Configure protected universal apps (Blocklist):
In this section, we can configure universal apps that are not required to be protected by WIP. Admin can provide details (the app name, publisher name, app version (minimum), and app version (maximum)) of universal apps that are not required to be protected by WIP.
For example, if admin wants to protect all MS Apps except Sticky Notes. He can protect all MS apps using allowlist section
App name: *
Publisher name: CN=Microsoft Corporation, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
Then, he can configure Sticky Notes in blocklist section.
App name: Microsoft.MicrosoftStickyNotes
Publisher name: CN=Microsoft Corporation, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
With this configuration all MS apps will be protected except the Sticky Notes as shown below:
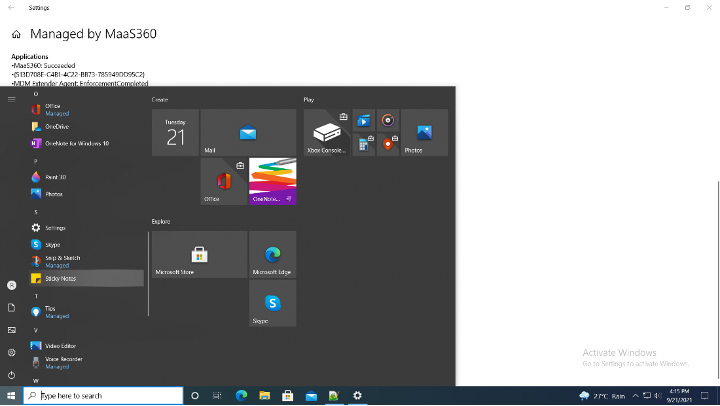
- Configure Protected Desktop Apps (Allowlist)
This section configures desktop apps that are allowed and protected by WIP. Admin can specify the app name, publisher name, app version (minimum), and app version (maximum) for the desktop apps that needs to be protected.
- Configure Protected Desktop Apps (Blocklist)
This section configures any desktop Application needs to be blocklisted/ not protected by WIP. Admin can specify the app name, publisher name, app version (minimum), and app version (maximum) for the desktop apps that needs to be protected.
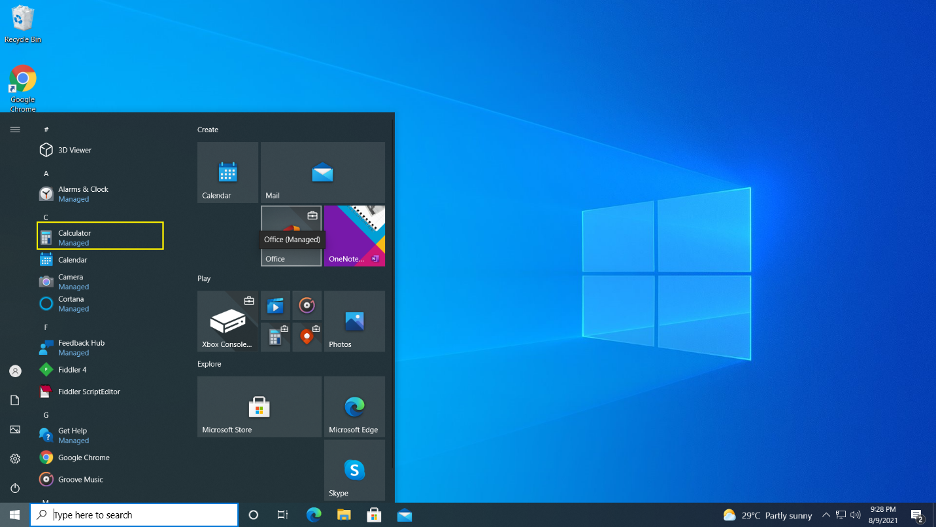
Once WIP policy is assigned on the device then the protected apps will be indicated as Managed as shown below:
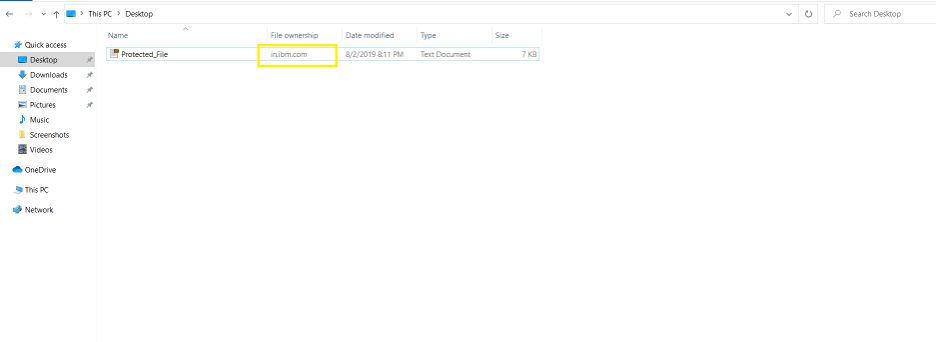
File Ownership is indicated in the Windows Explorer windows of protected Applications as below:
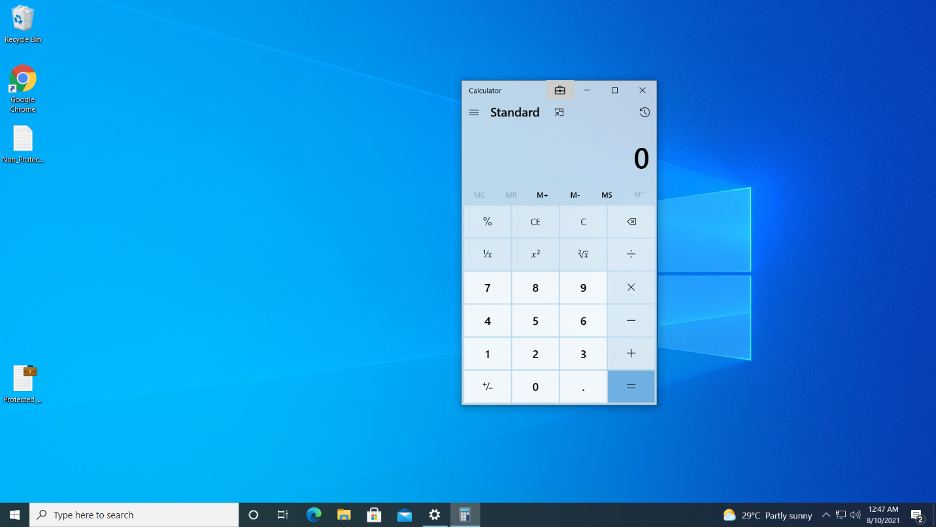
Briefcase icon is shown on the top right corner of the protected Application as shown below:
In this blog post, we learnt:
- What are the capabilities of the Windows Information Protection feature and how it can be configured through IBM MaaS360
- What are the various enforcement settings and their configuration on IBM MaaS360 portal
- How to reate data recovery certificates
- How to protect enterprise apps
- How to configure O365 as protected apps
In the coming blog(Secure Enterprise Data through IBM MaaS360 Windows Information Protection – Part 2), we will explore how we can leverage Windows Information Protection policy to protect data hosted on an enterprise network. We will also explore the difference between Enlightened and Unenlightened apps.