
Working from home in a lot of industries is now the standard and yet a lot of organizations still have yet to adopt more modern forms of security when allowing remote users to connect into the corporate network. With IBM Verify and IBM Cloud Identity, adding push notification verification multi-factor is simple, easy, and provides instant compliance for organizations who need to adopt these security patterns.
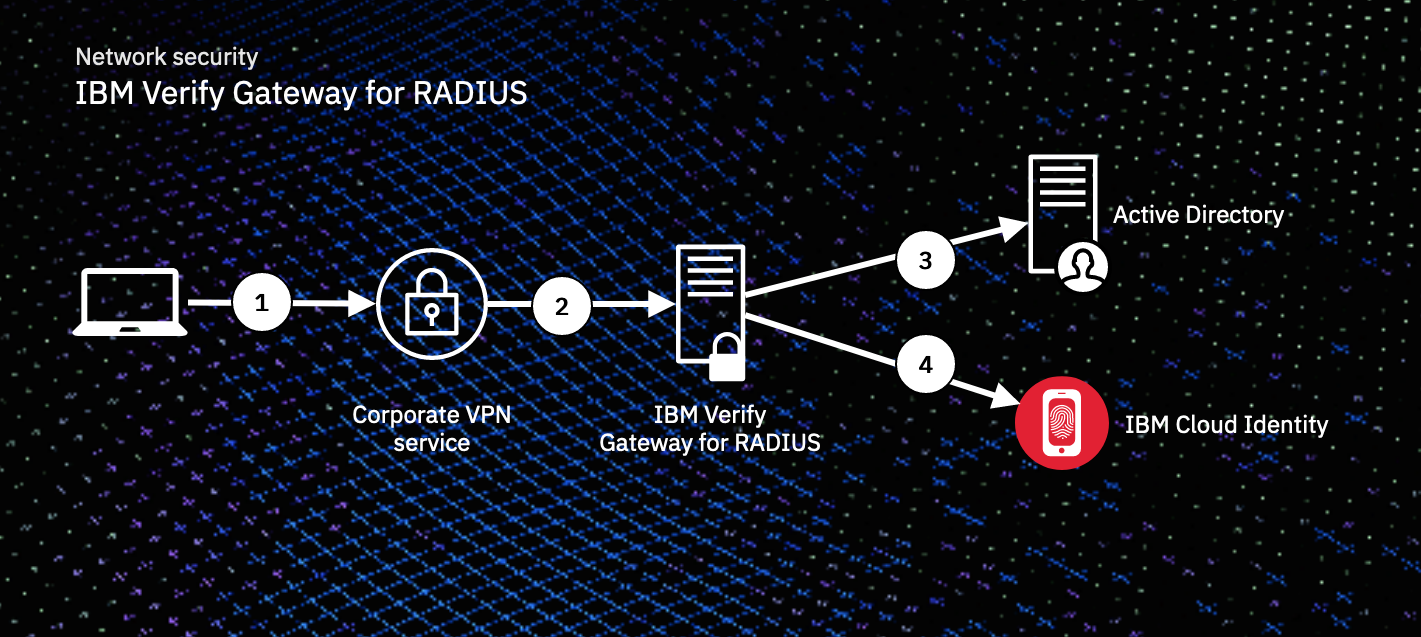
Interacting with the IBM Verify Gateway for RADIUS adds a single step during user authentication.
In the diagram above:
- The user connects to the VPN service by phone or laptop
- The VPN service contacts the IBM Verify Gateway for RADIUS and requests verification.
- The user is asked to first authenticate with their username and password.
Note: This could be either an onpremise (ex. Active Directory) password or the user's password from their Cloud Identity user record.
- The gateway pulls the user's profile information and MFA enrollments and presents options to the user and allows them to verify themselves during the authentication challenge. Once verified, they are authenticated.
See the experience
Watch the video below to see the end user experience with IBM Verify connecting to the corporate network.
Getting started with RADIUS
Download the installer from
here. Install the IBM Verify Gateway on a Windows 2012 64bit server with a minimum of 2vCPU, 4GB RAM, 1GB free storage. The service needs to be able to communicate to IBM Cloud Identity over port 443 and to the VPN server. This service listens on port 1812 by default but is completely configurable.
Complete documentation on using this service and all configurable options is found in the
Knowledge Center.
Configure the CIV RADIUS Gateway
There are a lot of different combinations, tweaks, and preferences that can be set to satisfy the company's use case. While we can't assume everyone wants the same, we can provide a few out of the box scenarios that will help speed up the deployment.
Provide MFA choices during authentication with Active Directory authentication
This allows for multiple choices during an authentication challenge. It uses the local Active Directory password for first factor authentication. It allows for user attributes to be displayed and used by users for 2nd factor verification. If the user chooses IBM Verify enrolled devices for push notification verification, then it will poll for acceptance every second until the timeout is reached.
"clients":[
{
"address": "192.168.1.101",
"mask": "255.255.255.0",
"auth-method": "password-then-choice-then-otp",
"name": "OpenVPN",
"secret": "Passw0rd",
"use-local-pwd-check": true,
"transients-in-choice":true,
"poll-device": true,
"poll-timeout": 30
}
],
Enforce IBM Verify for MFA using cloud user password
This is a simple configuration requiring IBM Veriffy as the only verification method. It uses the cloud directory password for first factor authentication. If the user has not enrolled in IBM Verify yet, they will not be able to authenticate. If the user chooses IBM Verify enrolled devices for push notification verification, then it will poll for acceptance every second until the timeout is reached.
