Welcome back to our OpenShift Pipelines as Code series! If you've been following along, we're thrilled to have you back for another exciting installment. In this blog, we're diving deep into the nitty-gritty of verifying OpenShift Pipelines as Code with GitHub on IBM Power. So, fasten your seatbelts as we guide you through the steps to achieve this technical feat.
In our previous blog, Red Hat OpenShift Pipelines as Code on IBM Power, we introduced you to the captivating world of Pipelines as Code (PAC ), giving you a glimpse of what's possible. Today, we’ll provide the detailed steps to make PAC and GitHub work together.
Initially, PAC was integrated with GitHub, and later extended to GitLab and Bitbucket. Now, we're zooming in on PAC and GitHub's partnership. To make this magic happen, all you need is your source code residing in a GitHub repository. A simple commit or a pull request triggers the pipeline, and you can watch the action unfold on your OpenShift cluster.
In our previous blog, we introduced PAC's inner workings, configuration essentials, and the prerequisites you need to have in place. We even walked you through some common steps to implement PAC with different repositories. Remember when we mentioned that we'd present you with a real working example? Well, it's time to deliver on that promise! Brace yourselves for a GitHub repository example that'll bring PAC to life.
Unveiling the Steps: Implementing PAC on IBM Power with GitHub
Before we dive into the action, make sure you have a GitHub account. If you're not already part of the GitHub community, head over to GitHub and follow the simple prompts to create your account. Once you're in, you're ready to roll!
Let's jog your memory with a quick recap of the steps we covered in our previous blog:
- Create a GitHub application using the ‘tkn pac bootstrap’ command on your machine.
- Create a GitHub repository through the GitHub UI.
- Generate a personal access token within your GitHub repository.
- Clone the GitHub repository to your local machine.
- Use ‘tkn pac create repo’ command to create a PAC repository.
- Commit your changes and push them to your remote Git repository.
- Raise a pull request or commit your changes to the main branch of your repository.
Now, let’s discuss each step in detail.
Step 1: Create a GitHub application.
The journey begins by creating your very own GitHub application. This application acts as the integration with OpenShift Pipelines and fetches the Git workflow into Tekton pipelines. Remember, for every user on the cluster, you'll need a GitHub application to facilitate the connection.
You must ensure that the GitHub application's webhook points toward your Pipelines as Code Controller route or the ingress endpoint which would listen to the GitHub events.
One way to make a GitHub application is by using PAC to bootstrap application creation. Here's a breakdown of the process:
- On your command line, enter the ‘tkn pac bootstrap’ command, and you'll be prompted to provide details such as GitHub app name and the Webhook controller URL (the smee URL created as part of the pre-requisites section in our previous blog).
Refer to the following example for better understanding.
# tkn pac bootstrap
🏃 Checking if Pipelines as Code is installed.
👌 Pipelines as Code is already installed.
? Enter the name of your GitHub application: pac-191-412
👀 I have detected an OpenShift Route on: https://pipelines-as-code-controller-OpenShift-pipelines.apps.ppc64le.com
? Do you want me to use it? No
? Enter your public route URL: https://smee.io/yusJJWw9d9vQ
🌍 Starting a web browser on http://localhost:8080, click on the button to create your GitHub APP
🔑 Secret pipelines-as-code-secret has been created in the OpenShift-pipelines namespace
🚀 You can now add your newly created application on your repository by going to this URL:
https://github.com/apps/pac-191-412
💡 Don't forget to run the "tkn pac create repo" to create a new Repository CRD on your cluster.
A secret named `pipelines-as-code-secret’ is created in the OpenShift-pipelines namespace on your OpenShift cluster. It contains the GitHub application ID, GitHub private key, and webhook secret.
- Open your web browser and head to http://localhost:8080.
Note: Use IP address of your machine if localhost doesn’t respond.
- Click Create your GitHub App
- Enter a name for your GitHub Application, and then click Create GitHub app for <user>.
