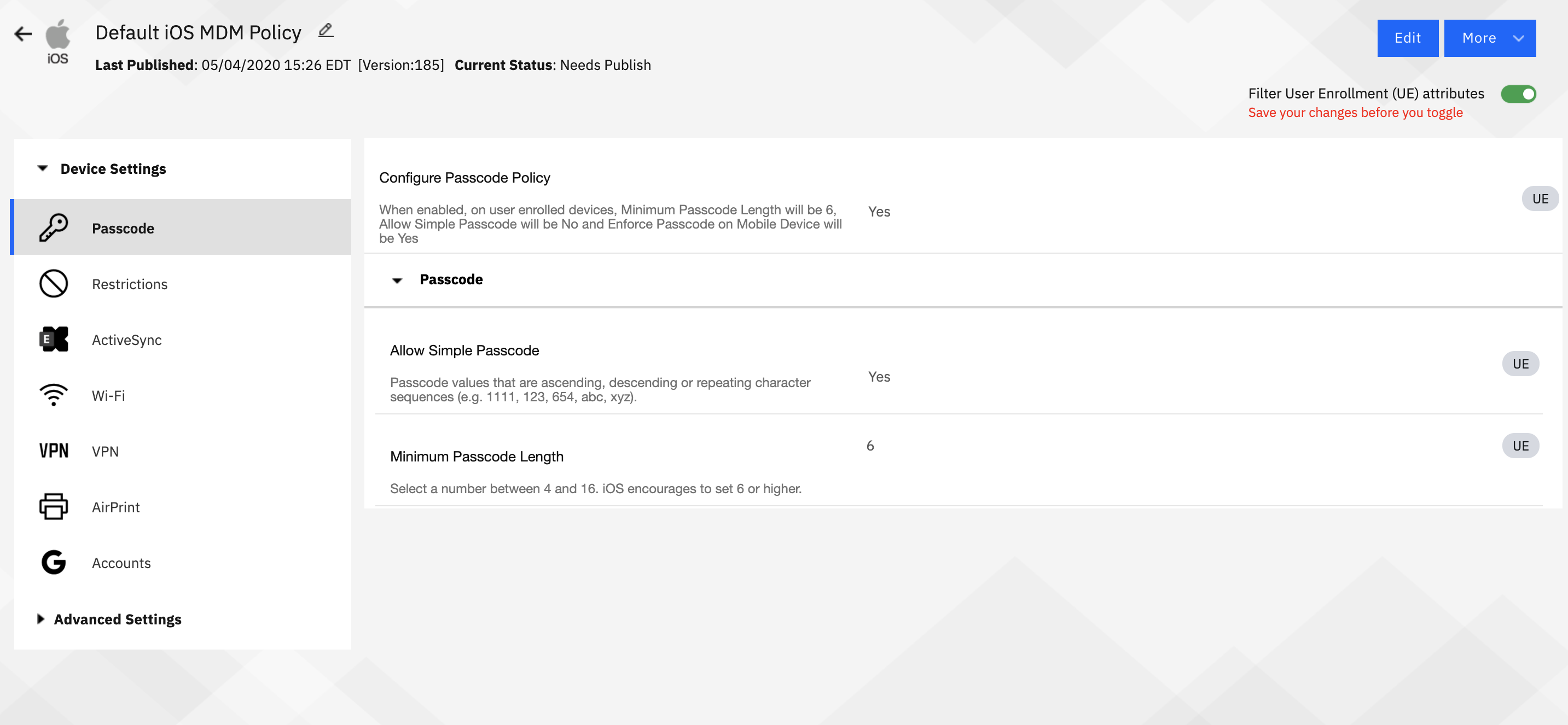
Admins will notice that when UE features are toggled, all of the Supervised settings are removed - they don't apply at all here. Many of the leftover settings are related to configuration - email, wifi, VPN, etc. There are some security related features as well, such as enforcing a device passcode, and restricting managed to unmanaged app settings.
MDM actions are limited to locking the device, selective wipe, and removing control. MaaS360 application based actions (buzz, message, locate) are not impacted by UE enrollments.
