Introduction :-This article describes the procedure followed for re-enabling Single Sign-On (SSO) capability between IBM Security Access Manager and IBM Cognos analytics post Cognos BI upgrade.
Scope and background :-This cross brand integration is not officially supported as of now, hence IBM Cognos product support may not be able to provide documented guidelines for support. Remote cognos technical support side can try to assist you and provide some inputs although this falls outside of scope for remote cognos technical support as ISAM product is not listed as officially supported for CA 11.1.7.
Assuming, SSO between Cognos BI (v10) and ISAM is already implemented in a project. The scope of this blogpost should only be considered as reference to confirm that SSO capability will carry forward post Cognos upgrade and understand steps that helped me to achieve SSO.
As per my experience in Cognos BI upgrade project, the SSO capability stopped working after Cognos (AIX based) was upgraded from version 10.2.2 to 11.1.7.
Technical details of environment are as follows:-
- Product version : Cognos analytics 11.1.7 (Distributed)
- Operating system : AIX 7
- CA Authentication source : Microsoft Active Directory
- CA gateway : IBM HTTP Server 9.0 (non-SSL)
- IBM Websphere Portal (WPS 8.5)
- IBM Security access manager (ISAM) with federated directory support for MS-Active directory and Webseal reverse proxy
This blog does not cover the configuration of the entire environment / above said product portfolio. In particular, mentioned product installations and configurations must already be complete.
Scenario :-
Post Cognos product upgrade and webseal junction reconfiguration, it was observed that SSO does not establish between ISAM and Cognos.
CA legacy login page is prompted by Cognos and user has to login again.
Post login to cognos application directly, browser maintains the server specific cookie to build the user session.
Below error was observed using F12 tool while debugging CA link SSO error.
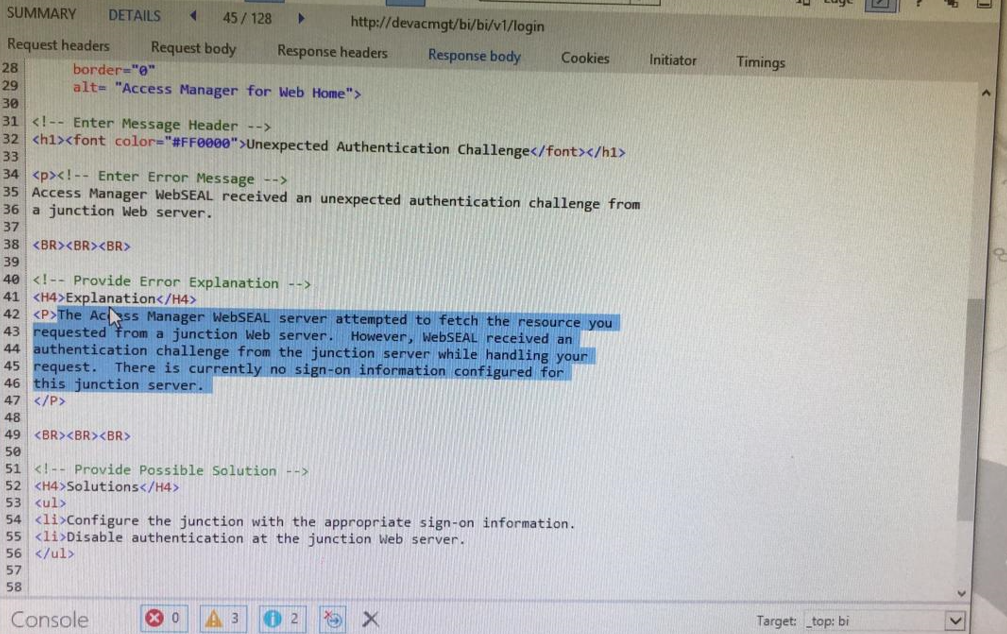
Following procedure helped in making SSO work again.
Step 1 :- Create transparent webseal junction
The following example use a Transparent Path junction to eliminate the requirement of path filtering. The Transparent Path junction name must exactly match the Context Root for Cognos. For example, /ibmcognos.
Using the pdadmin command-line utility, create a transparent path junction to the Cognos context root of the gateway. For example:
1. Determine the WebSEAL server name.
For example:
pdadmin sec_master> server list <instance-name>-webseald-<websealhost-name>
2. Create a Transparent Path to the Cognos Gateway URL with "in head" option.
The "in head" option for the cookie handling depends on whether domain cookies get prefixed with the junction or not.
pdadmin sec_master> server task <instance-name>-webseald-<websealhostname> create -t tcp -r -b filter -c all -h <cognos-gateway-fqdn> -p <cognos-gatewayport> -c iv-user -x /ibmcognos -j -J inhead -n
Step 2 :- IBM Cognos analytics configuration
- Launch the Cognos Configuration tool.
- Navigate to the Security group and expand Authentication component
- Under Authentication - Ensure Allow anonymous access is False
- Select New resource → Namespace
- On the New Resource - Namespace page, provide a meaningful value for Name, for
example: Security Access Manager.
- Select the Type: LDAP – Default values for Active directory.
- On the Resource Properties page, define the following properties:
The authenticated user identity for IBM Security Access Manager is passed in the iv-user request HTTP header to Cognos which performs a search of the user ID in the configured LDAP. If the user ID is found in the LDAP configured for the namespace, any additional user attributes (such as name) are read and returned to Cognos.
Lastly, its recommended to ensure Forms authentication is used so that single sign-out can be achieved using the Cognos <redirect-url /> tag. The following describes the steps to disable the Basic Authentication and enable Forms Authentication
1. Open the Web Gateway Appliance Web console.
2. Select Secure Web Settings → Reverse Proxy.
3. Select the preferred instance.
4. Select Edit.
5. Select the Authentication tab.
6. Under Basic Authentication → Transport, select None.
7. Under Forms → Forms Authentication, select Both.
8. Click Save.
If Forms Authentication is not used the browser window must be closed to terminate the IBM Security Access Manager session.
The solution is tried and tested on both Mozilla firefox and Google chrome web browsers.
#CognosAnalyticswithWatson