Pulling event log details from Cloud Identity
 Obtaining event detail from your IBM Cloud Identity tenant is as simple as two API calls which allows your SIEM or analytics tool to consume all events from the Cloud Identity platform. As we improve and add to the platform, more events may become available. The current report types that exist:
Obtaining event detail from your IBM Cloud Identity tenant is as simple as two API calls which allows your SIEM or analytics tool to consume all events from the Cloud Identity platform. As we improve and add to the platform, more events may become available. The current report types that exist:
- Management events /
management / This includes changes to user records, application modifications, API modifications, etc.
- Authentication events /
authentication / Users authenticating to the Cloud Identity platform.
- Single-Sign on events /
sso / Outbound single-sign on to OpenID Connect and SAML2.0
The IBM Cloud Identity event API allows for:
- Page sizing
- Filtering on event types (e.g. management, authentication, sso)
- Resource filtering (e.g. user, token, app_consent)
- Time span filtering (i.e. searching after a time, or between times)
The events API will max out at 10,000 events in the response. The API provides a simple way to allow you to make subsequent calls with ease. It includes a search_after object which includes a time and id which represents the last event in the current call, which allows you to make a second call that will not overlap events.
Events are sorted by newest events to oldest events. If using page sizing, then you will get the most recent events in that page size. e.g If you have a size limit of 2 events out of 10, then you will get the most recent 2 events out of the 10.
Pre-requisites
To make any API call you need an access token. The “Getting started with IBM Cloud Identity REST APIs” article helps you through the requisite steps in setting up an API Client and obtaining an access token: Getting started with IBM Cloud Identity Rest APIs.
Note: The API client used to obtain the access token must have the ”Manage reports" access enabled, at a minimum for this particular exercise.
Scenario 1 / Get all events
The simplest call to make is get all events from the platform without filters. Though in larger environments, you will likely get over 10,000 records. We'll discuss handling pagination in a later section.
API Endpoint: GET /v1.0/events
Make the call:
curl -X GET \
https://mytenant.ice.ibmcloud.com/v1.0/events \
-H 'Authorization: Bearer myAccessTokentzkhVdRO8FE6f08CTKny4AbUl18'
Expected response:
{
"response":{
"events":{
"search_after":{
"total_events":54,
"max_size_limit":"false",
"time":"1559156150862",
"id":"def9ea72-30ce-4589-800a-7306e306ea2e"
},
"events":[
{
"geoip":{
"continent_name":"North America",
"country_iso_code":"US",
"country_name":"United States",
"location":{
"lon":"-97.822",
"lat":"37.751"
}
},
{
...
},
{
...
},
{
...
}
}
...
Scenario 2 / Get events from specific event types
To filter on specific events on certain types, we'll use a filter query string.
The query string for this call will include event_type.
Each event type will need to be escaped with \" on each side of the value.
\"management\" corresponds with management events\"authentication\" corresponds with authentication events into the CI platform.\"sso\" corresponds with SSO events.
API Endpoint: GET /v1.0/events?event_type=\"sso\"
You may string multiple together to mulitples event types together, separated by commas. For example: event_type=\"sso\",\"authentication\"
Handling pagination (max records)
If your call response includes total_events that exceed the total events count in the response, or "max_size_limit": "true", you can make a second call with a filter as to not overlap with the first call.
For example, if the first call we made was:
GET https://mytenant.ice.ibmcloud.com/v1.0/events with a response of:
{
"response":{
"events":{
"search_after":{
"total_events":19540,
"max_size_limit":"true",
"time":"1559156150862",
"id":"def9ea72-30ce-4589-800a-7306e306ea2e"
},
We know that:
- The response includes 10,000 records, and
- We've hit the max size limit, and
- The last event in the reponse has the time of
1559156150862 and id of def9ea72-30ce-4589-800a-7306e306ea2e.
- If using the "from" or "to" parameter, also include that parameter in the call also.
Therefore, our next call will look like:
GET /v1.0/events?after=\"1559156150862\",\"def9ea72-30ce-4589-800a-7306e306ea2e\" which responds with:
{
"response":{
"events":{
"search_after":{
"total_events":19450,
"max_size_limit":"false",
"time":"1559227423000",
"id":"f253f26d-bb00-497b-a508-b3ea0e4f6d6f"
}
}
When max size limit is false, then we know we do not need to make an additional call. If you are also using page sizing though, and your size is less than 10,000 then it will always say max_size_limit = false.
