“Azure Virtual Desktop” is a desktop and application virtualization service it runs on the cloud.
In this article, we discuss the steps to be followed to publish the “IBM Personal Communications” application in “Azure Virtual Desktop.”
In this article, we have demonstrated the steps using the “Azure Virtual Desktop” (classic), which does not support Azure Resource Manager Azure Virtual Desktop objects. Please refer to the link below for details.
https://learn.microsoft.com/en-us/azure/virtual-desktop/virtual-desktop-fall-2019/tenant-setup-azure-active-directory
Please refer to the link below if you’re trying to manage Azure Resource Manager Azure Virtual Desktop objects. You can create a setup using the steps mentioned in the article below. This method will create host pools and manage Remote application groups using the Azure UI instead of PowerShell.
https://learn.microsoft.com/en-us/azure/virtual-desktop/create-host-pools-azure-marketplace?tabs=azure-portal
A brief outline of the steps for publishing the “IBM Personal Communications” in “Azure Virtual Desktop.”
- Create Azure Active directory: Microsoft Azure Active Directory (AD) is a cloud-based service to handle identity and access management. If you do not have access to the Azure Active Directory of the subscription directory (No Global Administrator Role), you can create a new Azure Active Directory.
- Create a tenant in Azure Virtual Desktop: Creating a tenant in “Azure Virtual Desktop” is the first step towards building application virtualization. A tenant is a group of one or more host pools. Users can build host pools, create application groups, and assign users with a tenant.
- Domain Controller: A Domain Controller (DC) is a Windows network server allowing users to access domain resources. Its main purpose is to authenticate users in a network. You can use the Active Directory domain using Active Directory Domain Services (AD DS) instead of the domain controller.
- Create a Hostpool: Host pools are a collection of one or more identical virtual machines within “Azure Virtual Desktop” tenant environments. Each host pool can contain an application group that users can interact with as they would on a physical desktop.
- Connect to the virtual machines of the Hostpool and Install IBM Personal Communications.
- Manage application groups for Azure Virtual Desktop: We can create one or more RemoteApp application groups for the host pool. In this step, we will create the Remote Application Group using PowerShell and publish the “IBM Personal Communications.”
- Access published Applications: Users can sign into “Azure Virtual Desktop” with the supported Remote Desktop clients and the web client.
Now we will see how we can publish the “IBM Personal Communications” in “Azure Virtual Desktop.”
- Create Azure Active Directory:
Microsoft Azure Active Directory (AD) is a cloud-based service to handle identity and access management. For example, an Azure subscription is linked to the “user1.name@myorg.com”.
If you do not have access to the Azure Active Directory (No Global Administrator Role), you can create a new Azure Active Directory using the steps below. Else use the “myorg.com” directory.
- Log in to: https://portal.azure.com/#homewith the subscription account.
- Click on Create a Resource, as shown below.

- Search for the azure active directory and select it as shown below.

- Click on create as shown in the below image.

- Enter the suitable organization name (Example: Contoso) and domain name and click create. Now the domain will be “onmicrosoft.com”
- Click on the top right corner in azure to check the created tenant.

As we have created a new azure active directory, we need to create users and assign roles to them. Switch to the newly created azure directory (Contoso) and navigate to the Azure Active Directory.
Create a new user and assign a “Global Administrator” role to the user.
Example: test1@contoso.onmicrosoft.com-- > “Global Administrator” role
test2@contoso.onmicrosoft.com
2.
Create a tenant in Azure Virtual Desktop:
Creating a Tenant in “Azure Virtual Desktop” is the first step towards building a desktop virtualization solution.
- Grant Azure Active Directory permissions to the Windows Virtual Desktop service and assign tenant creator role:
Granting permissions to the “Azure Virtual Desktop” service lets it query Azure Active Directory for administrative and end-user tasks. If you have created a new Azure Active Directory using step 1, ensure that you are in the newly created Azure Active Directory (Directory Name: Contoso).
If not, use the Azure Directory linked to the subscription, “myorg.com”: example, “user1.name@myorg.com”.
Please refer below link for the steps on granting permission to azure AD
https://learn.microsoft.com/en-us/azure/virtual-desktop/virtual-desktop-fall-2019/tenant-setup-azure-active-directory
Note: For the newly created Azure AD, Sign into the “Azure Virtual Desktop” consent page with a global administrator account test1 user (“test1@contoso.onmicrosoft.com”). For simplicity, assign the “TenantCreator” role to the test1 user.
For the Azure AD linked to the subscription, use global administrator “user1.name@myorg.com” to sign into the “Azure Virtual Desktop” consent page and assign the “tenant creator” role to the user1.
- Create an Azure virtual desktop tenant:
First, download and import the “Azure Virtual Desktop” module to use in your PowerShell session.
Sign into “Azure Virtual Desktop” by using the TenantCreator user account (“test1@contoso.onmicrosoft.com” OR “user1.name@myorg.com” based on the directory ) with the below cmdlet:
Add-RdsAccount -DeploymentUrl https://rdbroker.wvd.microsoft.com
- Azure AD tenant id: If you have created a new Azure AD using step 1, note the Azure AD tenant of the “Contoso” directory ( onmicrosoft.com). Else, note the Azure AD tenant of the directory “myorg.com.” Please refer below for the Azure AD tenant id.

