Are you a MaaS360 customer managing mobile devices who is getting ready to move off your Exchange On-Premise environment and migrate to Office 365’s Exchange Online? You might be asking how this migration will affect your investment in MaaS360 and what you need to do in MaaS360 to support this migration.
This blog identifies what you need to consider and common MaaS360 tasks to support your migration to Office 365 (O365) Exchange Online. The following topics are covered.
- Overview
- Planning
- Conditional access considerations
- Authentication considerations
- MaaS360 Components
- Sample Scenarios
- Resources
Overview
MaaS360 has several components that are used to configure mail on devices, provide visibility to your company mail environments, and control access to mail based on compliance. Maas360 does not affect the flow of email traffic between your devices and Exchange. Therefore, when you are moving your Exchange mailboxes from on premise to the cloud, MaaS360 just needs to know where they are and how to access them so these configuration settings can be distributed to devices.
IBM’s open ecosystem and complimentary partnerships provide you flexibility in your service choices while continuing to leverage your existing endpoint management investment with us. MaaS360 is a best of breed unified endpoint management (UEM) solution that is part of IBM’s open ecosystem zero trust strategy, which is designed to ensure you have the flexibility to integrate with complimentary services from Microsoft 365 such as O365 Exchange Online. An important benefit is not locking you in to any one particular vendor or service or settling for a mediocre implementation that negatively affects security and productivity. The chart below highlights the use cases and integrations with Microsoft 365.
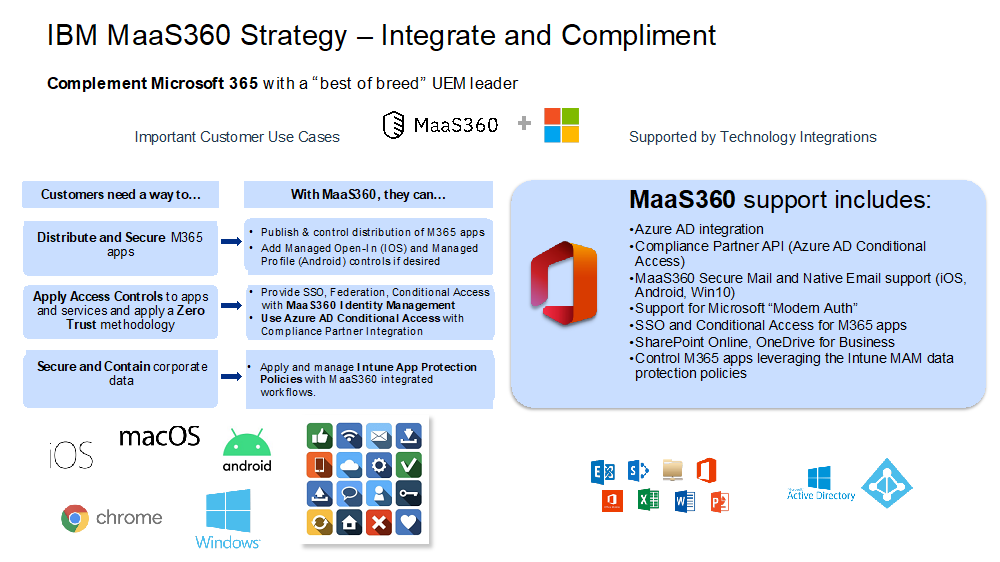
Planning
First, you need to understand your current environment and what you are trying to accomplish. Complete the questions in this matrix and review the referenced documentation for more details. If you are not sure yet, that’s no problem. The objective is to understand your scope.
|

|
Planning question
|
Choices
|
Description/Documentation
|
|
|
What kind of Exchange migration are you planning? |
_Cutover
_Phased/Hybrid |
Your choice is determined by the number of users/mailboxes you have and your current Exchange on-premises environment. You can find the details on Exchange migration types here |
|
|
How will users authenticate with O365 to access Exchange Online mail? |
_Basic Auth
_Modern Auth |
Authentication type can determine the policy settings that must be configured and the supported mail clients. Learn more here.
Basic Authentication: Username and Password
Note: Basic authentication is disabled by default in new O365 tenants and MS is in the process of deprecating Basic Auth. Learn more here.
Modern Authentication: Federated Identity/SSO/MFA
MaaS360 Policy configuration changes are required to move from basic auth to modern auth. Learn more here
|
|
|
How do your current MaaS360 enrolled/activated devices access on-prem Exchange mail? |
_Native Mail
_Secure Mail |
Identify the policies you currently use to access Exchange on-prem mail. The configuration settings will need to change to support O365 if you continue to use Native or Secure Mail. Learn more here.