Step 2: Create a GitHub repository.
After successfully making your GitHub application, it's time to shift gears and begin creating a GitHub repository.
- Login to GitHub and navigate to your profile section. Select Your repositories.
- Click New to create a new repository.
- Specify the name of the repository in the Repository name field and fill in all the other details. Click Create repository to create a repository.
Step 3: Create a GitHub personal access token.
Now let us create a GitHub personal access token for OpenShift Pipelines as Code GitHub API operations as this can be used to create a secret in the OpenShift cluster in the upcoming steps.
- Login to GitHub and navigate to your profile section. Select Settings à Developer settings à Personal access Tokens à Fine-grained tokens. Specify the Token name and select the desired Expiration value.
Under Repository access section, select Only select repositories and select your repositories from the dropdown.
- Grant the required permissions and click Generate token to generate a token.
- Keep a note of the generated token since you may not view it again.
Step 4: Clone your GitHub repository.
Clone your GitHub repository on to the local machine using the following command.
# git clone <repo-url>
# cd <repo-name>
Step 5: Run ‘tkn pac create repo’ command.
Run ‘tkn pac create repo’ command to configure a webhook and create the repository CR. Provide inputs when prompted.
# tkn pac create repo
? Enter the Git repository URL (default: https://github.com/):
? Please enter the namespace where the pipeline should run (default: pac191-412-pipelines): default
✓ Repository ldaruri-pac191-412 has been created in default namespace
? 👌 A GitHub App is configured for your cluster, Would you like to setup webhook for your repository? Yes
? Please enter the provider name to setup the webhook: github
✓ Setting up GitHub Webhook for Repository https://github.com/👀 I have detected a controller url: https://smee.io/LeB8PyT2gCGnsO
? Do you want me to use it? Yes
? Please enter the secret to configure the webhook for payload validation (default: gFrTCuAwSwgF): gFrTCuAwSwgF
ℹ ️You now need to create a GitHub personal access token, please checkout the docs at https://is.gd/KJ1dDH for the required scopes
? Please enter the GitHub access token: *********************************************************************************************
✓ Webhook has been created on repository ldaruri/pac191-412
🔑 Webhook Secret ldaruri-pac191-412 has been created in the default namespace.
🔑 Repository CR ldaruri-pac191-412 has been updated with webhook secret in the default namespace
ℹ Directory .tekton has been created.
✓ A basic template has been created in /root/pac-412/pac191-412/.tekton/pipelinerun.yaml, feel free to customize it.
ℹ You can test your pipeline manually with: tkn-pac resolve -f .tekton/pipelinerun.yaml | kubectl create -f-
With this invocation, a ’.tekton’ folder emerges, with the ‘pipelinerun.yaml’ file which contains default content to run Pipeline. It creates the GitHub repository and secret in the given namespace on OpenShift cluster. It also configures Webhook controller URL and secret in the GitHub repo for you.
Contents of the folder after running ‘tkn pac create repo’ command are:
# ls -a
. .. .git README.md .tekton
The following screen capture depicts creation of a repository in the OpenShift pipelines.
Default contents of pipelinerun.yaml file within .tektonboot folder are:
--
apiVersion: tekton.dev/v1beta1
kind: PipelineRun
metadata:
name: pac191-412
annotations:
# The event we are targeting as seen from the webhook payload
# this can be an array too, i.e: [pull_request, push]
pipelinesascode.tekton.dev/on-event: "[pull_request, push]"
# The branch or tag we are targeting (ie: main, refs/tags/*)
pipelinesascode.tekton.dev/on-target-branch: "[main]"
# Fetch the git-clone task from hub, we are able to reference later on it
# with taskRef and it will automatically be embedded into our pipeline.
pipelinesascode.tekton.dev/task: "git-clone"
