A key aspect of your Zero Trust strategy must include Device Trust. With users connecting to a myriad of SaaS apps for better productivity, it is important to be certain that their devices adhere to a robust Zero Trust strategy. Having a strong Identity Management Policy is a good start, however, you also want to make sure the device is trusted.
If your Device Trust strategy includes using
Azure AD Conditional Access, you may find leveraging device information a challenge. Customers that use MaaS360 and that leverage Azure AD Conditional Access will find that this feature is now integrated into the MaaS360 Device Unified Endpoint Management capabilities.
What's New? Microsoft now provides a capability allowing MaaS360 to write Device Compliance information to Azure AD for iOS and Android devices. This helps to facilitate using MaaS360 for Device Management alongside Azure AD Conditional Access rules that are typically used to limit access to Microsoft 365 services (e.g. Teams). For more information on the Microsoft, Device Compliance Partner API see:
https://docs.microsoft.com/en-us/mem/intune/protect/device-compliance-partnersThis new capability offers customers a choice. Previously, the only option was to rip and replace and then go to InTune MDM to leverage Azure AD Conditional Access for Device Trust.
Using this new capability, administrators can now use MS Graph APIs to integrate with Azure AD Conditional Access Device Trust. This provides the ability to sync Device Trust information (isEnrolled, isCompliant) with Azure AD. Customers can then include and enforce MaaS360 activated devices into Azure AD Conditional Access rules.
Setting it upSet up is simple. After the feature has been enabled for you by IBM Support, head over to the Microsoft Endpoint Manager console and add MaaS360 as a Compliance Partner (see:
Integrating MaaS360 with Microsoft to enforce device compliance through Azure AD Conditional Access).
Figure 1 - Adding MaaS360 as a Device Compliance Partner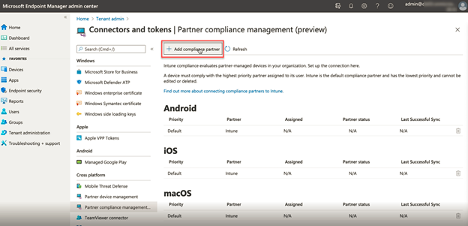
Then register the MaaS360 App in the Azure AD tenant to service the registration requests (see:
Registering MaaS360 app in the Azure AD tenant).
Once this is done, go to the MaaS360 portal and update the Azure AD Configuration settings to enable the integration by adding the Azure AD Tenant ID and App ID (Client ID) of the MaaS360 Application you just registered. Then add the Azure AD Groups that you want to be part of the program; these users will be prompted to register their device once this is done.
Once these steps are completed, device data from registered devices will start synching over to Azure AD and you will be able to see them in the Azure AD console in the Devices listing.
Figure 2 - MaaS360 Azure AD Integration Configuration
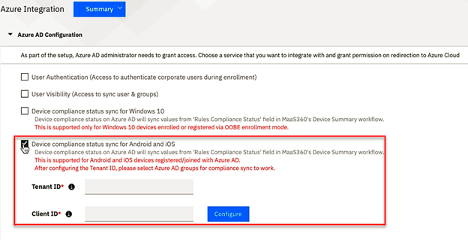
What the end user can expect For device data to be synched over to Azure AD, the device must be Azure AD Registered. Fortunately, this process has been streamlined and facilitated by the MaaS360 app on iOS or Android devices. The targeted users will be prompted to register their devices in Azure AD. This will invoke the MS Authenticator app (required) to facilitate the registration process. After a couple of clicks and authentication, the user's device is registered. This is a one-time requirement.
Once the device is registered, device compliance data will be synced between MaaS360 and Azure AD and if the user is in a group that has been targeted for a Conditional Access policy, their device will be evaluated along with the other criteria in the rule.
As such, users on MaaS360 Enrolled and Compliant devices will then be allowed to access resources controlled by Azure AD Conditional Access rules that require a compliant device to connect.
Figure 3 - MaaS360 App Registration Experience Prerequisites
Prerequisites In order to participate, you should have at least Azure AD Premium (required for Conditional Access) and Intune licensing (required for Device Compliance). Targeted users/groups must have an InTune licensing applied. If you want to control which users are directed to register, select the desired Azure AD Groups, MaaS360 Azure AD Visibility. This
MUST BE ENABLED in order to retrieve Azure AD Group information. It cannot be acquired from Active Directory (or other directories). See:
https://www.ibm.com/docs/en/maas360?topic=maas360-configuring-azure-ad-integration.
It is also a good idea to push the Microsoft Authenticator App to all the in-scope devices before requesting users register their devices. The Microsoft Authenticator is the App that MaaS360 uses to accomplish the registration.
OutcomesBy taking these steps, MaaS30 Device Compliance rules can be used to intelligently control which users and devices can access Office 365 apps and services.
Figure 4 - Azure AD Conditional Access Rule Example Figure 5 - Architecture Overview Showing MaaS360 Enrolled Device in Azure AD
Figure 5 - Architecture Overview Showing MaaS360 Enrolled Device in Azure AD
 Resources
ResourcesFor more information on the Azure AD Conditional Access Compliance Partner Program see:
https://docs.microsoft.com/en-us/mem/intune/protect/device-compliance-partnersMaaS360 Docs:
Integrating MaaS360 with Microsoft to enforce device compliance through Azure AD Conditional Access