Using Cloud Identity as an identity provider for ADFS during mobile sign-on for passwordless authentication in a zero trust architecture.
In order to take full advantage of IBM Cloud Identity, IBM MaaS360, and your current Active Directory Federation Service (ADFS) architecture / investment, there are a few things to understand. First, IBM Cloud Identity will become an alternate Identity Provider to ADFS. Meaning when ADFS detects the user agent is mobile based, it will redirect the authentication request over to IBM Cloud Identity to handle to the rest. IBM MaaS360 is used in this pattern because it provides you the mobile device management security component, which delivers compliance and enrollment information to IBM Cloud Identity.
ADFS has about 30% of the overall federation market, simply because it's convenient to install, works with your current Microsoft investment, and most companies are entitled to it through their Microsoft licenses. While IBM Cloud Identity is a full Identity as a Service provider, delivering easy SSO and MFA options that enrich your security prospectus, it is important to work hand in hand with our customer's current deployment models. This guide will demonstrate how to accomplish integrating all three into one cohesive, zero-trust, architecture without impacting your day to day business operations.
Table of Contents
- Architecture Overview
- User Experience
- Prerequisites
- Enable the Identity Service and MDM policy in IBM MaaS360 for Single Sign-on
- Configure IBM Cloud Identity as an Claims Provider Trust (identity provider) in ADFS
- Configure ADFS as an application (service provider) in IBM Cloud Identity
- Redirect mobile authentication to IBM Cloud Identity for conditional access
- Add additional ADFS protected apps to IBM MaaS360 for SSO
- Test the mobile authentication flow
Architecture Overview
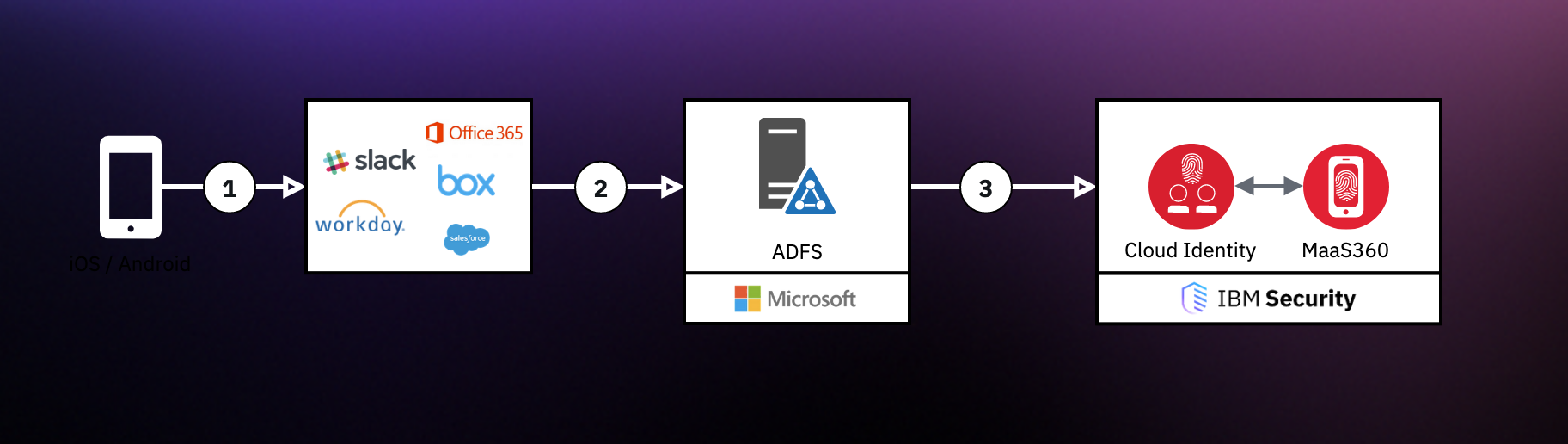
Communication path:
- Device (iOS or Android) accesses an application protected with ADFS
- The application (ex. Office365) redirects the user over to ADFS for authentication
- ADFS detects that the device is mobile, and redirects the authentication request over to IBM Cloud Identity
Given IBM Cloud Identity handles the mobile authentication logic and requires a certificate for authentication, the mobile device will present it upon request. If the mobile authentication fails, you can either have IBM Cloud Identity perform username / password authentication or simply outright block the request.
IBM Cloud Identity uses a certificate, installed on the device via IBM MaaS360, to validate the device is enrolled, and compliant.
User Experience
| Mobile (Passwordless) |
Desktop (Basic User/Password) |
 |
 |
Prerequisites
Understand that this modification is a global change, meaning all authentication on mobile will be redirected to IBM Cloud Identity. You can modify the onload.js in the theme for ADFS to look at the URL request and make a logical decision as well. However, for this guide, we are going to make a global change. We'll explain how to segment this in a later guide.
Requirements:
1. ADFS configured as an Identity Source
2. IBM Cloud Identity + IBM MaaS360 (you can obtain trials for both via IBM Marketplace)
3. IBM MaaS360 with matching user data to Active Directory either via manual entry or IBM Cloud Extender
We will be using a MaaS360 instance with the username that matches the userPrincipalName of the user. The regex used in the ADFS claims rule will extract the username from the upn format and convert it to the Windows Account Name format. Using ADFS claim rules can provide you flexibility in how to convert the username from whatever format you have to what ADFS expects.
Enable the Identity Service and MDM policy in IBM MaaS360 for Single Sign-on
In order to obtain a IBM Cloud Identity and MaaS360 linked tenant, you need to provision the tenant via IBM MaaS360's services. This will allow device data to synchronize between the two systems.
Read more on enabling this service here.
Steps
- Login to the MaaS360 portal as an administrator.
- Navigate to SETUP, then select Services
- Find Identity and Access Management service.
- Enable it and click Configure.
- Enter a tenant name, this is a descriptor name for your tenant.
