
Updating your Phishing response plan to deal with increased volume
With the daily disruption into everyone’s lives, there is naturally a surge in demand for the latest information and updates on the novel coronavirus (COVID-19). This has unfortunately translated into a significant increase in phishing campaigns and targeted email spam looking to exploit individuals who are looking for more information on the pandemic. The X-Force Incident Response and Intelligence Services (IRIS) team has been tracking these threats and you can find more information on their recommendations here.
For existing Resilient customers, there are some playbook optimizations or 3rd-party integrations they could leverage to better contain and remediate email threats in their environment. In this blog we will look to run through some of these, and we will be hosting a tech talk to discuss phishing playbooks use cases and optimization. The three areas we are going to focus on in this blog are around the in-product email connector, playbook customization, and automation.
In-Product Email Connector
The Resilient Email Connector is a flexible component that enables organizations to easily integrate the Resilient SOAR platform with a variety of processes and systems that generate security alerts. Individuals and systems can easily generate incidents in the Resilient platform by simply sending an email message. Customers can configure the email connector as an IMAP or POP3 mailbox, with all configuration and testing happening in the UI.
Once the email connector is configured, individuals can send an email to an abuse box which will then automatically generate an incident within the system. This is a considerable time saving for analyst when dealing with a high-volume threat like phishing attacks.
In addition to this, there is a Generic Email Parsing Script app available for Resilient in the IBM Security App Exchange. This app is a customizable python script that will parse the email body text looking for URLs, IP addresses and file hashes. After filtering out invalid and whitelisted values, this data will be added to the incident as artifacts for further investigation.
The script can also be configured to either append this information to an existing incident, or to create a new incident if there is no corresponding incident. Non-inline email attachments can also be added to the incident as well. The script app is designed to provide examples and is full extensible to meet your own specific requirements.
Customizing and Automating Playbooks for Phishing attacks
At this point you have ingested the suspicious email content, parsed out the relevant information into artifacts and added any attachments. Now you can define the tasks that the security operations team need to complete in order to run the phishing playbook, and a significant number of these should be automated.
In the Resilient platform, playbooks make use of integrations, functions, and scripts to help orchestrate your incident response process. These are likely to be a combination of internal processes but also to leverage 3rd-party security applications as well.
Some of the common 3rd-party applications that customers can access quickly and easily include common email security tools like Mimecast and Proofpoint TAP, allowing for the seamless integration of data between Resilient and these security tools to trigger processes to identify known phishing threats and block newly discovered malicious domains. We also provide out-of-the-box integrations for Microsoft Exchange and Office365 to support full bi-directional email integration to allow security analysts to identify users, search for emails and delete phishing emails from Exchange mailboxes. Analysts can query emails in Exchange and run our email parsing app on the .eml file. This will create an incident in Resilient and trigger automation playbooks
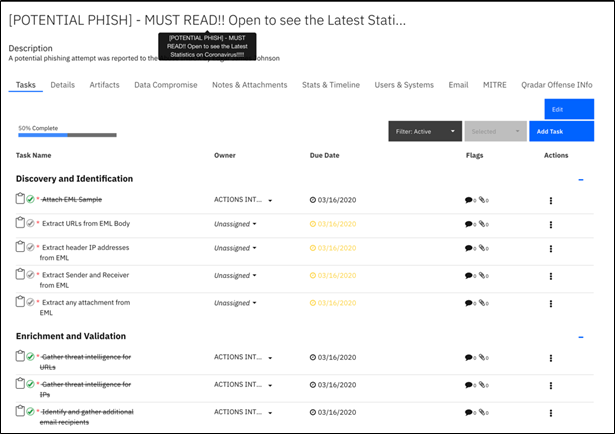
Here we can see an example of some of the steps of a Phishing playbook. The initial phases would typically be the ingestion of the email, any attachments and the artifacts that have been parsed from the email.
Once these artifacts, or Indicators of Compromise (IoC) have been extracted, then there are a number of automations around enrichment that can be configured. These would include the automated correlation of artifact information with threat feeds – these can be pre-installed feeds, including VirusTotal, IBM X-Force Exchange and others, plus a large number of commercial feeds and Threat Intelligence Platforms (TIP) including Anomali, Recorded Future, Cisco and many others which are also available from the IBM Security App Exchange.
Other automated enrichments would typically include internal data sources like LDAP and CMDB to identify impacted users and assets – once we know the who and what, this might trigger escalations in the response process, if the incident involves a high value employee or asset for example.
Common steps at this point will depend on the artifacts you have gathered, the goal of this workflow is to quickly reach a triage point, where the analyst has identified whether the phishing attack has been successful or not. Searching for the URLs in the SIEM will help us reach this conclusion, as well as running an IoC hunt across endpoints looking for known malware samples. The idea is that the process will depend on your current security architecture and processes, using automation and orchestration to streamline and speed up response times. For example, if an IP or hash is found to be malicious in within the email you can automatically blacklist the IP address or ban the malicious hash. Then you can run reporting and advanced analytics based on the number of malicious phishing emails you have seen.
Resilient helps your incident response team create a well-defined process to address phishing emails that may threaten your organization. Most clients base their playbooks on the NIST 800 framework and are able to create a playbook that integrates people, process, and technology. We are going to run a tech session on April 29th at 10am ET to explore this topic in more detail, you can
register for the talk here. Please leave a comment or feedback below if you have questions or suggestions. We’d love to hear from you.
#Resilient
#ACE on Cloud