Native Mail: MaaS360 MDM Policy with ActiveSync settings
Secure Mail: MaaS360 Workplace Person Policy with ActiveSync Settings |
|
|
How will your MaaS360 enrolled/activated devices access Exchange Online mail? |
_Native Mail
_Secure Mail
_Outlook App |
If you plan to move to Microsoft’s consumer mail app, Outlook, consider the following:
- Modern auth is required
- ActiveSync mail connections are not used consistently
- Data leak prevention controls
- User experience will change
- Conditional access is needed to control email access based on compliance status, AutoQuarantine/Block is not supported with Outlook.
|
|
|
What type of Users do you have in MaaS360 User Directory? |
_Local Users
_AD/LDAP
_Azure AD |
Go to Users>Directory in the MaaS360 portal and review User Source. Learn more here |
|
|
What current Cloud Extender integrations do you have? |
_User Vis
_User Auth
_Exchange
_Email Notifications
_None |
It’s important to note that Cloud Extender is not required to access email from the device. Cloud Extender provides visibility and control into your Exchange mail environment from the MaaS360 portal. Review the Cloud Extender module description and architecture here.
Review Cloud Extender migrations options based on Exchange migration type. |
|
|
What Cloud Extender Exchange Settings are currently enabled? |
_Auto Quarantine
_Retain Exchange
_None |
Cloud Extender Auto Quarantine overview:https://www.ibm.com/docs/en/maas360?topic=portal-enabling-auto-quarantine-aq-exchange |
|
|
What is your current Identity Source? |
_On Prem AD
_Azure AD
_Other |
When you access your mail environment, using settings from native mail, secure mail, or a mobile app, typically the variables username, domain, email address are used that were cached to the device when you enrolled, not what’s currently in the Maas360 User record. Therefore, you need to consider whether the email configuration settings will need to change. Learn more here. |
|
|
What is your future Identity Source? |
_On Prem AD
_Azure AD
_Other |
If you are moving from On Prem AD to Azure AD as your Identity Source, this also might affect how you enroll your devices moving forward. Customers often continue to use On Prem AD as the Identity Source with Azure AD serving as the Identity Provider, integrating with ADFS, or integrating with another Identity Provider such as Okta or Ping, See Authentication considerations |
Conditional access considerations
The decisions you make based on if and how you are planning to implement conditional access can affect your Exchange migration strategy. Conditional access determines whether you get access to a resource beyond just your membership in something static like a group, it is based on a compliance state that is constantly changing. That compliance state can be based on device compliance. Many data points and actions can contribute to the compliance state, whether it’s MDM enrollment status, having an outdated operating system, attempting to access blocked websites, and more.
Note: Implementing conditional access is not a requirement, it is an option.
Basic Conditional Access with MaaS360 and the Cloud Extender Exchange Module
MaaS60 and the Cloud Extender Exchange module provide basic conditional access for email. Cloud Extender is a free software module that is available with the entry level MaaS360 Essentials Suite (and therefore with every bundle). You can enable Auto Quarantine to block new unenrolled devices that attempt to connect to Exchange and block enrolled devices based on a wide variety of options using MaaS360 Security Compliance Rules. This is available for ActiveSync connected mail only, therefore the Outlook mobile app is not supported.
Conditional Access with MaaS360 Identity and Access Management using IBM Security Verify
If you want to go beyond conditional access for mail and grant access to mobile apps based on compliance state, you can enable the Identity and Access Management service in MaaS360. Verify is a free complimentary service that can be enabled in the MaaS360 services workflow. MaaS360 also includes a no-charge User Risk Management component that enables you to configure compliance events that contribute to the user risk score that can determine the compliance state for a device and user.
Learn more about MaaS360 and Verify for Conditional Access here.
Note: MaaS360 can also use Verify to pass compliance state to a third party IdP such as Okta to control app access.
Learn more here.
Conditional Access with MaaS360 and Azure AD integration
If you have an Azure AD P1 license that enables conditional access, MaaS360 can integrate with Azure AD to provide compliance state based on MaaS360 compliance to Azure AD for app access. MaaS360 continues to use its User Risk Management feature and device compliance to set compliance state, its App catalog to distribute the mobile apps, and policies and compliance rules to secure devices. For this integration, you must configure User Visibility for Azure AD in MaaS360 and enable compliance updates between MaaS360 and Azure.
