Database Activity Monitoring with Guardium Data Protection is traditionally leveraged with a lightweight software agent installed on the database server at the OS layer. The agent, called S-TAP, is the responsible for collecting traffic that is the basis of Guardium reports, alerts, dashboards.
But what happens for those systems where we can't or don't want to install the S-TAP? Most typical examples are containerized databases or DBaaS where we don't have the possibility to manage the operating system.
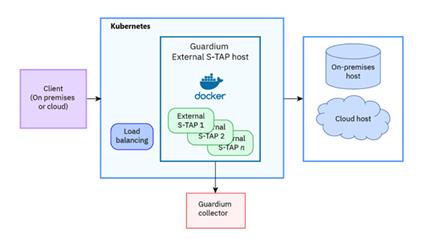
The answer is External S-TAP – a Guardium component that intercepts traffic for cloud and on-premises databases without the need of installing the agent on the database server. The External S-TAP acts as a proxy that forwards the traffic to the database server but also sends a copy of this traffic to a Guardium collector for traditional analysis, parsing and security policy application.
External S-TAP software is based on the S-TAP code, but it is packaged in a Docker image. Due to the nature of the component, two or more containers are required in the same External S-TAP deployment in order to assure the availability of the database connection. This is the reason for the presence of a load balancer as well, that is going to balance the traffic to the containers. Two deployment choices exist now:
- With Kubernetes (Figure 1) – that will take care of issues like load balancing and Docker containers orchestration. Another big advantage of using Kubernetes is the possibility to deploy the External S-TAP directly from the Guardium user interface.
- Without Kubernetes (Figure 2) – in this case the deployment is managed with scripts for both load balancer and External S-TAP itself.
------------------------------
Ander Schiavella
------------------------------