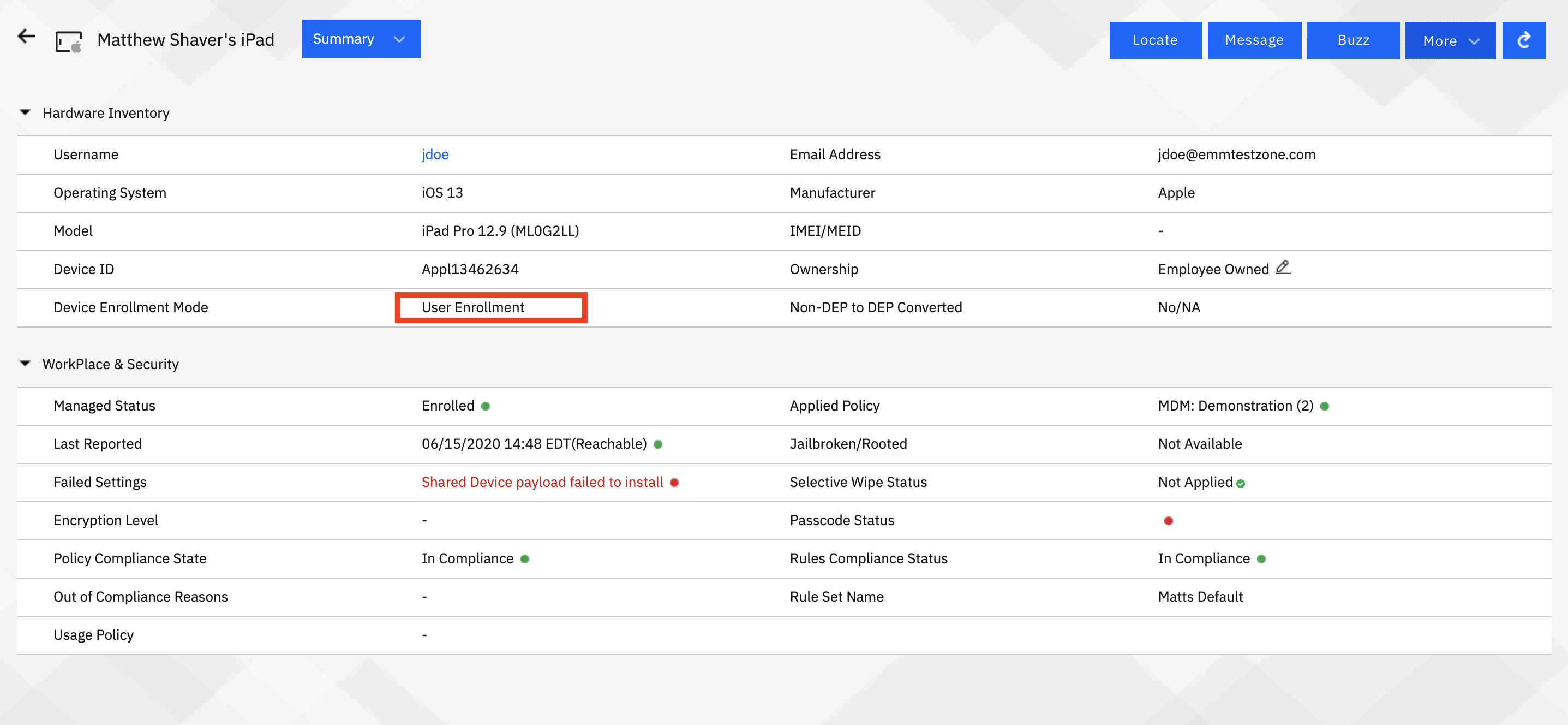
Application distribution will be limited to apps with VPP licenses. There will not be any silent install actions - user will have to initiate app installs from MaaS360.
As with any major shift in the device management market, User Enrollment will take some getting used to, and, for some organizations, a lot of setup. We've heard market demand for this type of feature for a while, but many of those asking have also shied away from embedding themselves in programs like Apple Business Manager. In order to support this, adoption of ABM/ASM is not something that can be avoided anymore. This means grabbing your company a DUNS number and going through the sign up process.
Anyone who still has the legacy systems (if it's even possible anymore) will need to upgrade to ABM/ASM to support.
We here on the MaaS360 side will continue to release enhancements to our implementation throughout the quarter, and I'll be updating this blog post as we do, so feel free to keep it in your bookmarks tab.
#Featured-area-2#MaaS360