I already checked on how to request additional parameters in the "id_token".
According to the specification,
https://openid.net/specs/openid-connect-core-1_0.html#ClaimsParameter, you can make these requests in the Authorize endpoint or Userinfo endpoint.
It did not work for me, when using Authorize requests, and I haven't got a clue why.
According to the specification support of "Claims" option in Authorize endpoint is OPTIONAL. Does ISAM support this?
If it does, that I have something wrong in my configuration or request format.
I am using claims=["email","environment"] in the URL. When send it I make sure it is URLENCODED. It does not work!
I am going to try later to always include something in the JWT, and do another test for "scope" based attributes.
------------------------------
Joao Goncalves
Pyxis, Lda.
Sintra
+351 91 721 4994
------------------------------
Original Message:
Sent: Thu October 08, 2020 06:14 AM
From: Jon Harry
Subject: Adding attributes to JWT in OpenID
Not completely sure but I don't think it's normal for OIDC to provide attributes in HTTP headers. Usually attributes are sent in the id_token (a JWT) or requested after initial SSO from the UserInfo endpoint.
Jon.
------------------------------
Jon Harry
Consulting IT Security Specialist
IBM
Original Message:
Sent: Thu October 08, 2020 05:57 AM
From: Joao Goncalves
Subject: Adding attributes to JWT in OpenID
Thanks for the information.
I will try all of them, and see if I can make it work.
How do I tell the system where to put the attributes (JWT vs HTTP Headers)?
------------------------------
Joao Goncalves
Pyxis, Lda.
Sintra
+351 91 721 4994
Original Message:
Sent: Thu October 08, 2020 05:48 AM
From: Jon Harry
Subject: Adding attributes to JWT in OpenID
Hi Joao,
Adding attribute sources/attribute mapping to an OIDC definition doesn't tell the system to always send those attributes. It simply makes them available (using the "atttribute name") to be requested by the client. The client requests specific attributes using a claim request (as mentioned in other thread).
If you want the OIDC Provider to always provide an attribute you will need to edit the pre-token mapping rule to add it to the context. There's information on the attribute type to set in the presentation I pointed to in the other thread. If you wanted to you could also add logic to include the attribute based on received scopes.
Jon.
------------------------------
Jon Harry
Consulting IT Security Specialist
IBM
Original Message:
Sent: Wed October 07, 2020 03:51 PM
From: Joao Goncalves
Subject: Adding attributes to JWT in OpenID
Well, my saga is not finished yet.
After configuring successfully the configuration of OpenID, I need to include fields in JWT and/or HTTP Headers.
What I did so far, was to create an Attribute Source, chose several, including a "fixed" attribute named "environment" with the value "TEST".
Here is the configuration:
After this, I went to OpenID Provider configuration and added some attributes:
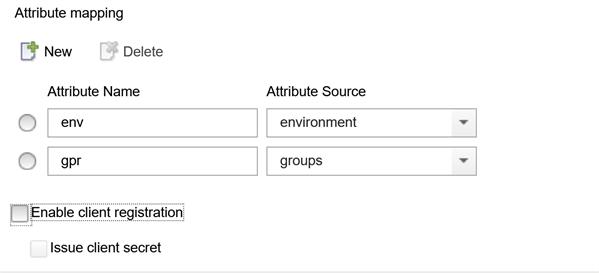
Hoping that now, these properties would show up in the JWT, which did not.
Now I have a some questions:
- What did I do wrong? why are the attributes not showing anywhere?
- How do I specify whether the attributes should show in JWT or in the HTTP headers?
- After adding in the OpenID Provider these attributes, what happened behind the scenes? I went to the Pre and Post scripts, and apparently nothing was changed there!
------------------------------
Joao Goncalves
Pyxis, Lda.
Sintra
+351 91 721 4994
------------------------------