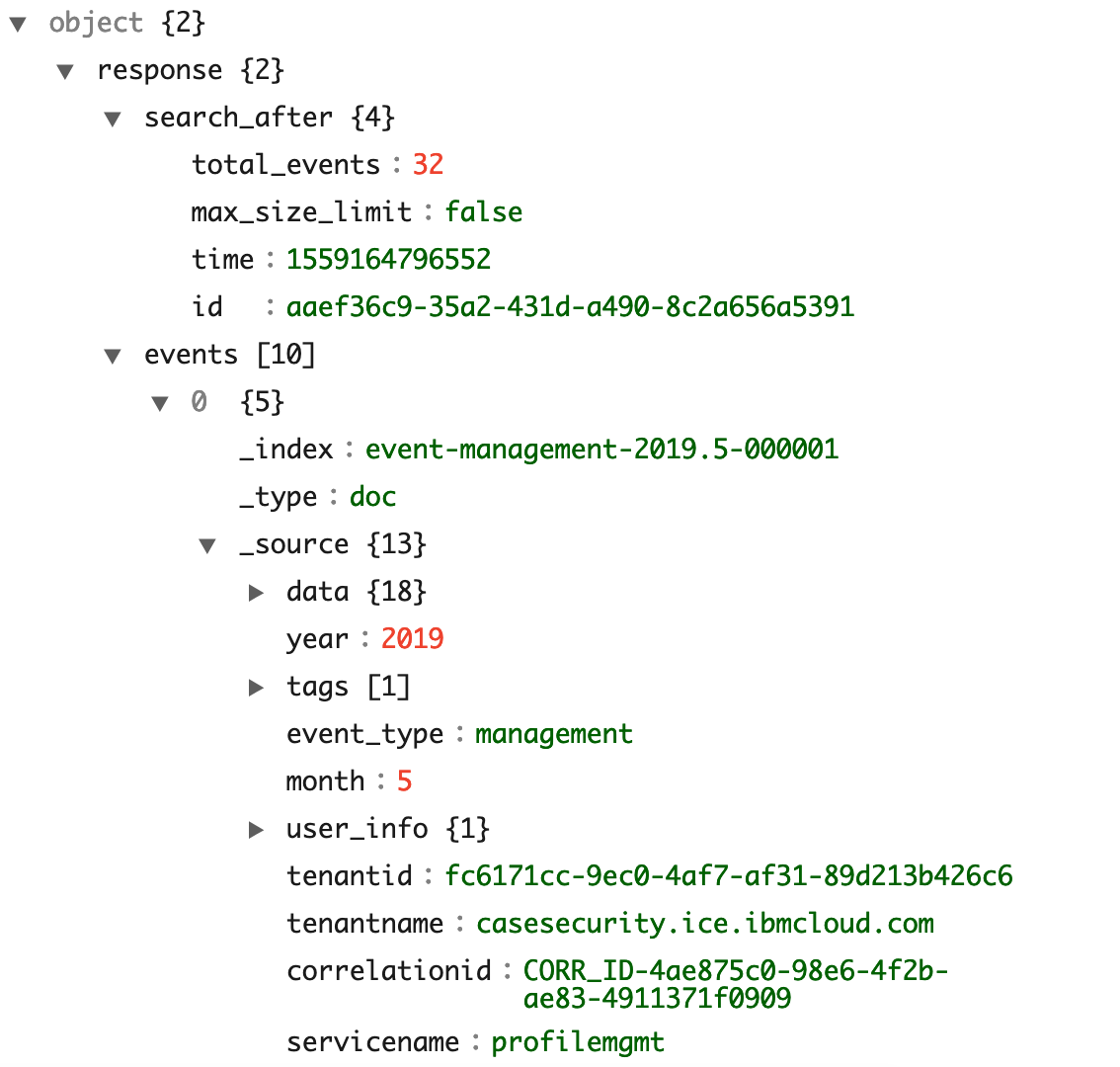
API Response Schema
In response, reference the below schema to understand what each component in the object does. There are two main objects under the response object, search_after and events
search_after
total_events / Includes the total number of events within the time range or if not time range is specified, then the number of lifetime events.
max_size_limit / If the current response is 10,000 records, this will turn to true.
time / In epoch unix format, this attribute represents the last event timestamp in the current response.
id / This is the last event identifier in the current response.
events
Types of data depends on what resource is returned but here are examples of the three event types.