- Subscription Id: Ensure that you are in the subscription-linked Azure AD and navigate to the “subscriptions,” and note down the subscription Id. Please refer below screenshot for reference.
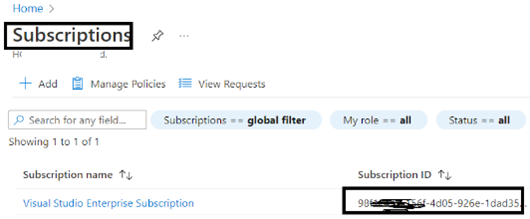
After that, create a new “Azure Virtual Desktop” tenant associated with the Azure Active Directory tenant using the cmdlet below:
New-RdsTenant - Name <TenantName> -AadTenantId <DirectoryID> -AzureSubscriptionId <SubscriptionID>
Replace the bracketed values with values relevant to your organization and tenant in the above command. The name you choose for your new “Azure Virtual Desktop” tenant should be globally unique.
For example, the WVD tenant’s name is WVDtenant1.
Please refer below link for more details regarding the steps mentioned above.
https://learn.microsoft.com/en-us/azure/virtual-desktop/virtual-desktop-fall-2019/tenant-setup-azure-active-directory
3. Domain Controller:
A Domain Controller (DC) is a Windows network server allowing users to access domain resources. Its main purpose is to authenticate users in a network.
Azure AD is always used to authenticate users for “Azure Virtual Desktop.” Session hosts can be joined to the same Azure AD tenant or an Active Directory domain using Active Directory Domain Services (AD DS) or Azure Active Directory Domain Services (Azure AD DS).
You can use Active Directory Domain Services instead of the domain controller.
Ensure that you are in the subscription-linked Azure Directory. Create a virtual machine and install the AD DS role for using this Virtual Machine as a domain controller. All the virtual machines of the host pool will be joined to this domain controller.
Users in the domain controller and Azure Active Directory must be the same. We can achieve this by installing the “Azure AD Connect” in the domain controller.
Install “Azure AD Connect” in the Domain controller to sync the on-premises users (Users in the Domain Controller ) to the Azure Active Directory.
Please check the below link for more information on Azure AD Connect.
https://learn.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-install-express
By default, VNET uses the Azure-provided DNS server (Default – Azure provided). We want to join the Virtual Machines of the Hostpool to the Domain controller. For this purpose, we need to update the VNET settings.
Open the VNET, which is used by the domain controller and the host pool, and update the DNS server IP under the “Virtual Network” à “DNS server” as shown below.
Host pools are a collection of one or more identical virtual machines within “Azure Virtual Desktop” tenant environments. Each host pool can contain an application group that users can interact with as they would on a physical desktop.
Ensure that you are in the subscription-linked Azure directory.
- Search for the marketplace in the search bar of azure and search for “windows virtual desktop – provision a host pool” in the marketplace, as shown below.
- Open the “windows virtual desktop-Provision a host pool” as in the below image.

- Enter the details under the Basics Tab as shown below:

- Enter details as per your requirements.
- Add details for the Virtual Machine Settings as per your requirement.
- AD domain joins UPN section: Enter the UPN of the Global Admin user.
For the newly created Azure AD, use the “test1@contoso.onmicrosoft.com” and For the Azure AD linked to the subscription, use the “user1.name@myorg.com”.
- Please ensure the user is added to the Users group in the “domain controller” and assigned below mentioned roles.

