I was asked by one of my customer for an assistance about ADFS integration with IGI. It was not so complicated to do the integration, but i had some challenges to got it working. So, i decided to write this blog post.
This blog post is here to document a simple use case about IGI and ADFS integration for Service Center authentication. You may have some challenges with username mapping, but if you are able to make it working in a simple use case, you will only have to deal with the name mapping challenge.
Let's see the major steps.
Test user descriptionIn Active Directory my test user is defined as this :
In IGI my test user is defined like this
Requirements
- IGI 5.2.6.1 deployed configured
- Windows 2016 with ADFS deployed and configured
- ADFS Root and Intermediate certificate
- Make sure name resolution is correctly working and there is no time issue (date,time and timezone)
Configuration Setup
A. Root and Intermediate ADFS Certificates sharing with IGI
Let's start with Certificates sharing with IGI. This steps is necessary to ensure IGI can discover the endpoint configuration;
- Connect to IGI LMI console
- Upload ADFS root and Intermediate certificate in IGI
- From IGI LMI console, click "Configure", then under "Manage Server Settings" click "Certificates",
- Edit "IBM Security Identity Governance and Intelligence key store",
- In "Signer" tab, upload the ADFS endpoint Root Certificate and Intermediate certificate
- Restart IGI
B. ADFS Configuration for IGI
Disclaimer : ADFS configuration documented here must be reviewed by your ADFS admin team to ensure the conformity with your security rules.
- Right Click on "Application Group", click "Add Application Group"
- Give the new "Application Group" a name, here IGI
- Select "Server Application", click "Next"
- In the redirect URI enter : https://<igi_app_fqhn>:9343/oidcclient/redirect/iamlab
- iamlab is important. It has a direct dependency with the provider name you will define in IGI (next section)
- Replace <igi_app_fqhn> with your IGI Server FQHN ; the one to access Service Center
-
- Click "Next"
- Click on the checkbox "Generate a Shared secret", copy and save the secret ; You will need it during IGI configuration
- Click "Next" , then "Close". The application group is created.
Important : Write down the client ID and Shared Secret you will need them during IGI Configuration.
If you go with this configuration, you may have the following error in ADFS (event viewer), and an error on ADFS login page.
Microsoft.IdentityServer.Web.Protocols.OAuth.Exceptions.OAuthUnauthorizedClientException: MSIS9321: Received invalid OAuth request. The client '55395f85-b82b-486c-9fa6-db77a6c67b94' is forbidden to access the resource 'http://schemas.microsoft.com/ws/2009/12/identityserver/selfscope'.
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthAuthorization.OAuthTokenBrokerAuthorizationRequestContext.ValidateBroker()
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthAuthorization.OAuthTokenBrokerAuthorizationRequestContext.ValidateCore()
To fix it, you have to go with "PowerShell"
1. Allow the clientID to access the resource
Grant-AdfsApplicationPermission -ClientRoleIdentifier 55395f85-b82b-486c-9fa6-db77a6c67b94 -ServerRoleIdentifier http://schemas.microsoft.com/ws/2009/12/identityserver/selfscope2. Get the ID of the new object create, this to define the scope of the permission
Get-AdfsApplicationPermission -ServerRoleIdentifiers "http://schemas.microsoft.com/ws/2009/12/identityserver/selfscope"3. Look for the entry which corresponds to your client, then copy the "
ObjectIdentifier" attribute value.
4. Define "
openid" then "
aza" scope
Set-AdfsApplicationPermission -TargetIdentifier fe56f061-c689-45e8-af8d-b8fdf5d1e60f -AddScope 'openid'Set-AdfsApplicationPermission -TargetIdentifier fe56f061-c689-45e8-af8d-b8fdf5d1e60f -AddScope 'aza'5. Check the configuration is updated ; you will notice now "ScopeNames" contains "
aza" and "
openid"
Get-AdfsApplicationPermission -ServerRoleIdentifiers "http://schemas.microsoft.com/ws/2009/12/identityserver/selfscope"
6. Restart ADFS service
You are done for ADFS configuration. Now we can continue with OIDC setup on IGI side.
C. ADFS Configuration in IGI
As it is not possible to have External OIDC and Internal OIDC configured at the same time, we have to disable the internal OIDC provider.
