IBM Cloud Pak for Data supports Security Assertion Markup Language (SAML) for Single Sign On (SSO) integration, there are several commercial Single Sign on Identity providers, in this article we will summarize the steps for integrating Cloud Pak for Data with Red Hat Single Sign On Server.
Software Pre-requisites
The following product versions were used in this article
- Red Hat Single Sign on Server 7.4
- Red Hat Identity Management 4.9
- IBM Cloud Pak for data 4.x
Configure Red Hat Single Sign On Server
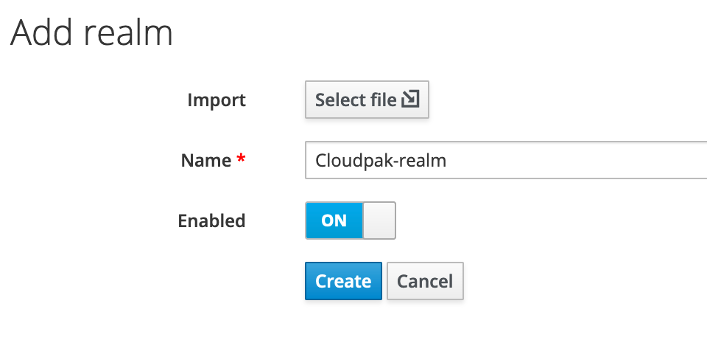
- Login to Red Hat SSO Server as Administrator user and create a new realm using add realm menu
- When requested provide a name for the realm,
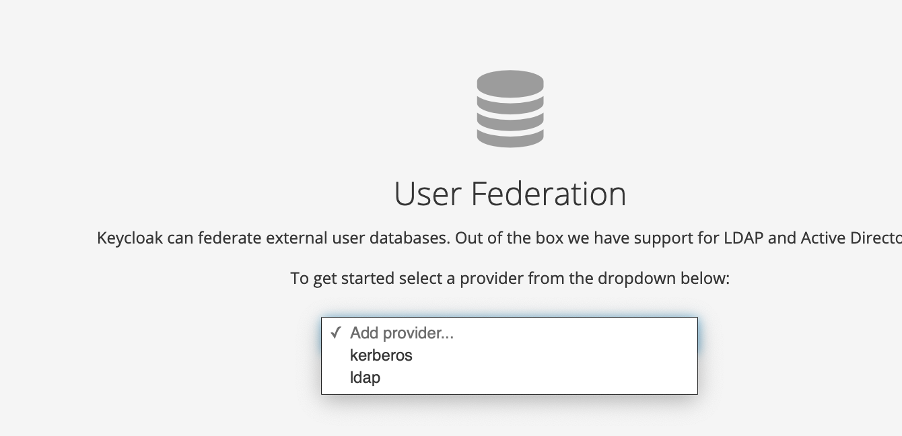
- Configure the user federation for the cloudpak-realm , for this article we will be using Red Hat Identity Management as our LDAP/identity provider, select User Federation menu and select LDAP as provider from the drop down menu
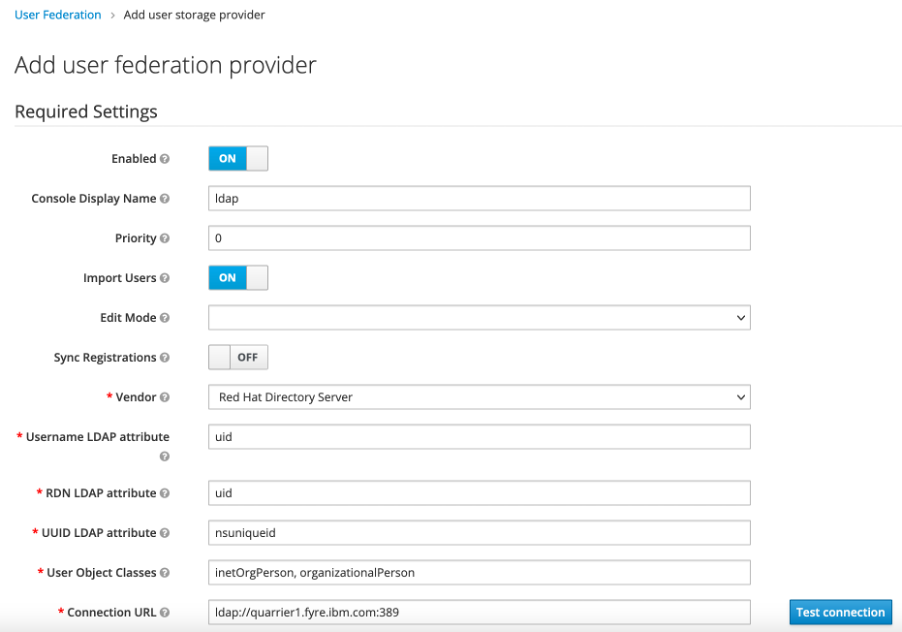
- Set the vendor field to Red Hat Directory server, this automatically sets the other LDAP attributes fields to facilitate integration with the specified vendor. Update the connection URL and set the remaining mandatory settings such as Users DN, Bind DN, Bind Credential. Test the connection to see whether the credentials are correct, if the test succeeds, click save.