For example, if you enter bigblue, then your tenant will become bigblue.ice.ibmcloud.com. You should not enter in the full hostname of the URL.
- Enter your IBMid and then click Configure.
- Navigate to your tenant once the tenant has been successfully created to verify you can access IBM Cloud Identity as an administrator.
Note: If you support Windows 10 devices then you will see an additional checkbox for laptop conditional access. Only enable the laptop access if you want to use conditional access for Windows 10.
Configure IBM Cloud Identity as an Claims Provider Trust (identity provider) in ADFS
To allow ADFS to redirect authentication to IBM Cloud Identity, we need to onboard IBM Cloud Identity to ADFS as a Claim Provider Trust. This is also known as an Identity Provider in typical IAM terms.
Prerequisites
- Download your IBM Cloud Identity identity provider metadata from the following URL: https://yourtenant.ice.ibmcloud.com/appaccess/v1.0/templates/federations/metadata
Note: Replace yourtenant with your actual tenant name that was created.
Steps
- Log into your Windows server as an administrator that has ADFS management configured.
- Open the ADFS Management console.
- Right-click on "Claims Provider Trust" and click Add Claims Provider Trust. The wizard will open up. Click Start.
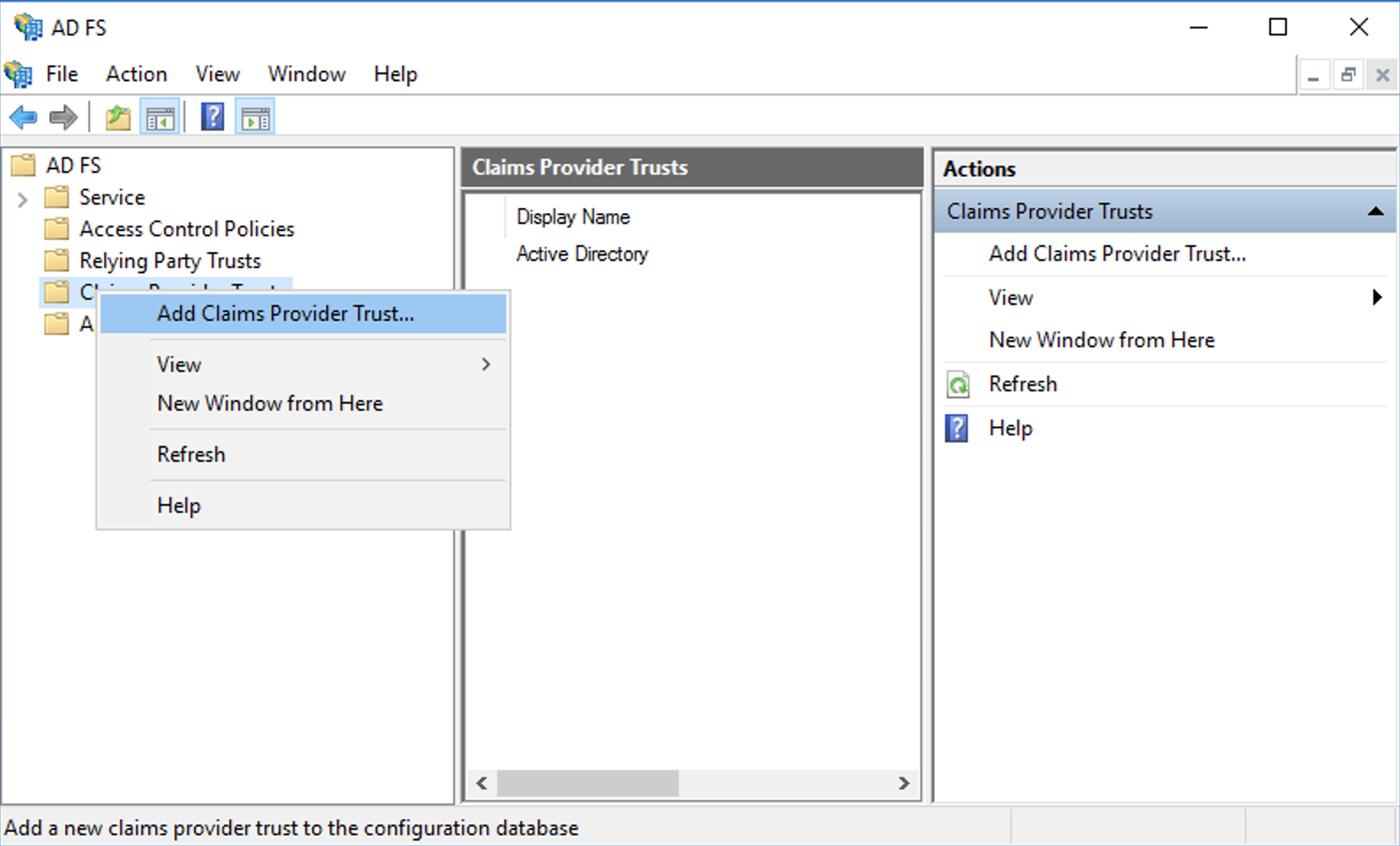
- Select the second radio button called "Import data about the claims provider from a file". Browse to your downloaded metadata from IBM Cloud Identity.