# Use maven task from hub
#
# pipelinesascode.tekton.dev/task-1: "maven"
# You can add more tasks by increasing the suffix number, you can specify them as array to have multiple of them.
# browse the tasks you want to include from hub on https://hub.tekton.dev/
#
# pipelinesascode.tekton.dev/task-2: "[curl, buildah]"
# How many runs we want to keep.
pipelinesascode.tekton.dev/max-keep-runs: "5"
spec:
params:
# The variable with brackets are special to Pipelines as Code
# They will automatically be expanded with the events from Github.
- name: repo_url
value: "{{ repo_url }}"
- name: revision
value: "{{ revision }}"
pipelineSpec:
params:
- name: repo_url
- name: revision
workspaces:
- name: source
- name: basic-auth
tasks:
- name: fetch-repository
taskRef:
name: git-clone
kind: ClusterTask
workspaces:
- name: output
workspace: source
- name: basic-auth
workspace: basic-auth
params:
- name: url
value: $(params.repo_url)
- name: revision
value: $(params.revision)
# Customize this task if you like, or just do a taskRef
# to one of the hub task.
- name: noop-task
runAfter:
- fetch-repository
workspaces:
- name: source
workspace: source
taskSpec:
workspaces:
- name: source
steps:
- name: noop-task
image: registry.access.redhat.com/ubi9/ubi-micro
workingDir: $(workspaces.source.path)
script: |
exit 0
workspaces:
- name: source
volumeClaimTemplate:
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 1Gi
# This workspace will inject secret to help the git-clone task to be able to
# checkout the private repositories
- name: basic-auth
secret:
secretName: "{{ git_auth_secret }}"
The ‘pipelinerun.yaml’ file contains two tasks by default:
- fetch repository which clones self-repository
- noop task which pulls image
Step 6: Commit changes and push the repository from your local machine.
- Commit your repository's changes using the following commands.
#git add .
# git checkout
.tekton/pipelinerun.yaml
Your branch is up to date with 'origin/main'.
# git commit -m "tekton"
[main fb8e5df] tekton
1 file changed, 89 insertions(+)
create mode 100644 .tekton/pipelinerun.yaml
git remote add origin
fatal: remote origin already exists.
- Create a new branch using the following command.
# git branch -b demo
- Push your repository using the following command.
# git push origin demo
Username for 'https://github.com':
Step 7: Initiate a pull request or commit to the main branch of the repository.
After pushing the repository to the demo branch, go to the repository and initiate a pull request from the demo branch to the main branch. This action initiates the running of the file 'pipelinerun.yaml' located in the '.tekton' folder via GitHub checks.
You can see results right in your GitHub repository under Checks, and view Pipelines run on the Red Hat OpenShift cluster.
When you click on any of the tasks, PipelineRun will start. You will then be redirected to the RedHat OpenShift cluster, where the PipelineRun takes place.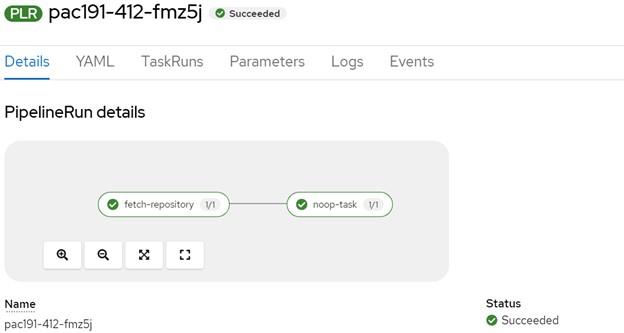
This is how you can easily switch between the GitHub repository and the OpenShift cluster to observe the progress of Pipelines.
Conclusion:
Throughout this blog, we have comprehensively explored the practical implementation of PAC with GitHub repositories and Red Hat OpenShift clusters on the IBM Power platform. For simplification, we utilized a single README.md file within the repository, but you can effortlessly apply the same procedure to any other application source code repository hosted on GitHub. In our upcoming blog posts, we will delve into illustrative instances of implementing PAC with Bitbucket and GitLab. Stay connected for more insightful content!