Note: Please review our latest blog on MaaS360 integration with Azure AD for conditional access here
Authentication considerations
In MaaS360, there are 3 main types of authentication: authentication when you enroll, authentication when you access a service like email, and authentication when administrators access the portal.
If you are using Cloud Extender User Auth with AD to enroll devices and you do a full cutover to Azure AD as your Identity Source, you would need to decommission the Cloud Extender User Auth module and configure the cloud to cloud User Auth integration between MaaS360 and Azure AD OR set up SAML authentication.
When you migrate to O365, whether you continue to use Active Directory as your identity source or move to Azure AD, O365 will need to know how to authenticate the user and determine access. MaaS360 provides the username and target service URL, and authentication type to O365 based on settings configured in the policy for MaaS360 native or secure mail or in the App Config parameters for mobile apps.
O365 requires the users that will access email be added to Azure AD in order to assign the Exchange online license, regardless of whether the Identity Source will remain on Active Directory. When migrating to O365, Azure AD with AD Connect enables you to continue to use Active Directory as your Identity Source, by using AD Connect with Pass Through Authentication, Password Synchronization, ADFS, or an Identity provider like Azure AD, Okta, Ping, or IBM Security Verify. Be sure to consider if you make a change, how the user experience will be affected.
Important: When moving from Exchange On Premise to Exchange Online, you will most likely be looking at changing from basic authentication to modern authentication to access mail from MaaS360 Secure Mail or native mail configured through MaaS360 Persona and MDM policies, respectively. Learn more about moving from basic authentication to modern authentication for Exchange Online email access in this blog.
MaaS360 Components
The following is a list of the MaaS360 components that are used for mail configuration, access, and compliance. Determine which components you will continue to use and what you will change.
|

|
Component Type
|
Description
|
|
|
MaS360 Policies
|
MDM Policies and WorkPlace Persona Policies (Secure Mail)
- Email configuration
- DLP settings
|
|
|
Cloud Extender Modules
|
- Exchange (On Prem and Online) - visibility and access control
- Email notifications
|
|
|
Cloud Extender Exchange Settings
|
- Auto Quarantine
- Service Accounts
- Host information
- Mailbox, OU, Domain Selection Criteria
|
|
|
MaaS360 enrolled device
|
When you enroll your device, you either authenticate using MaaS360 Local User credentials or corporate credentials. Using corporate credentials requires integration with your Identity Source/IdP via Cloud Extender User Auth, SAML configuration, or Azure AD integration. In all cases, the username, email address, and domain are cached with the device record. These variables %username%, %email%, and %domain% can be used in combinations with literals and other user attributes to access your email service, example %username%@myonlinemaildomain
|
|
|
MaaS360 User Record
|
Additional user attributes from the MaaS360 User Record can be used for email configuration and migration (Corporate directory User Vis required for AD users). For example with AD users the UPN is also included in the User record. User attributes can used to identify users who have migrated to O365 helping with group policy assignments and app distributions between non-migrated and migrated users.
|
|
|
MaaS360 Groups
|
MaaS360 Groups are used for policy assignments, distributing apps and content, and group based compliance. Groups can be imported from Active Directory using Cloud Extender User Visibility, integration with Azure AD User Visibility, or created manually in MaaS360. Groups can help you to assign new policies with O365 settings to a subset of users/devices during your migration.
|
|
|
App Catalog
|
If you will be using the Outlook Mobile App, add it to the MaaS360 App Catalog and configure App Config parameters to access O365 mail.
|
|
|
Compliance Rules
|
Compliance Rules can be used to Block email access to Exchange mail service based on out of compliance events, like unenrolling a device. The Cloud Extender Exchange module integration is required for this feature.
|
Scenarios
The following scenarios were created to help provide examples that represent likely conditions and environments across the MaaS360 customer community.
Scenario1: CompanyA
CompanyA is currently using the MaaS360 Secure Mail container to access Exchange on Prem mail with WorkPlace Person Policies. Their current authentication is Basic, but when they move to O365, modern authentication will be enabled. They will continue using the Cloud Extender Auto Quarantine feature and compliance rules to block mail access based on compliance state. Active Directory will continue to be their Identity Source with ADFS and Azure AD Connect.