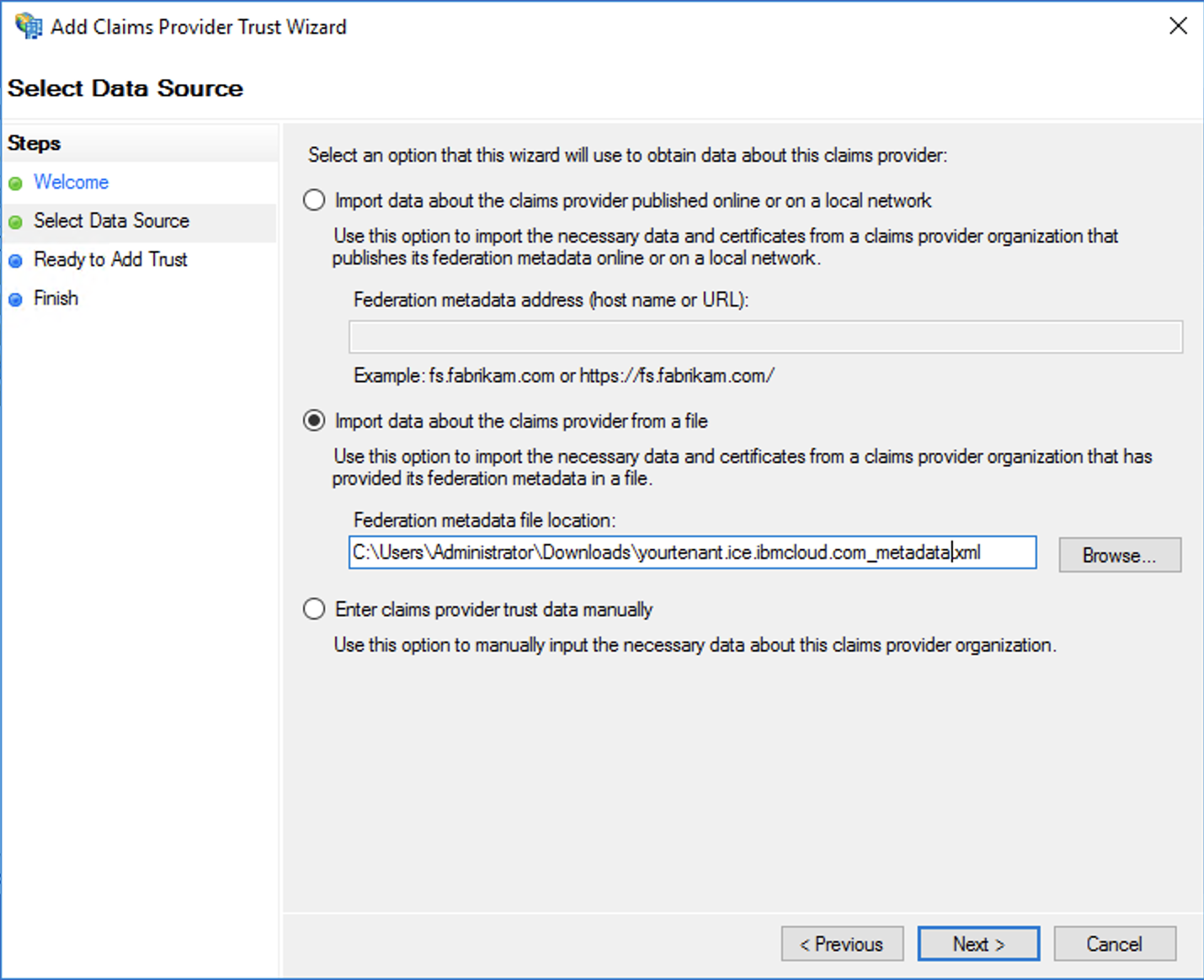
- Give the Identity Source a name. This is a descriptor name for reporting purposes.
- Review the configuration to ensure it matches what you would expect (ex. tenant name, certificate expirations, etc)
- Select the option to open the claims rule editor upon close. Click Close.
Claims rules for username mapping
Steps
- Click Add New to add a new claim rule
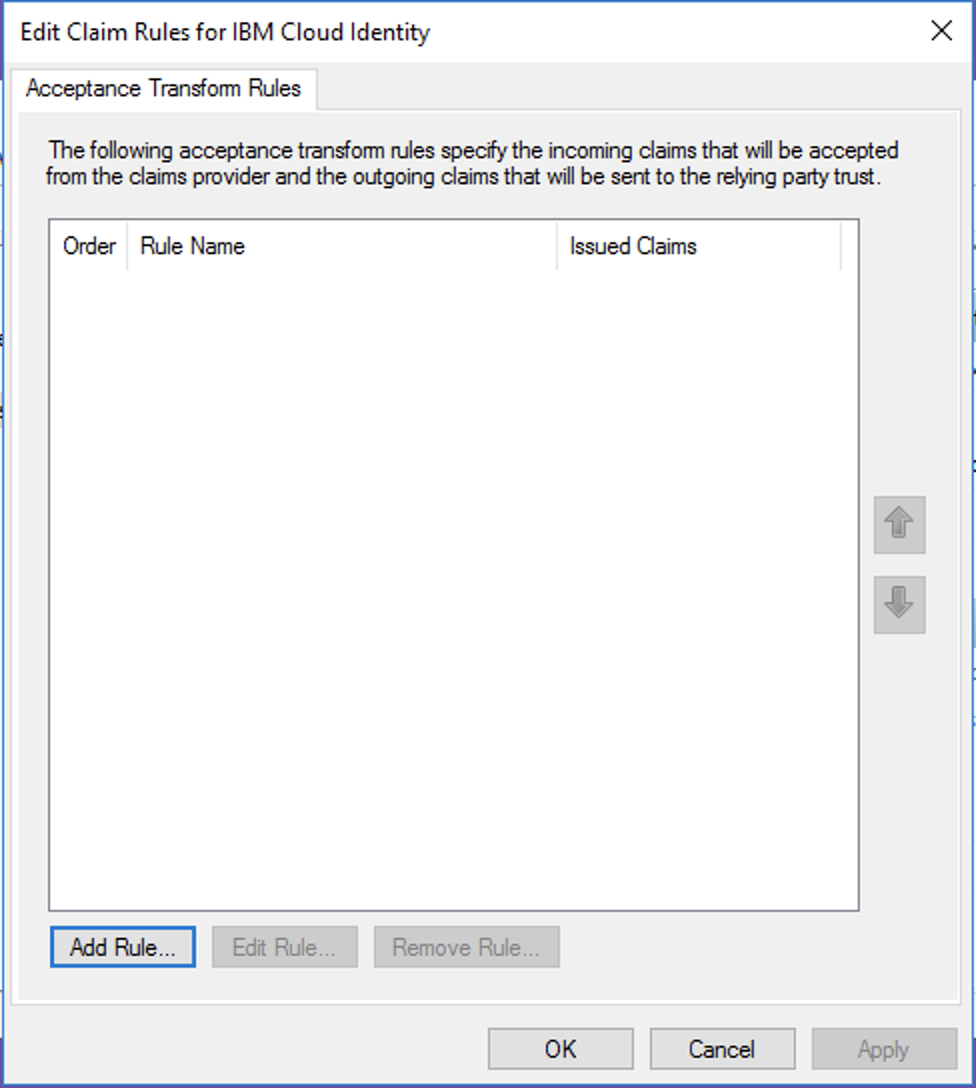
- Select the option "Send Claims Using a Custom Rule".