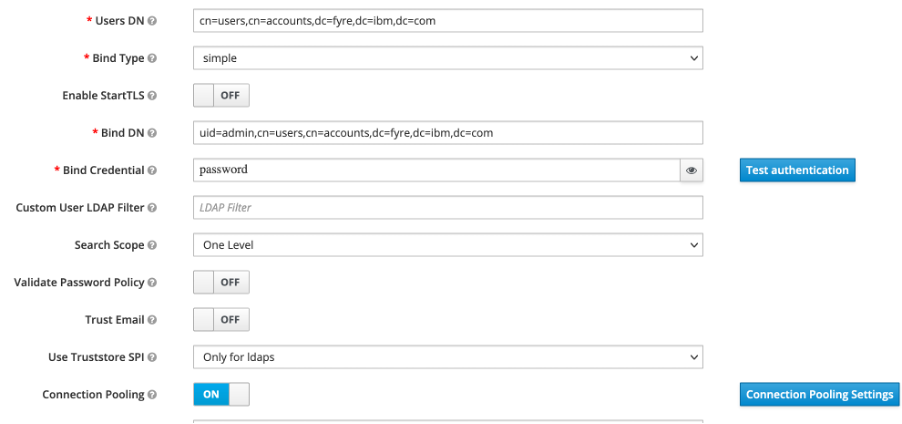
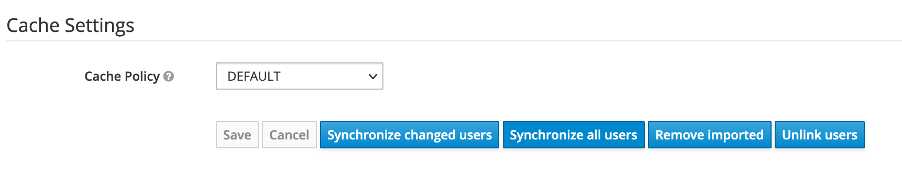
- After saving the LDAP settings, additional options are unlocked, which can be used to synchronize the LDAP users with Red Hat SSO Server. Select Synchronize all users for the first time. A popup should appear highlighting number of user records successfully synchronized.
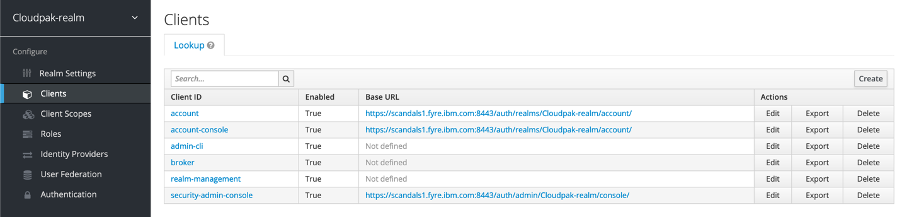
- Now register the Cloud Pak web client within the Cloud Pak realm, select Clients and click Create
- When requested provide a name for the client, this client name will later be used while configuring the Cloud Pak web client. Set the Client Protocol field to SAML.
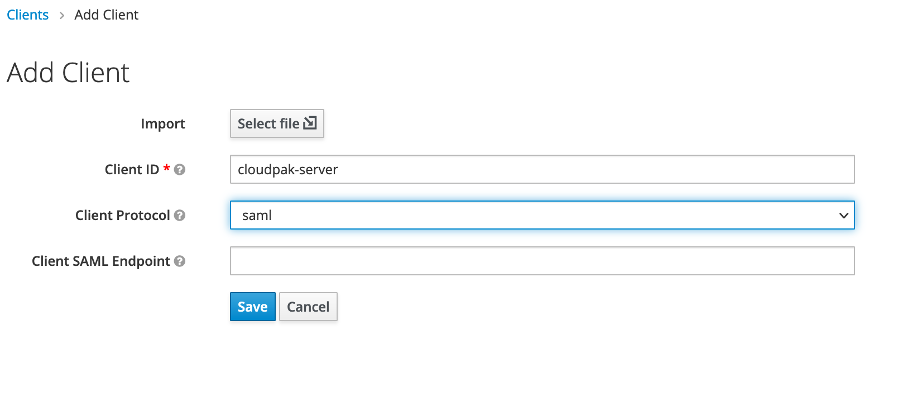
- Configure the cloudpak-server client settings, specify the Cloud Pak callback URI for "Valid redirect URIs" property , for example, https://cluster/auth/login/sso/callback, the rest of the properties can be left to their default values.
- Now we’ll export the SAML keys which will be later used to configure Cloud Pak for Data SAML settings. These keys will allow Red Hat SSO server and Cloud Pak client to identify each other.