"clients":[
{
"address": "192.168.1.101",
"mask": "255.255.255.0",
"auth-method": "password-and-device",
"name": "OpenVPN",
"secret": "Passw0rd",
"poll-device": true,
"poll-timeout": 30
"reject-on-missing-auth-method":true
}
],
Enrolling in IBM Verify
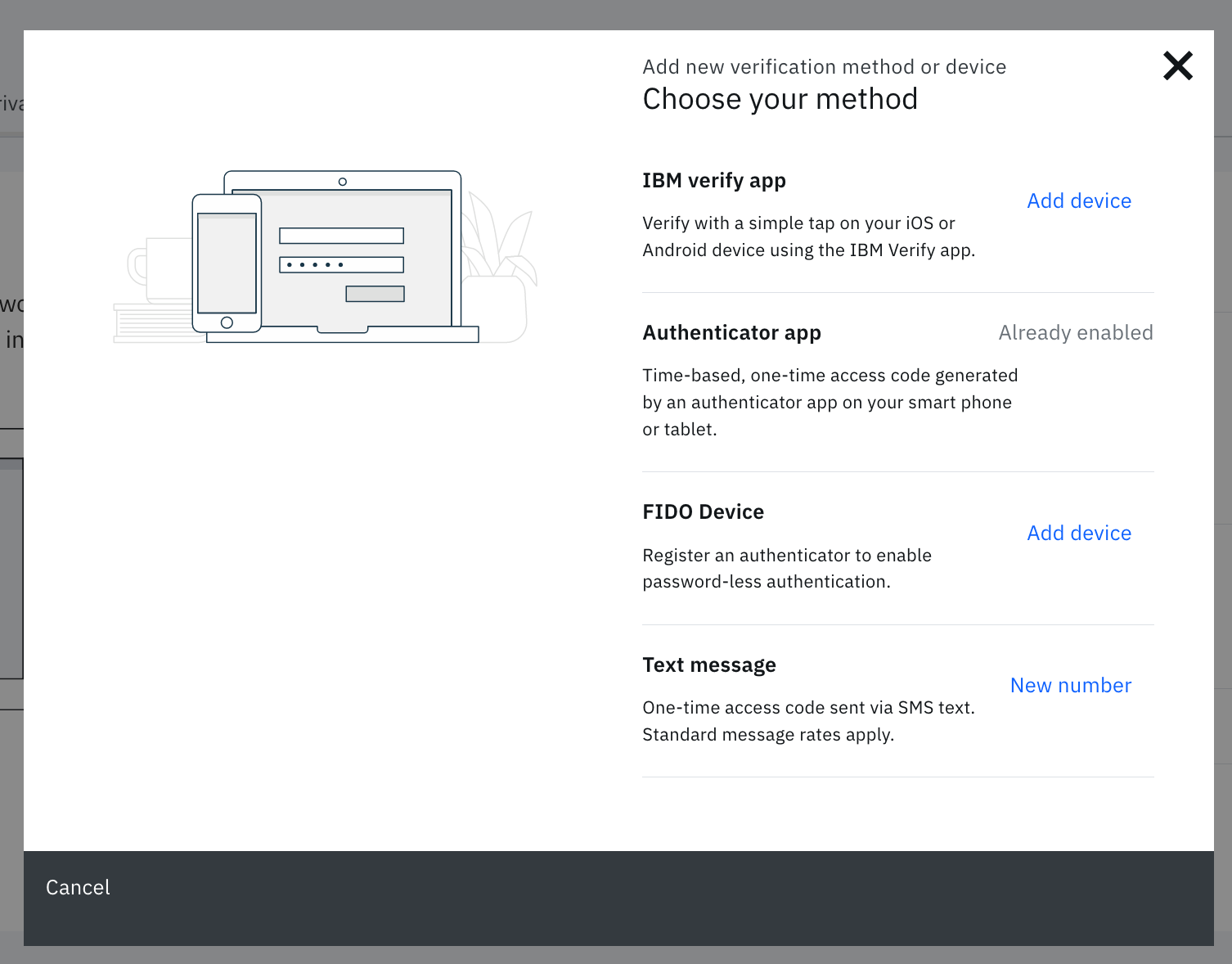
User enrollment in IBM Verify and other methods is very straight forward. All users can authenticate to and add new factors using the wizard:
https://yourtenant.ice.ibmcloud.com/usc/settings/security
Outside of the preferred IBM Verify methods, we support SMS, Email, and Time-based OTP (ex. Google Authenticator). FIDO2 unfortunately cannot be used at this time for RADIUS authentication, but it can drastically improve user experience to authenticate to cloud applications.
Dive deeper
There are a number of resources at your disposal to dive into more advanced use cases.
- Take the MFA everywhere course in Security Learning Academy to get hands on with the IBM Verify Gateway for RADIUS.
- View other IBM Verify integrations on XForce Exchange.
- IBM Verify Gateway for PAM (on Linux)
- IBM Verify Gateway for PAM (on AIX)
- IBM Verify Gateway for Windows Login
IBM Verify can protect almost any enterprise system and network with a wide variety of MFA options for extensible security for remote connectivity. With IBM Verify configured in your environment, you easily layer in MFA without drastic changes to your architecture. Leverage the power of IBM Cloud Identity to provide you with easy patterns to secure your perimeter.
#CloudIdentity