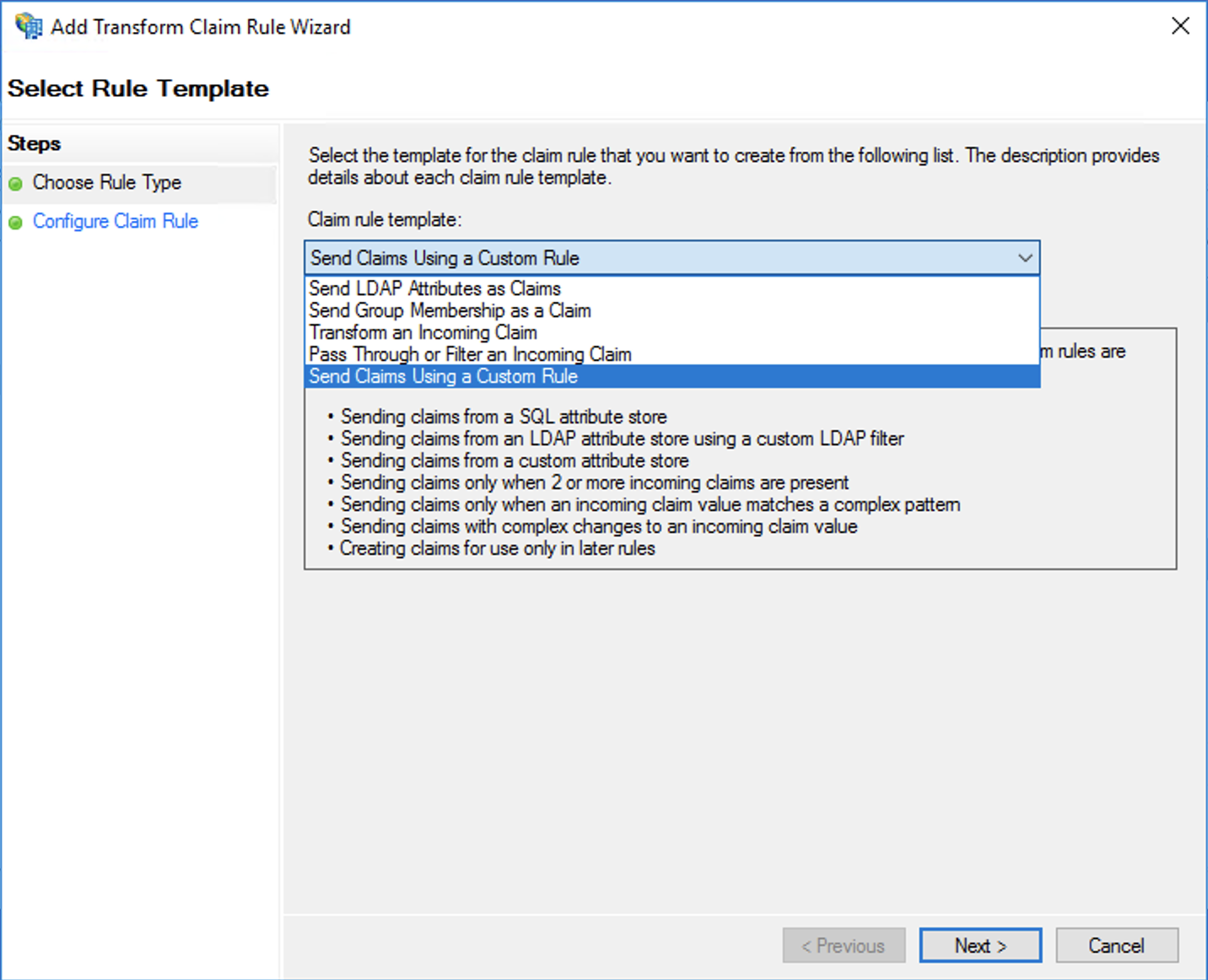
- Give the rule a name. In this case, we are transforming the MaaS360 username to Windows user name.
