Prerequisit : have the
Utility Functions integration installed and configured
Link to App ExchangePurpose : Enhance the standard shell access using a multi-select choice fo shell action ot the analyst
Changes :
- New Rule
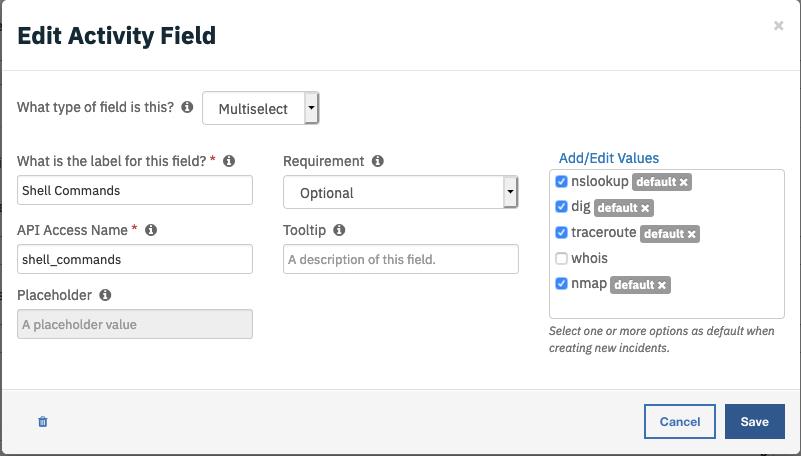
Shell Commands actually limited to atifact type IP and DNS. It use a Shell Command activity fields (below) that allow the analyst to select the action they want to run at once.
- New Workflow
CVE Lookup as duplicate of the Example: CVE Search with changes in post process scripts
Rule:
Workflow:
Actually, the following commands are available :
- traceroute
- nslookup
- dig
- whois
- nmap
It needs the app.config to be adapted like:
# local shell_command default commands (unix)nslookup=nslookup "{{shell_param1}}"dig=dig "{{shell_param1}}"traceroute=traceroute -m 15 "{{shell_param1}}"whois=whois "{{shell_param1}}"nmap=nmap "{{shell_param1}}"and the requested packages to be installed on the integration server that will launch the shell.
Here is my personal list, but check and verify it before using it!
# Install for Shell action traceroute, whois, bind, nmap, nslookupwget http://mirror.centos.org/centos/7/os/x86_64/Packages/traceroute-2.0.22-2.el7.x86_64.rpmsudo rpm -Uvh traceroute-2.0.22-2.el7.x86_64.rpmwget http://mirror.centos.org/centos/7/os/x86_64/Packages/whois-5.1.1-2.el7.x86_64.rpmsudo rpm -Uvh whois-5.1.1-2.el7.x86_64.rpmsudo yum install bind-utilswget http://mirror.centos.org/centos/7/os/x86_64/Packages/libpcap-1.5.3-11.el7.x86_64.rpmsudo rpm -Uvh libpcap-1.5.3-11.el7.x86_64.rpmhttp://mirror.ghettoforge.org/distributions/gf/el/7/plus/x86_64/nmap-ncat-7.10-1.gf.el7.x86_64.rpmhttp://mirror.ghettoforge.org/distributions/gf/el/7/plus/x86_64//nmap-7.10-1.gf.el7.x86_64.rpmsudo rpm -Uvh nmap-ncat-7.10-1.gf.el7.x86_64.rpmsudo rpm -Uvh nmap-7.10-1.gf.el7.x86_64.rpmNote that I recommend a dedicated integration server in a DMZ for integrations facing internet like Shell, VirusTotal, Pipl etc...Results are visible in notes, and result status in artifact description:
Attached is the res file to import this configuration.
Feel free to use, change, adapt this code to your usage.
Building the res file:resilient-circuits extract --workflow "shell" --rule "Shell Commands" -o config_SHELL.res --zip
------------------------------
BENOIT ROSTAGNI
------------------------------