You may be aware that I am writing a series of blogs related to Security and Compliance on the OpenShift Container Platform (OCP) on IBM Power Systems.
As part of this series, I have written a blog on PCI-DSS and the Compliance Operator to have a secure and compliant cluster. Part of the cluster’s security and compliance depends on the File Integrity Operator – an operator that uses intrusion detection rules to verify the integrity of files and directories on cluster’s nodes.
My team has added support for File Integrity Operator on OpenShift Container Platform on IBM Power, and in this post I’m sharing the background, the setup, verify the setup and the use the Operator in your cluster.
The Background
The file integrity operator deploys a DaemonSet which initializes and runs privileged Advanced Intrusion Detection Environment (AIDE) containers on each node and logs the files and directories which have been modified since the baseline run.
The operator works with FileIntegrity resources, where each of these objects represents a managed deployment of AIDE on one or more nodes.
This post next shows how to setup File Integrity Operator.
To install the File Integrity Operator on your OpenShift Container Platform 4.12 or higher system, execute the following steps:
-
Login with a user id that has cluster-admin user access
-
In the OpenShift Container Platform web console, navigate to Operators → OperatorHub.
-
Search for the File Integrity Operator, then click Install.
-
Keep the default selection of Installation mode and namespace to ensure that the Operator is installed to the openshift-file-integrity namespace.
To confirm that the installation is successful:
-
Navigate to the Operators → Installed Operators page.
-
Check that the Operator is installed in the openshift-file-integrity namespace and its status is Succeeded.