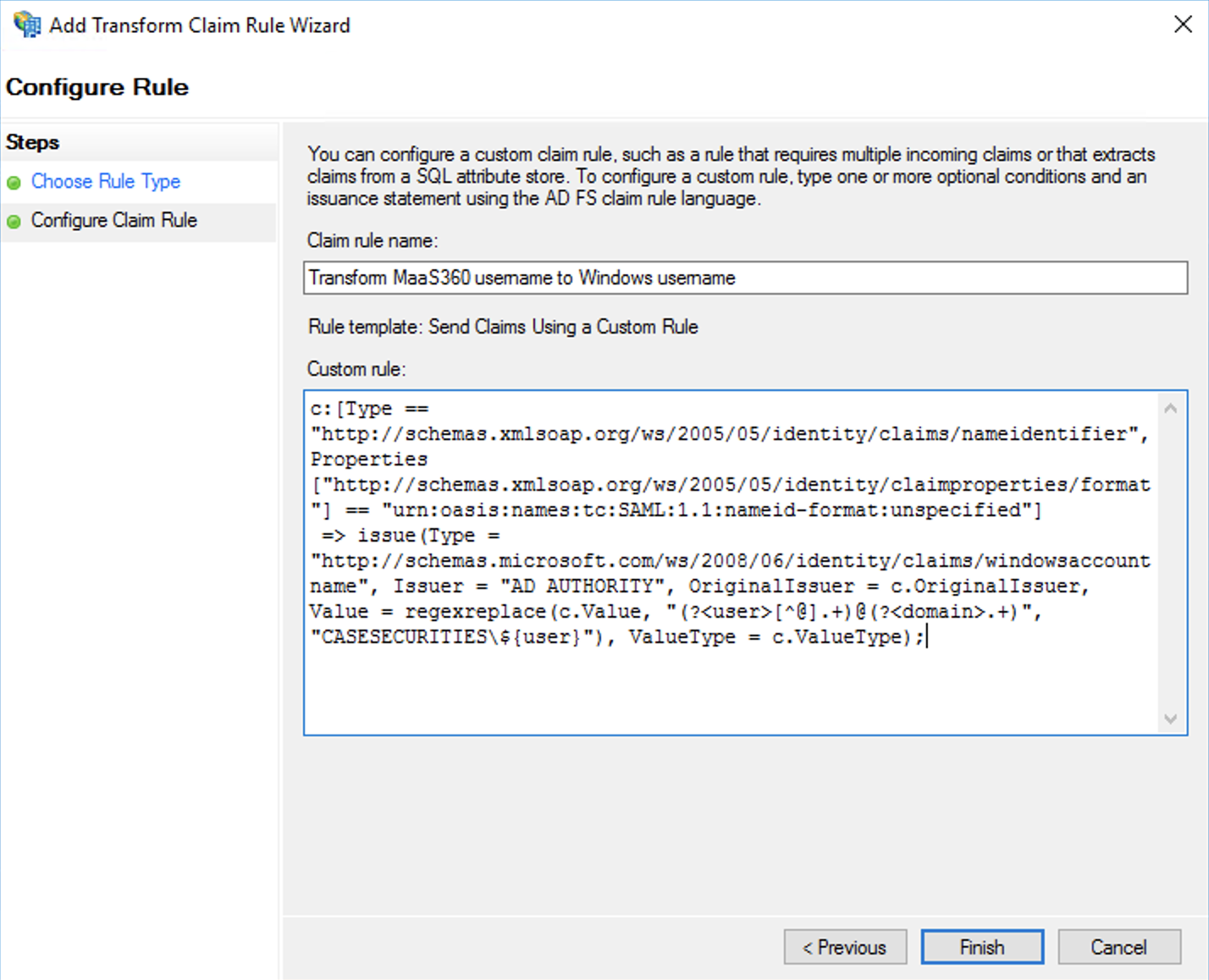
- Paste in the custom rule that matches your use case from below.
- Click Finish.
IBM MaaS360 synchronizes the user data from it's directory to IBM Cloud Identity. There a few patterns of username that can be used. Use the below mapping rule that matches your users the best:
Username is the userPrincipalName (UPN) attribute
Use the following claim in your claims rule. Replace the DOMAIN with your domain.
c:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] == "urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified"] => issue(Type = "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer = "AD AUTHORITY", OriginalIssuer = c.OriginalIssuer, Value = regexreplace(c.Value, "(?[^@].+)@(?.+)", "DOMAIN\${user}"), ValueType = c.ValueType);
Example from MaaS360:
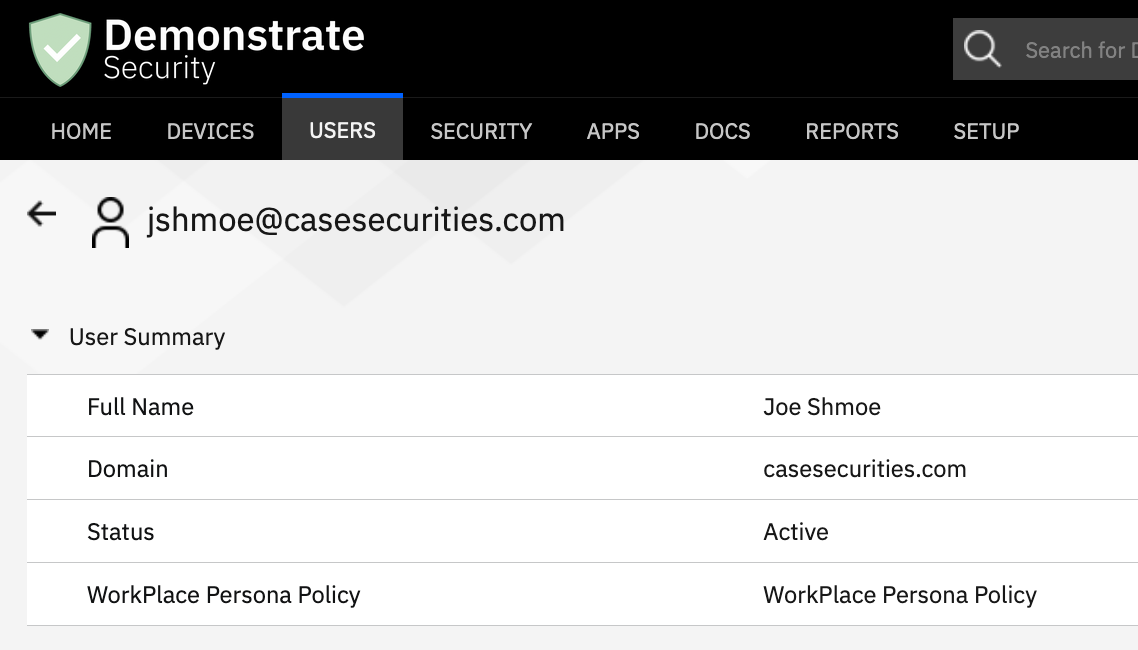
Username is the samAccountName attribute (without domain)
Use the following claim in your claims rule. Replace the DOMAIN with your domain.
c:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] == "urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified"] => issue(Type = "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer = "AD AUTHORITY", OriginalIssuer = c.OriginalIssuer, Value = regexreplace(c.Value, "(?.+)", "DOMAIN\${user}"), ValueType = c.ValueType);
Example from MaaS360:
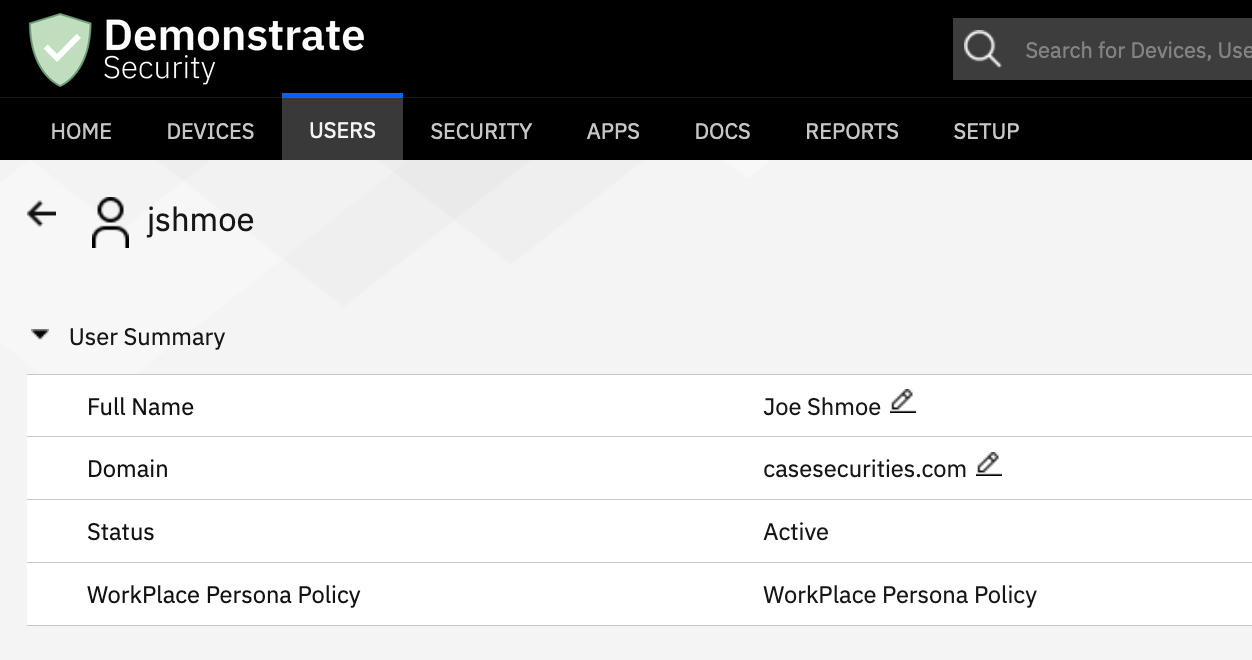
Username is the email address
If your username is the email address, ensure that another attribute matches either the UPN or samAccountName and follow the steps below on how to map the attribute to the preferred username.
Steps
- Login to IBM Cloud Identity as an administrator.
- Open the menu and navigate to Configuration.
- Select Identity Sources.
- Under the global settings section, select the proper attribute for Unique User Identifer from the drop down that is populated with either the UPN or samAccountName.
- Follow one of the prior claim rules that matches the attribute you selected.
Note: Read more here on these settings. Additional note, custom attributes cannot be used as unique idenfiers.
Configure ADFS as an application (service provider) in IBM Cloud Identity
For ADFS to successfully trust the authentication message coming back from IBM Cloud Identity, ADFS will need to be onboarded as an application (service provider).
Prerequisites
- Download the ADFS metadata. The standard URL by default for this is: https://sts.hostname.com/federationmetadata/2007-06/federationmetadata.xml
- Copy the entity ID, search for
entityID in the XML file. Ex. https://sts.hostname.com/adfs/services/trust
- Copy the AssertionConsumerService Location URL, search for
AssertionConsumerService Location in the XML file. Ex. https://sts.hostname.com/adfs/ls/
Steps
- Login to your IBM Cloud Identity tenant as an administrator.
- Open the menu, navigate to Applications.
- Click Add Application.
- Select Custom Application from the list of available connectors.
- Provide the application a name, such as ADFS
- Provide a descriptor Organization Name; this is a required field.