Management events
{
"data":{
"targetid_realm":"cloudIdentityRealm",
"api_grant_type":"urn:ibm:params:oauth:grant-type:apikey",
"targetid_username":"user@domain.com",
"performedby_type":"intraservice",
"targetid":"600000AVWG",
"resource":"user",
"origin":"10.125.127.163",
"cause":"The system modified the user \"user@domain.com\".",
"messageid":"CSIAI1022I",
"userinfo_lookup_field":"targetid",
"devicetype":"Apache-HttpClient/4.5.2 (Java/1.8.0_161)",
"result":"success",
"performedby":"shared_apikey",
"json":"<jsonData>",
"action":"modified",
"self":"false",
"location":"https://<tenant>/cdprofilemgmt/v2.0/Users/600000AVWG",
"realm":"cloudIdentityRealm"
},
"year":2019,
"tags":[
"_geoip_lookup_failed-lookup_failed"
],
"event_type":"management",
"month":5,
"user_info":{
"targetid":{
"realm":"cloudIdentityRealm",
"userid":"600000AVWG",
"username":"user@domain.com"
}
},
"tenantid":"ba1dc906-53d6-48ec-be0d-4e05d4ec9752",
"tenantname":"<tenant>",
"correlationid":"DefaultContext",
"servicename":"profilemgmt",
"id":"1186c0f1-6769-4fdd-82db-ecc8e8e148b3",
"time":1558721144307,
"day":24
}
Authentication events
{
"event_type": "authentication",
"data": {
"api_grant_type": "urn:ibm:params:oauth:grant-type:apikey",
"performedby_type": "intraservice",
"sourceinstance": "clouddirectory",
"subject": "6000001O8M",
"origin": "10.125.127.135",
"cause": "Authenticated user \"user\" successfully.",
"messageid": "CSIAM1030I",
"devicetype": "Apache-HttpClient/4.5.2 (Java/1.8.0_161)",
"result": "success",
"performedby": "shared_apikey",
"location": "https://<tenant>/cdprofilemgmt/v2.0/Users/authentication",
"sourcetype": "clouddirectory",
"realm": "cloudIdentityRealm",
"username": "user"
},
"month": 5,
"year": 2019,
"tenantid": "ba1dc906-53d6-48ec-be0d-4e05d4ec9752",
"tenantname": "<tenant>",
"correlationid": "CORR_ID-ed592d9a-be04-4dc8-84e2-a65bd2093e3b",
"servicename": "profilemgmt",
"id": "5aeb9b37-0e04-47dc-982a-ea71dbc620ec",
"time": 1559156269126,
"day": 29,
"tags": [
"_geoip_lookup_failed-lookup_failed"
]
}
SSO events
{
"geoip": {
"continent_name": "North America",
"country_iso_code": "US",
"country_name": "United States",
"location": {
"lon": "-97.822",
"lat": "37.751"
}
},
"data": {
"origin": "76.224.107.171",
"count": 1,
"samlassertion": "<saml:Assertion xmlns:saml=\"urn:oasis:names:tc:SAML:2.0:assertion\" ID=\"Assertion-uuid9dcfa216-016a-10ee-bf79-df9724a49584\" IssueInstant=\"2019-05-09T18:16:31Z\" Version=\"2.0\" xmlns:xs=\"http://www.w3.org/2001/XMLSchema\" xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\"><saml:Issuer Format=\"urn:oasis:names:tc:SAML:2.0:nameid-format:entity\">https://tenant.ice.ibmcloud.com/saml/sps/saml20ip/saml20</saml:Issuer><saml:Subject><saml:NameID Format=\"urn:oasis:names:tc:SAML:2.0:nameid-format:persistent\">SmVzc2ljYQ==</saml:NameID><saml:SubjectConfirmation Method=\"urn:oasis:names:tc:SAML:2.0:cm:bearer\"><saml:SubjectConfirmationData NotOnOrAfter=\"2019-05-09T18:17:31Z\" Recipient=\"https://provider/acs\"/></saml:SubjectConfirmation></saml:Subject><saml:Conditions NotBefore=\"2019-05-09T18:15:31Z\" NotOnOrAfter=\"2019-05-09T18:17:31Z\"><saml:AudienceRestriction><saml:Audience>https://provider</saml:Audience></saml:AudienceRestriction></saml:Conditions><saml:AuthnStatement AuthnInstant=\"2019-05-09T18:16:31Z\" SessionIndex=\"uuid9dcf9a83-016a-17c2-b2b4-df9724a49584\" SessionNotOnOrAfter=\"2019-05-09T19:16:31Z\"><saml:AuthnContext><saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:Password</saml:AuthnContextClassRef></saml:AuthnContext></saml:AuthnStatement><saml:AttributeStatement><saml:Attribute Name=\"Email\" NameFormat=\"urn:oasis:names:tc:SAML:2.0:attrname-format:basic\"><saml:AttributeValue xsi:type=\"xs:string\">jessica.chains@yopmail.com</saml:AttributeValue></saml:Attribute><saml:Attribute Name=\"LastName\" NameFormat=\"urn:oasis:names:tc:SAML:2.0:attrname-format:basic\"><saml:AttributeValue xsi:type=\"xs:string\">Chains</saml:AttributeValue></saml:Attribute><saml:Attribute Name=\"FirstName\" NameFormat=\"urn:oasis:names:tc:SAML:2.0:attrname-format:basic\"><saml:AttributeValue xsi:type=\"xs:string\">Jessica</saml:AttributeValue></saml:Attribute></saml:AttributeStatement></saml:Assertion>",
"userid": "6000009XUX",
"devicetype": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:66.0) Gecko/20100101 Firefox/66.0",
"applicationname": "DocuSign",
"result": "success",
"subtype": "saml",
"providerid": "https://provider",
"host": "saml_runtime",
"realm": "cloudIdentityRealm",
"applicationid": "2698567225614820916",
"applicationtype": "DocuSign",
"username": "jessica@domain.com"
},
"year": 2019,
"event_type": "sso",
"month": 5,
"tenantid": "ba1dc906-53d6-48ec-be0d-4e05d4ec9752",
"tenantname": "tenant.ice.ibmcloud.com",
"correlationid": "CORR_ID-d82748cd-6802-488b-bd81-e789809e4f37",
"servicename": "saml_runtime",
"id": "2a6f3d31-09c0-4b1b-88aa-e2d678c1d25d",
"time": 1557425791967,
"application_info": {
"name": "DocuSign",
"type": "DocuSign"
},
"day": 9
}