As part of the overall IBM FedRAMP project, IBM MaaS360's boundary will be expanded to include an AWS GovCloud deployment of MaaS360 over the MCSP stack. FedRAMP customers on M1 and M3 MaaS360 instances will be migrated to M7 (the new AWS GovCloud instance). M1 and M3, post-FedRAMP tenant migrations to M7 will become commercial-only instances and will drop off the FedRAMP boundary.
Acess To MCSP Gov Cloud for MCSP Prod M7 Environment:
Step 1: First the user needs to raise a git issue for getting their user account created on the IBM Gov Cloud using the Link
Click on Request New User Account as shown below:

The user needs to fill in the template below on GIT:
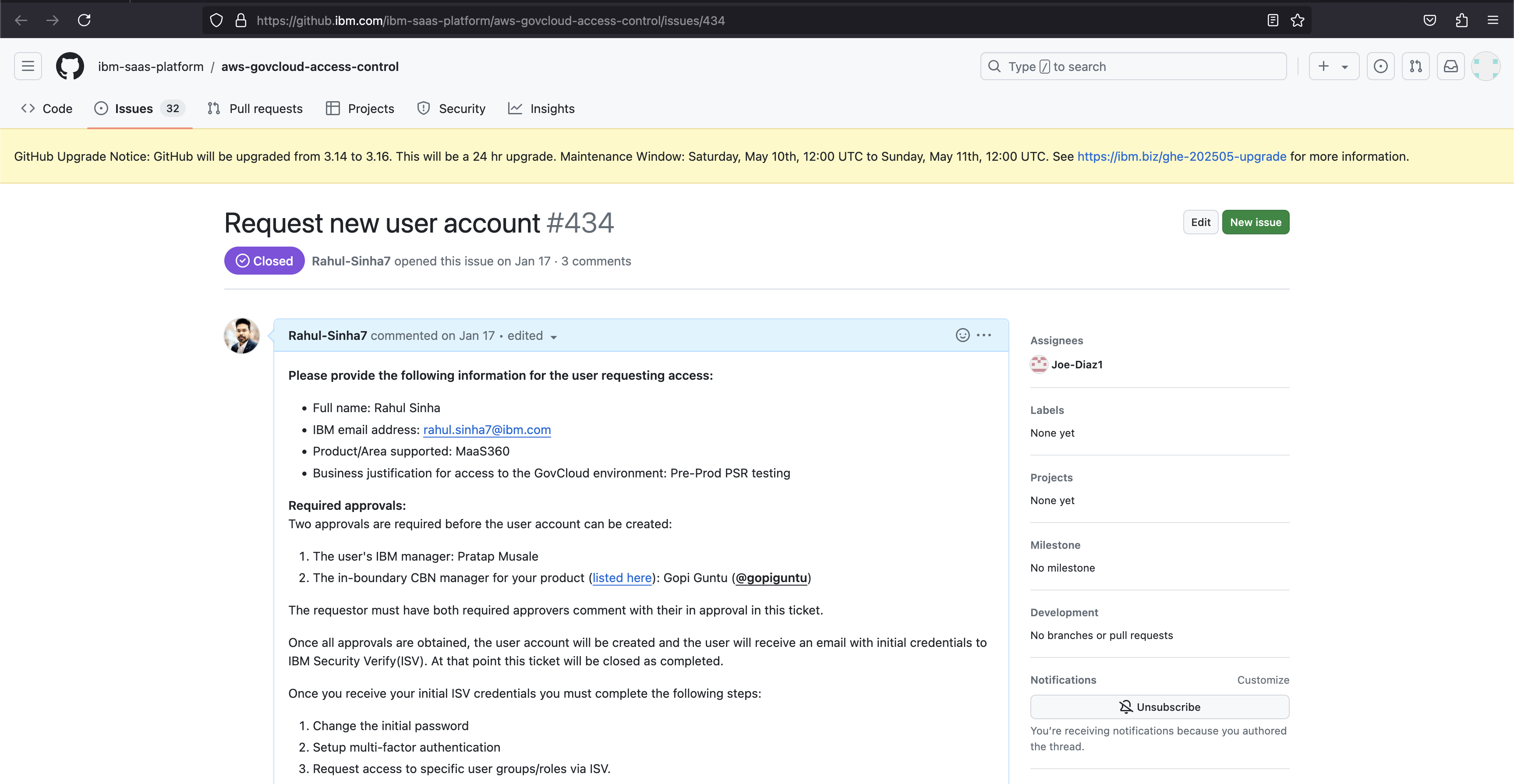
- Once submitted, inform your reporting manager to approve this request with the justification.
- Once your manager approves, the second line approval will go to Gopi Guntu.
- Upon approval by Gopi, the request will now go to the core MCSP team in the US and will be served mostly by Joe Diaz.
- This entire process will day at least 1 day and once the user account is created on IBM gov cloud by Joe, you will receive an email notification with login details.
- You need to login using the IBM email address and the temporary password.

- The user must log in to https://sre-ibm-fedramp-idp.verify.ibmforusgov.com/usc for MCSP Prod M7 and set up the two-factor authentication.

- Once two-factor authentication is set up, the user will be able to log in to the IBM Fedramp landing page.
- Initially, when the user logs in for the first time, it will not have any application listed.
- The user will have to request access to "IBM GovCloud Application Manager" and wait for approval.
- Once the access is given, the user will then be able to request for Roles for MCSP_Prod_Fed_Developer_M360

- The request approval will again go to Gopi Guntu and once approved, Viswanath Kotamraju will be able to grant role-level access to the user.
- Once the user has the roles added, then he/she can navigate to App Center and launch the application by clicking on IBM GovCloud Application Manager

At this point, you might be requested to log in again and once the page loads, the user will need to scroll down and click on AWS GovCloud Identity Manager.
- Once the AWS access portal opens, you need to expand the mcsp-MaaS360-prod and open the MCSP_P_F_SerDev.
- It should launch the AWS console and then you can navigate to Cloudwatch making sure that you have selected the us-east-1 region.

Fetching the Application logs via the Openshift Console:
- The user can access the Openshift Console using the URL: M7 Openshift Console
- Then the user can navigate to Workload>Pods>search for relevant pods and navigate to Logs to see the real-time logs for the application pods.
- Note: For both of the above ways to check the application logs, the user needs to ensure that he/she is connected to the AWS Prod VPN profile
- VPN Profile can be found on the shared link: AWS ProdVPN
- The user will also need to download the AWS VPN client using the link: AWS VPN Client
- Once downloaded, the user needs to navigate to Manage Profiles and import the downloaded Prod VPN profile.
- Please follow the Link if you want similar access for Dev or Pre-prod environments