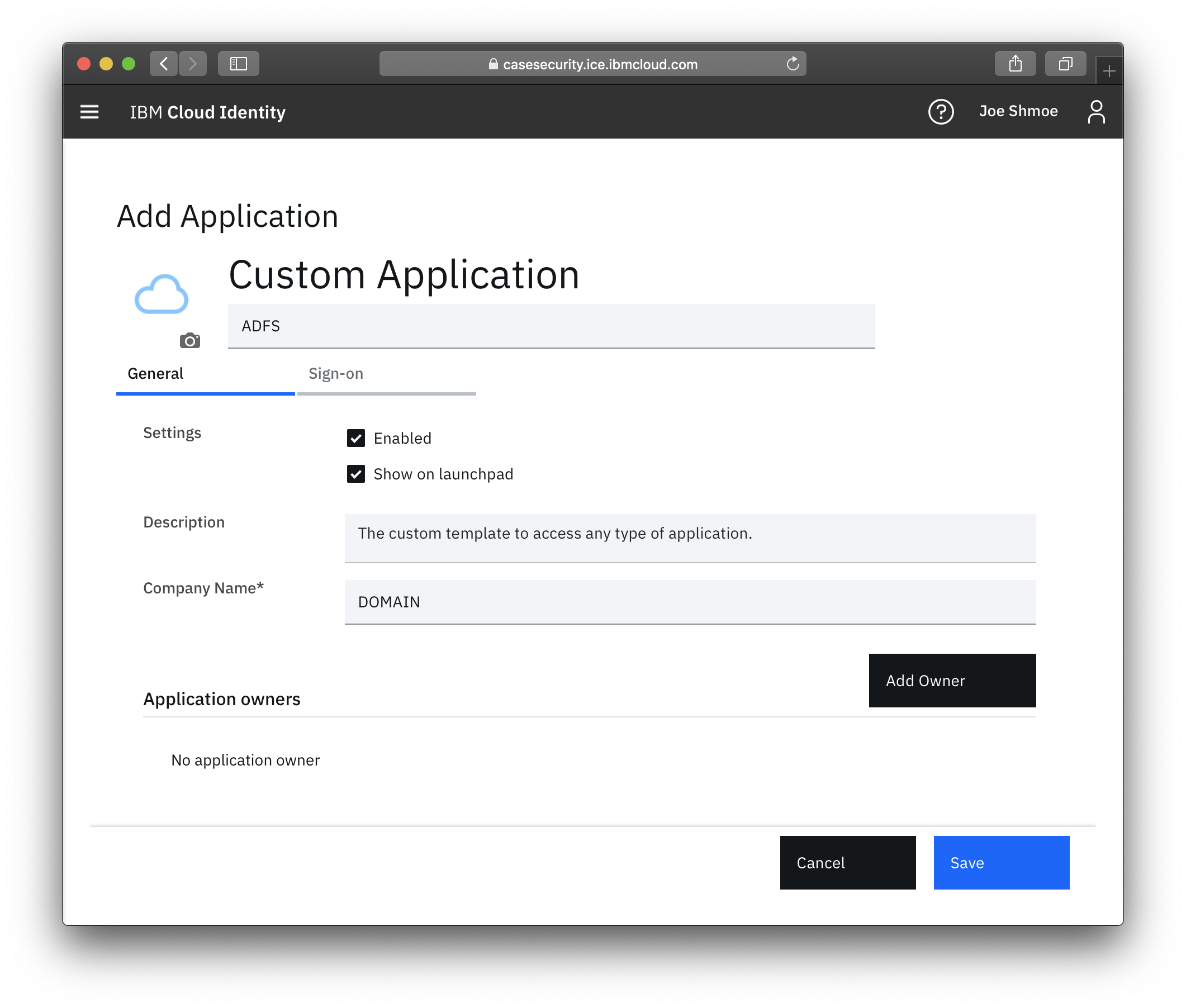
- Navigate to the Sign On tab.
- Enter the entity ID that was copied, and paste it into the Provider ID field.
- Enter the Assertion Consumer Service URL in the corresponding field.
- Check the box for "Identity provider initiated sign in".
- Scroll to the bottom of the configuration and under access policies, uncheck the box to select an access policy.
- Select an access policy that corresponds with your security requirements. To block all access unless the device is managed and compliant, select "Allow access from compliant devices only; block otherwise".
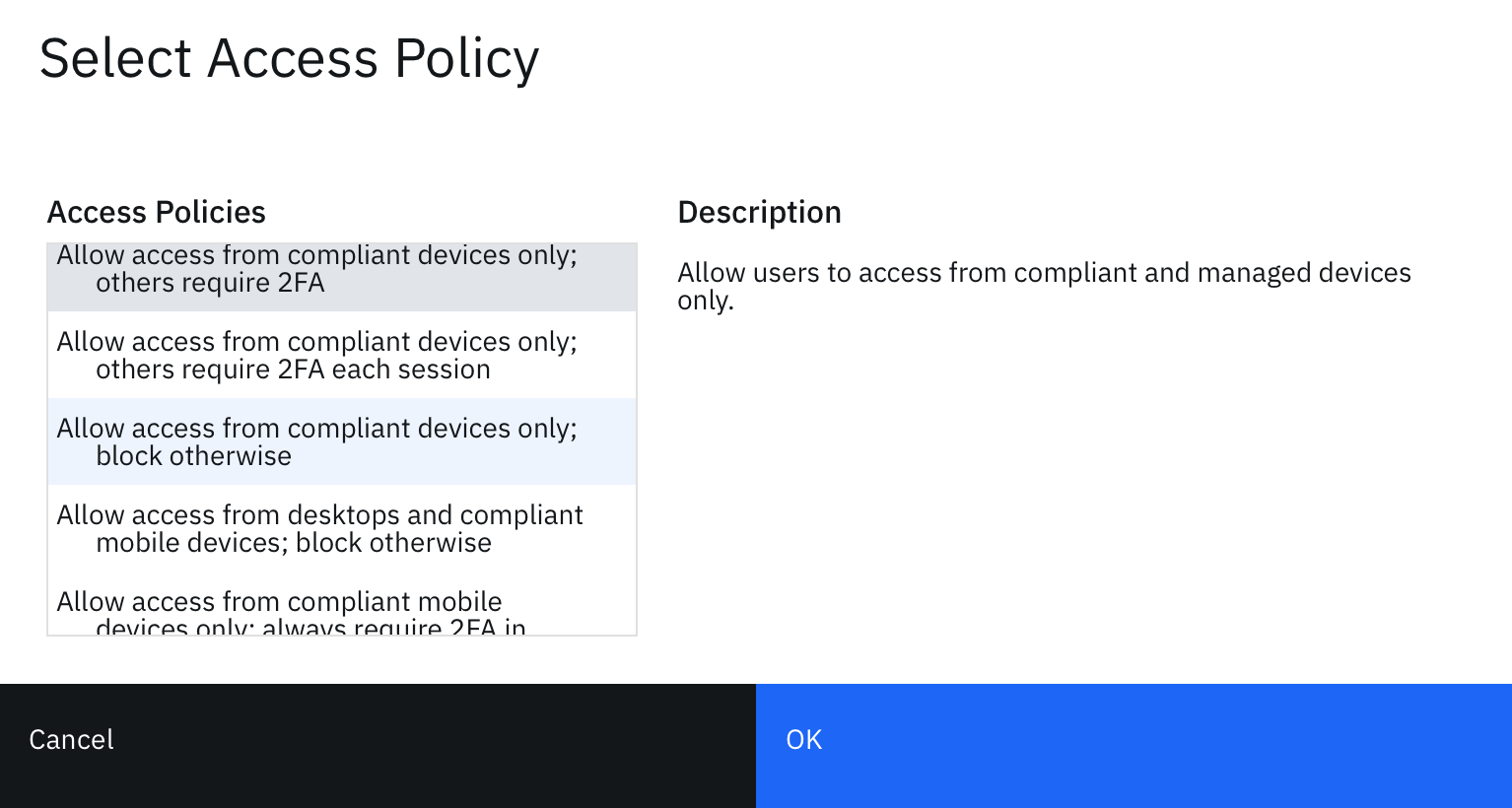
- Click OK when you're done making your selection.
