Now that we have what we need from IBM Security Verify Access lets get started with coding! Extract the zip file you just downloaded and create a new Plug-in project in Eclipse. We will use the extracted jar file as the starting point for the new project. You will need to import the extension jar that was unzipped as well as setting a project name/description.
Now we will update our build target. Open the Target Platform configuration menu (window → preferences → plug-in development → target platform) and create a new target platform.
In this target you need to import the extension jar that was downloaded from the appliance (com.ibm.security.access.extension_8.0.0.jar) as well as any other dependencies that your project will require. This example will return JSON as well as HTML so I have imported an implementation of the javax.json interface (com.ibm.websphere.javaee.jsonp.1.1_1.0.30.jar), your project may differ. To import the required jars, add a new Directory to the build target and navigate to the directory which contains the required jars.
Next we need to update the manifest and plugin.xml files. This is easily done with the Eclipse Plug-in Manifest Editor. The Overview tab shows information that was entered during creation. Feel free to update any of the General information as well as setting the singleton parameter.
Update the project dependencies in the dependency tab by adding packages in the Imported Packages window. At a minimum you will need to import some of the packages from the com.ibm.security.access.extension_8.0.0.jar but your exact requirements may vary. For this example I import com.ibm.security.access.extension.* and javax.json (note you may need to select “show non-exported packages” to get your dependencies to be visible).
You will also need to add any dependent jars your mechanism uses to the classpath. If you don’t do this step your project will probably still compile however when you upload your mechanism to IBM Security Verify Access it won’t execute as expected. For convenience I added all the jars I require into a “lib” directory.
In the next tab you will set the parameters of your extension. Here you can set:
-
The name that will appear in the list of Mechanisms available on IBM Security Verify Access
-
The class which should be loaded as the entry point for your extension;
-
Any administrator configured properties which are required for your mechanism to function correctly.
-
The available data types for properties are: Boolean, Double, Integer, String, KeyStore, Email, X500, URI, URL, Hostname, Date, LdapServerConnection, SMTPServerConnection and WSServerConnection.
With our extension project set up we can now get started on coding! This is the point where your mechanism may significantly diverge from this example.
The final step in implementing a custom extension is successfully compiling it into a jar that can be uploaded and interpreted by IBM Security Verify Access. This can be quite tricky so I have provided an example build.xml that can be used by the Apache Ant build tool. The build file can be broken down into two steps:
-
Compiling java into .class files
-
Packaging the .class files along with any dependencies into a .jar file which can be uploaded to IBM Security Verify Access.
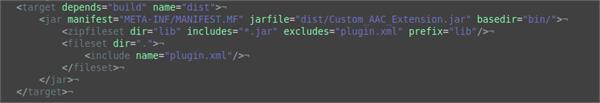
When packaging the jar we need to make sure that we include any dependencies that the mechanism needs. As mentioned previously I added all of my dependencies into a “lib” directory, which makes including them easy. If your dependencies are in a different location you will have to modify the zipfileset tag to point to the jars you need.
The fileset tag ensures that the Eclipse generated plugin.xml is included in the final jar. This xml document is essential for IBM Security Verify Access to be able to understand the parameters required and the class it should execute to run your extension. If your mechanism is not appearing in the list of Authentication Mechanisms after your jar has been uploaded, this may be why.
Creating an authentication policy using your Java authentication mechanism:
Now that we are done with the coding side of things, lets create an authentication policy using the mechanism we just wrote. To start things off navigate to the extensions menu under the AAC mega-menu.