- Select Export option, then set the archive format as PKCS12, set the key and store password and click Download.

- Extract the certificate and keys from the keystore ,
openssl pkcs12 -in keystore.p12 -nokeys -out cert.pem
openssl pkcs12 -in keystore.p12 -nodes -nocerts -out key.pem
Retain the cert.pem and key.pem files, we will be using them to configure cloud pak web client later.
- Finally we'll create a mapper object for mapping the LDAP attributes to their respective SAML attributes, select Mappers tab and click create

- Specify the mapper details so that the username will be included within the SAML response body. Set the mapper type as User property and set the property name and SAML attribute name as “username”. Save the mapper.

- Now Red Hat SSO Server is ready to be integrated with Cloud Pak Web Client
Integrating Cloud Pak for Data with Red Hat Identity Management for Access Control
- Login to Cloud Pak for Data UI as administrator, Select Access Control Menu and Click on LDAP Configuration . Specify the hostname and port for directory server, and user search field attribute as applicable for Redhat Directory Server.
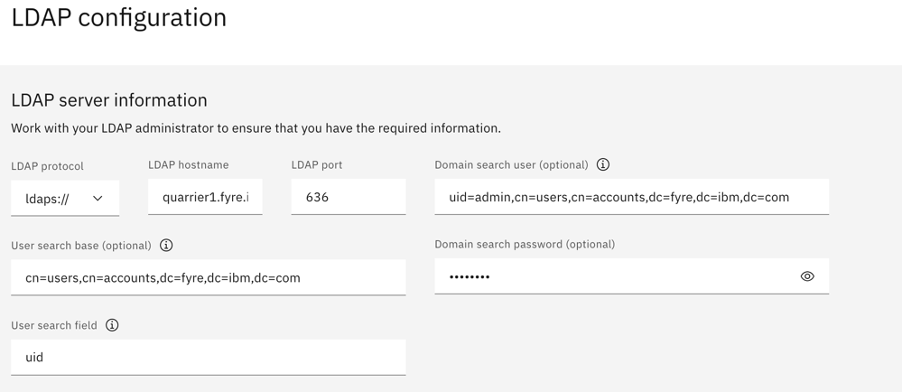

- Test the connection by specifying a username and password from the directory server. If the test connection succeeds save and exit.

- Within the access control page, import a user from the IdM server, this user will later be used for logging in using SSO.

- Assign the required roles and proceed to complete the user import

Integrate Cloud Pak web client with Red Hat SSO using SAML
- Following table lists the values we will be assigning to the SAML configuration attributes for integrating with Redhat SSO
|
Attribute Name
|
Value
|
|
entryPoint
|
https://redhatsso-server.ibm.com:8443/auth/realms/Cloudpak-realm/protocol/saml
|
|
fieldToAuthenticate
|
username
|
|
spCert
|
Import the private key from the file key.pem, refer to configure redhat sso section for details.Exclude the tags begin private key and end private key while importing.
|
|
idpCert
|
Import the IDP certificate from the file cert.pem.
Copy the Cloudpak-realm certificate from the certificate chain excluding the Begin certificate and End certificate tags
|
|
issuer
|
Specify the name of the client used for registering with Redhat SSO, for this example it’ll be cloudpak-server
|
|
identifierFormat
|
Not used
|
|
callbackUrl
|
The cloud pak call back URL once the authentication is complete,
https://<cloud pak url>/auth/login/sso/callback
|
Once completed json file will be in the following format, the certificate and private key values have been truncated
{
"entryPoint": "https:// redhatsso-server.ibm.com:8443/auth/realms/Cloudpak-realm/protocol/saml",
"fieldToAuthenticate": "username",
"spCert": " MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQCSr9EYtvAt8MwQ27f1H+F2pcLvoxmKazV4HJobS2d…",
"idpCert": "MIICqzCCAZMCBgF7lUDC9zANBgkqhkiG9w0BAQsFADAZMRcwFQYDVQQDDA5DbG91ZHBhay1yZWFsbTAeFw0yM…",
"issuer": "cloudpak-server",
"identifierFormat": "",
"callbackUrl": "https://cpd-zen.apps.teased.cp.fyre.ibm.com/auth/login/sso/callback"
}
- Login to Openshift and apply SAML configuration within usermanagement pod using the following comman
oc exec -it -n namespace $(oc get pod -n namespace -l component=usermgmt | tail -1 | cut -f1) -- bash -c "vi /user-home/_global_/config/saml/samlConfig.json"
- Restart the usermanagement pods so that the config changes can be applied
oc delete pods -l component=usermgmt
Now that the SSO integration is complete, whenever user tries to login to Cloud Pak for Data web UI, users will be redirected to Redhat SSO login page for authentication as shown following

Once successfully authenticated, users will be logged in to the Cloud Pak UI.
#CloudPakforDataGroup