- Exchange Hybrid Migration: 100,000 mailboxes on Exchange 2010
- MaaS360 Security Policies: Secure Mail with ActiveSync Settings
- Mail Authentication: Basic=>Modern
- MaaS360 User Directory Source: AD/LDAP Users
- Cloud Extender: User Authentication, User Visibility, Exchange
- Auto Quarantine enabled
- O365 tenant configured with AD Connect where Active Directory is the Identity Source
- Determine your mailbox migration strategy
- By number of mailboxes, number of OUs
- How long is your phased strategy 6 weeks, 6 months?
- Determine the Exchange Cloud Extender modules to support the migration
- Install and configure new Cloud Extender Exchange modules for O365 as needed
- Configure Cloud Extender Settings
- Duplicate the MaaS360 Workplace Secure Mail policies and configure for O365
- Enable Modern Auth
- Configure mail settings
- Set as default if you want new enrollments to connect to O365
- Create Groups for users that migrate to O365 for policy assignment
- Can create a User Attribute to determine the migrated users.
- Configure the Cloud Extender User Visibility module to update the User Attribute and Import Groups
- Assign the Workplace Persona policy to the Group
- Move a small test set of mailboxes to O365
- Update the user attribute and group membership in Active Directory for the test set of users
- Initiate a User Visibility refresh
- The policy will be assigned to the users/devices in the group
- The next time the user accesses mail from their device, they will be prompted to authenticate again
Scenario2: CompanyB
CompanyB is currently using Native Mail to access Exchange on Prem mail with MaaS360 MDM Policies. Their current authentication is Basic, but when they move to O365, modern authentication will be enabled and they plan to rollout the Outlook App. They want to limit data leakage from the Outlook App by using DLP controls. They will continue to use Active Directory as their Identity Source with ADFS.
- Exchange Hybrid Migration: 1000 mailboxes on Exchange 2013
- Outlook Mobile App
- MaaS360 MDM Policies for DLP controls
- Mail Authentication: Basic=>Modern
- MaaS360 User Directory: AD/LDAP Users
- Cloud Extender: User Authentication, User Visibility
- O365 tenant with AD Connect where Active Directory is the Identity Source
Note: If you are planning to use Azure AD Conditional Access to control access to the Outlook App, you require User Visibility integration with Azure and MaaS360 which would mean you would decommission the User Visibility Cloud Extender to AD/LDAP and use the Cloud to Cloud integration with Azure AD. This use case is outside the scope of this blog and will be discussed in an upcoming blog. More information can be found here.
- Determine your mailbox migration strategy
- By number of mailboxes, number of OUs
- How long is your phased strategy 6 weeks, 6 months?
- Add the Outlook App to the MaaS360 App Catalog
- Set App Config parameters to access O365 mail
- Duplicate the MaaS360 MDM policies to enable DLP controls and remove ActiveSync Settings
- Remove the ActiveSync MDM settings since the Outlook App will be used
- Enable iOS Managed Open In restriction if not already enabled
- Use Android Enterprise Profile Owner for BYOD
- Create Groups for users that migrate to O365 for policy assignment
- Create a User Attribute to determine the migrated users.
- Configure the Cloud Extender User Visibility module to update the User Attribute and Import Groups
- Move a small test set of mailboxes to O365 and test
- Update the user attribute and group membership in Active Directory for the test users
- Initiate a User Visibility refresh
- The MaaS360 User group should be updated with the migrated Users automatically
- The policy will be assigned to the users/devices in the group
- Distribute the Outlook Apps to the group
- Assign the new MaaS360 MDM policy with no ActiveSync Settings to the group
- Test access to O365 mail using the Outlook App
Note: To strengthen DLP for the Outlook app to limit cut, copy, paste and copy to cloud apps, MaaS360 integrates with Intune App protections policies: https://www.ibm.com/docs/en/maas360?topic=overview-microsoft-intune-app-protection-policies.
Resources
Microsoft Mail Migration types:
https://docs.microsoft.com/en-us/exchange/mailbox-migration/mailbox-migrationBasic to Modern Auth Migration for Policies:
https://www.ibm.com/support/pages/node/6449702
Mail Policy Settings
MaaS360 User Directory: https://www.ibm.com/docs/en/maas360?topic=users-using-user-directory
Cloud Extender:
Please reach out to your MaaS360 account representative if you require more guidance. If you are unsure who your account representative is, please contact the IBM Security MaaS360 Customer Success team at csmaas@us.ibm.com.
Your account representative can also provide you information on IBM Security Expert Labs. The IBM Security Expert Labs team has simple and full service options that can be leveraged to provide guidance and implementation services to customers when determining how to move forward with your migration strategy.
Learn more here:
Simple services
Full service options
-