- Click Save.
- Select the entitlements tab and entitle all users to this application.
- Click Save again.
Test the federated authentication flow
Steps
- Create a local user in Cloud Identity to test with.
- In a separate browser session, go to your IdP intiiated login URL for ADFS. Ex. https://sts.hostname.com/adfs/ls/IdpInitiatedSignon.aspx
- Select IBM Cloud Identity from the list.

- Login with the test user you created.
- The test would be successful if you have an established ADFS session.
Note: To debug this issue, onboard the RSA application as a Relying Party Trust in ADFS to verify the session was established
Redirect mobile authentication to IBM Cloud Identity for conditional access
In order to capture the authentication request and forward the request to an alternate identity source, you will need to modify the onload.js file on the Theme applied to ADFS.
Prerequisites
- Ensure the test was successful between IBM Cloud Identity and ADFS.
Steps
- Log into the server that is configured for ADFS Management as an Administrator.
- Open powershell as an Administrator.
- Run the command
mkdir c:\ibmci\.
- Run the following command to download the current default ADFS theme to the folder:
Export-AdfsWebTheme –Name "Default" –DirectoryPath c:\ibmci
- Open the following file in a text editor:
C:\ibmci\script\onload.js
-
Right after "use strict" line, paste the following code snippet. Replace the yourtenant information with your hostname.
var captureHeader = document.getElementById('hrdArea');
if (captureHeader) {
/* If user agent matches, redirect to IBM Cloud Identity */
if (navigator.userAgent.match(/iPad|iPhone|Android/i) != null) {
HRD.selection('https://yourtenant.ice.ibmcloud.com/saml/sps/saml20ip/saml20');
}
/* If user agent does not matches, perform normal username/password authentication */
else {
HRD.selection('AD AUTHORITY');
}
}
/* Hide the authentication selection from the user. */
var selectorui = document.getElementById("bySelection");
selectorui.style.display = "none";
-
Save the file, ensure you overwrite the old onload.js file.
-
In powershell, create a new theme by duplicating the Default template:
New-AdfsWebTheme –Name "IBMCI" –SourceName "Default"
-
Perform the following command to overwrite the onload.js in the new theme:
Set-AdfsWebTheme -TargetName "IBMCI" -AdditionalFileResource @{Uri='/adfs/portal/script/onload.js';path="c:\ibmci\script\onload.js"}
-
Set the new theme to active
Set-AdfsWebConfig -ActiveThemeName "IBMCI"
Note: You always have the ability to revert back to the default theme by replacing "IBMCI" with "Default" and running the command again.
-
Restart the ADFS service to set the theme. You can do this through services.msc or running this command: Restart-Service adfssrv
Important: This is a global change to the Theme. If you only want to apply the mobile redirect on specific applications, additional modificiations to the onload.js will be needed to look at the URL being requested. A tutorial on modifying themes based on relying party are found here: https://blogs.technet.microsoft.com/pie/2015/08/29/customizing-the-ad-fs-sign-in-pages-per-relying-party-trust/
Add additional ADFS protected apps to IBM MaaS360 for SSO
In the MaaS360 portal, you must add the mobile apps to the MaaS360 App Catalog and set the app for Enterprise Single Sign On. If you have an existing application in the catalog, you can edit the application entry and check the box for "Enterprise Single Sign on".
For example, if you wanted to protect an application like Office365, you must add the Office365 mobile app to the MaaS360 App Catalog and check the box for Enable Enterprise single sign-on.
Additionally, you must enable the MDM policy for Single Sign on for both Android and iOS. Add the applications you wish to entitle to the MDM policy. This is an explicit permission. If the app is not included in the MDM payload, the certificate used to authenticate will fail to work.
The apps display in the Application Name selection based on Enterprise Single sign being checked in the App Catalog. After you save and publish the policy, the updated policy must be assigned to the mobile devices to take advantage of SSO and conditional access. This can be accomplished by setting the policy as the default, assigning the policy to a device group or single device.
Test the mobile authentication flow
Prerequisites
- Cloud Identity is successfuly configured as Claims provider trust in ADFS
- ADFS is an application in Cloud Identity
- MaaS360's applications are enabled for Enterprise Single Sign on
- MaaS360's MDM policies are configured for Single Sign on and distributed to devices.
Steps
- Using a device that is enrolled in IBM MaaS360, open an application that uses ADFS as an authentication provider or navigate in Safari/Chrome to the website protected with ADFS.
- Attempt the authentication.
If your authentication is successful then you will not see any username/password field in ADFS, nor in IBM Cloud Identity.
If you see an IBM Cloud Identity login page, that means that your certificate is not valid or installed, or the MDM payload is missing from your device.
#CloudIdentity