Introduction
Data masking helps mask or obscure sensitive data for occasions when the real data is not required. For example, enterprises want to prevent sensitive data to be displayed in transactional logs in any environment.
This article demonstrates the steps required to mask sensitive data contained in a request body. Data Masking can be applied to both REST and SOAP APIs.
Prerequisites
- An active subscription of webMethodsio API Gateway Cloud tenant
- Basic Knowledge of Query Expressions like XPath, JSONPath, and Regex to target fields within the request body
Procedure
- Login to webMethods.io API Gateway tenant and select an API.

In this example a 'MaskDataAPI', a simple REST API, is used to demonstrate the application of Data Masking on a request body containing JSON data.
- Go to Policies and select Edit. From the Policy catalog, select Data Masking under Request Processing to add it to the API.
- On the right, there is Policy properties panel where there is an option to configure criteria for Data Masking.
Three types of Query Expressions are supported - XPath, JSONPath, and Regex.
There are options to apply Data Masking to Transaction Logs and Payload.
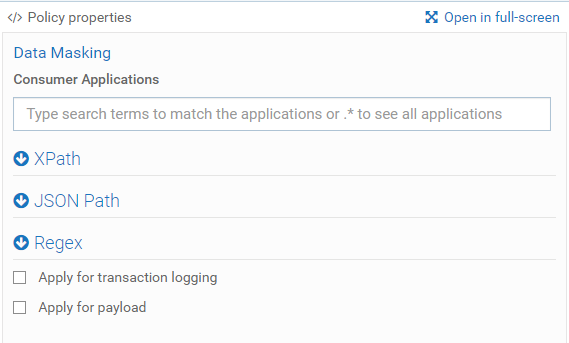
Query expression can be selected based on type of request body. In the below example, JSONPath is selected for the application/JSON payload.
- The request body constitutes of dummy credit card data like shown below.
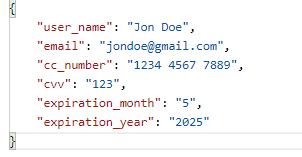
A Masking Criteria can be applied to each field within the request body.
Below are the masking types available.
Masking Type:
a. Mask: Will replace the value of the targeted field with the mask value provided. Default value is (*******).
b. Filter: Removes the field completely from the payload. If this is selected, mask value will be hidden as it is not necessary.
In the below example two fields are masked (cc_number and cvv) and one field (email) is filtred. Also, only transaction logging option is selected.
- To test the API, go back to the Technical Information section and copy the Gateway endpoint.
Additionally, copy the resource path of the resource to be targeted like shown below.
- Update the POST request to the URL (gateway-endpoint + resource-path) as shown below in Postman.
- After successful execution, verify the Transaction Logs under Analytics tab to see if masking has been correctly applied.
- Verify that masking has been applied only within Transaction Logs (as was specified in Step 4) by sending a POST request to a second resource path as shown below.
This endpoint executes a Flow Service which simply echoes back the request body. Using Postman, send a POST request to selected resource path which simply echoes back the request body without any masking.
Here, the request body can be seen to be unaltered by data masking.
Note
- You can choose to apply Data Masking to the request body throughout the application level. This can be done by checking the 'Apply for payload' option in Step 4.
- The /PaymentAPI endpoint was created for demonstration purposes only and will not be made available in the exported API attachment below.
Attachments
#API-Gateway#wiki#webMethods