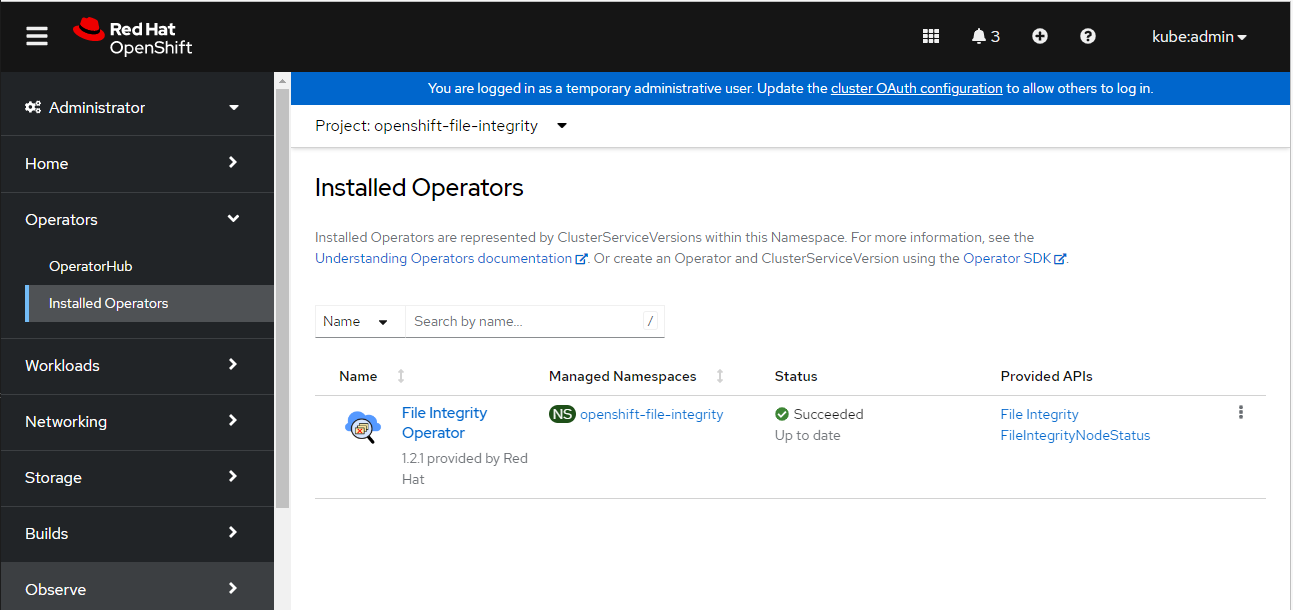
3. You can also verify the installation succeeded by inspecting a csv file.
You should see output similar below
$ oc get csv -n openshift-file-integrity
NAME DISPLAY VERSION REPLACES PHASE
file-integrity-operator.v1.2.1 File Integrity Operator 1.2.1 Succeeded
4. Verify that File Integrity Operator is running using below command
$ oc get deploy -n openshift-file-integrity
NAME READY UP-TO-DATE AVAILABLE AGE
file-integrity-operator 1/1 1 1 31m
Use the File Integrity Operator
-
Create a FileIntegrity Custom Resource using below file-object.yaml file.
apiVersion: fileintegrity.openshift.io/v1alpha1
kind: FileIntegrity
metadata:
name: worker-fileintegrity
namespace: openshift-file-integrity
spec:
nodeSelector:
node-role.kubernetes.io/worker: ""
tolerations:
- key: "myNode"
operator: "Exists"
effect: "NoSchedule"
config:
name: "myconfig"
namespace: "openshift-file-integrity"
key: "config"
gracePeriod: 20
maxBackups: 5
initialDelay: 60
debug: false
status:
phase: Active
spec.nodeSelector - Defines the selector for scheduling node scans.
spec.tolerations – Specify tolerations to schedule on nodes with custom taints. When not specified, a default toleration allowing running on main and infra nodes is applied.
spec.config.name - Define a ConfigMap containing an AIDE configuration to use.
-
Create File Integrity object.
$ oc apply -f file-object.yaml
fileintegrity.fileintegrity.openshift.io/worker-fileintegrity created
-
Confirm the FileIntegrity object was created successfully.
$ oc get fileintegrities -n openshift-file-integrity
NAME AGE
worker-fileintegrity 7s
-
You can also check FileIntegrity Custom Resource status.
$ oc get fileintegrities/worker-fileintegrity -o jsonpath="{ .status.phase }" -n openshift-file-integrity -w
PendingInitializingActive
$ oc get fileintegrities/worker-fileintegrity -o jsonpath="{ .status.phase }" -n openshift-file-integrity
Active
-
Check FileIntegrityNodeStatuses
The scan results of the FileIntegrity CR are reported in another object called FileIntegrityNodeStatuses. The fileintegritynodestatus object reports the latest status of an AIDE run and exposes the status as Failed, Succeeded, or Errored in a status field.
$ oc get fileintegritynodestatuses -n openshift-file-integrity
NAME NODE STATUS
worker-fileintegrity-osa21-worker-0.ocp-power.xyz osa21-worker-0.ocp-power.xyz Succeeded
worker-fileintegrity-osa21-worker-1.ocp-power.xyz osa21-worker-1.ocp-power.xyz Succeeded
$ oc get fileintegritynodestatuses.fileintegrity.openshift.io -ojsonpath='{.items[*].results}' -n openshift-file-integrity | jq
[
{
"condition": "Succeeded",
"lastProbeTime": "2023-05-23T09:22:20Z"
}
]
[
{
"condition": "Succeeded",
"lastProbeTime": "2023-05-23T09:22:18Z"
}
]
-
Check the events of FileIntegrity CR
Transitions in the status of the FileIntegrity and FileIntegrityNodeStatus objects are logged by events. The creation time of the event reflects the latest transition, such as Initializing to Active
$ oc get events --field-selector reason=FileIntegrityStatus -n openshift-file-integrity
LAST SEEN TYPE REASON OBJECT MESSAGE
16m Normal FileIntegrityStatus fileintegrity/worker-fileintegrity Pending
15m Normal FileIntegrityStatus fileintegrity/worker-fileintegrity Initializing
14m Normal FileIntegrityStatus fileintegrity/worker-fileintegrity Active
This post you’ve seen how to install File Integrity Operator, create File Integrity object and make use the of file integrity operator for file integrity checks in OpenShift cluster.
Thanks for reading! I hope you found this helpful :)
#Containers,Kubernetes,andOpenShift