1. Connect to IGI LMI http://<fqhn_igi_lmi>:9443/fallback. ; replace <fqhn_igi_lmi> with your FQHN.
2. Click on "OpenID Connect Provider Configuration" available under "Manage Server Setting" in "Configure" menu.
3. Click "Disable".
Note : A restart of IGI is necessary after this configuration change. IGI logon page will not have the same look and feel !
Now we can continue by setting up the External OIDC configuration in IGI.
Go in "OpenID Connect Configuration".
- Click New
- Set the provider name, in this configuration "iamlab"
- Set the "Configuration" to "Discovery Configuration"
- Enter the ADFS discovery URL, it should look like "https://<adfs-fqhn>/adfs/.well-known/openid-configuration ; replace <adfs-fqhn> with your ADFS endpoint FQHN.
- Set "Signature Algorithm" to RS256
- Set User ID to Create Subject to "upn"
- Enter the Client ID and Shared Secret obtained from ADFS team
- Select the checkbox "Service Center"
- Click Save configuration
- All fields will be populated
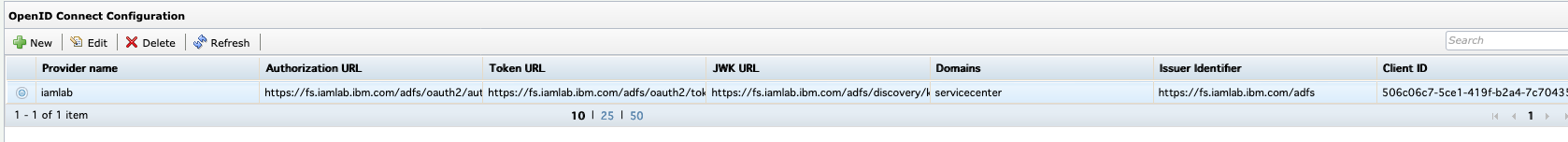
We are done, you can restart IGI
Note : I used the "upn" for the "User ID to Create Subject", based on the information i expect from ADFS by default.. If you have an issue with that attribute or a different one to handle, you can have a look to IGI trace file. The information you are looking for is similar to this :
{"aud":"506c06c7-5ce1-419f-b2a4-7c70435cecc0","iss":"https://fs.iamlab.ibm.com/adfs","iat":1595322147,"exp":1595325747,"auth_time":1595322146,"sub":"5zx9YG9asrSY1h6vpscSKvjEOuE2sg5n6LeZYuOGqpU=","upn":"sfnoel@iamlab.ibm.com","unique_name":"IAMLAB\\sfnoel","sid":"S-1-5-21-3728494814-2886181673-2121607864-1116"}
Testing
- Go to https://<igi_app_fqhn>:9343/
- Click on Service Center
- You are redirected to ADFS for authentication
- Insert the user name and password
- Click on Logon, you are then redirected to IGI Service Center and authenticated
Let's have a look to the demo video
Troubleshooting
IGI OIDC troubleshooting
IGI is executed by Websphere Liberty. For OIDC troubleshooting on IGI you can enable the following trace :
OpenID Connect -or- OAuth -or- JWT authentication
com.ibm.ws.security.*=all:com.ibm.ws.webcontainer.security.*=all:com.ibm.oauth.*=all:com.ibm.wsspi.security.oauth20.*=all:org.apache.http.client.*=all
OpenID
com.ibm.ws.security.*=all:com.ibm.ws.webcontainer.security.*=all:com.ibm.ws.transport.http.*=all:org.openid4java.*=all:org.apache.http.client.*=all
Source :
https://www.ibm.com/support/pages/node/272965The following steps are necessary to enable the traces
From IGI Console
- Click "Manage" then clic on "Log Retrieval and Configuration" under "Maintenance"
- In the "Log Retrieval and Configuration" page, click "Configure"
- Go to "Application Server" tab
- Insert the trace settings to be enabled as shown in the picture below, then save the configuration
- Restart IGI
Once you have the trace enabled and IGI restarted, they can be accessed by 2 methods :
- From the LMI,
- In "Log Retrieval and Configuration"
- From a support file,
- Generate a "support file", download it, then unzip the support file
- Traces are located in opt/ibm/wlp/usr/servers/igi/logs
- Trace file are named trace.log, trace history are named trace_YY_MM_DD.0.log
TIPS : WebSphere enabled people, will recognize the trace file and could help you to go thru them.
ADFS issue troubleshooting
For ADFS troubleshooting you can enable Admin and Trace logs. The process is well documented on Microsoft WebSite
here