- Virtual Network and subnet: Ensure that the VNET and SubNet of the “domain controller” and the “Hostpool” are the same.
- Enter the Windows Virtual Desktop Information as shown below:

- Windows Virtual Desktop Tenant name: Enter the WVD tenant name which we created, “wvdtenant1”.
- UPN, Password:Enter the user who has a “tenant creator” role / “global admin” and “tenant creator” roles.
For the newly created Azure AD, use the “test1@contoso.onmicrosoft.com” and
for the Azure AD linked to the subscription, use the “user1.name@myorg.com”.
This user should be in the Domain Controller and must be assigned the roles below.
- Click on review and create to create the Hostpool.
5. Install IBM Personal Communications:
After creating the host pool, ensure that you are in the subscription-linked directory and navigate to the “virtual machines,” and connect to the virtual machines of the host pool using RDP. Install the “IBM Personal Communications” application.
Note: We need to install the same version of the applications in all the virtual machines of the host pool.
6. Manage app groups for Windows Virtual Desktop:
download and import the Windows Virtual Desktop PowerShell module to use in your PowerShell session.
- Log in with the TenantCreator user account.
For the newly created Azure AD, use the “test1@contoso.onmicrosoft.com” and
For the Azure AD linked to the subscription, use the “user1.name@myorg.com”.
Add-RdsAccount -DeploymentUrl https://rdbroker.wvd.microsoft.com
- Create a Remote Application group:
New-RdsAppGroup -TenantName <specify WVD Tenant Name>-HostPoolName <Specify Hostpool name >-Name <Specify App group name> -ResourceType RemoteApp
(Optional) To verify that the app group was created, you can run the following cmdlet to see a list of all app groups for the host pool.
Get-RdsAppGroup <tenantname> <hostpoolname>
- Run the following command to get the list of Start menu apps on the host pool's virtual machine image. Write down the values for FilePath, IconPath, IconIndex, and other important information for the application that you want to publish.
Get-RdsStartMenuApp <tenantname> <hostpoolname> <appgroupname>
Note: Some applications from the start menu may not be listed using the “Get-RdsStartMenuApp” command.
For example, if the “userpm.exe” of the PCOMM application is not listed, use the below command by explicitly providing the exe path.
New-RdsRemoteApp -TenantName "TenantName" -HostPoolname "Hostpoolname" -AppGroupName "Appname" -Name "Preferences" -FilePath "C:\Program Files\ibm\Personal Communications\userpm.exe" -FriendlyName "Preferences" -IconPath "C:\Program Files\ibm\Personal Communications\userpm.exe"
In the case of “IBM Personal Communications,” you can publish the “AppData”/”Programdata” folder OR only”pcswin.ini”.
(Optional) Run the below command to publish the “pcswin.ini” file.
New-RdsRemoteApp -TenantName <tenantname> -HostPoolname <hostpoolname>
-AppGroupName <remoteappgroupname> -Name "pcswin.ini" -FilePath "C:\Users\Administrator\AppData\Roaming\IBM\Personal Communications\pcswin.ini" -FriendlyName "pcswin.ini" -IconPath "C:\Users\Administrator\AppData\Roaming\IBM\Personal Communications\pcswin.ini"
- (Optional) Run the below command to publish the “AppData” folder.
New-RdsRemoteApp -TenantName <tenantname> -HostPoolname <hostpoolname>
-AppGroupName <remoteappgroupname> -Name "Appdata" -FilePath "C:\Users\Administrator\AppData\Roaming\IBM\Personal Communications " -FriendlyName "Appdata" -IconPath "C:\Users\Administrator\AppData\Roaming\IBM\Personal Communications"
- Run the following command to install the application based on AppAlias. AppAlias becomes visible when you run the output from the previous step.
New-RdsRemoteApp <tenantname> <hostpoolname> <appgroupname> -Name <remoteappname> -AppAlias <appalias>
- To verify that the app was published, run the following command.
Get-RdsRemoteApp <tenantname> <hostpoolname> <appgroupname>
- Run the below command to check the list of users having access to the published RemoteApp group
Get-RdsAppGroupUser -TenantName <tenantname> -HostPoolName <hostpoolname> -AppGroupName <appgroupname>
Example:
- Run the following command to grant users access to the RemoteApp group.
Add-RdsAppGroupUser -TenantName <Tenantname> -HostPoolName <Hostpoolname> -AppGroupName <RemoteAppGrpName> -UserPrincipalName <UPN>
7. Access Published Applications:
Users added to the Remote application group can sign into Windows Virtual Desktop with supported Remote Desktop clients and web clients to see a resource for a session desktop.
Below are the current supported clients:
- Remote Desktop client for Windows 7 and Windows 10: You can install the client for the current user, which does not require admin rights, or your admin can install and configure the client so that all users on the device can access it.
- The client can be launched from the Start menu by searching for Remote Desktop.
- Log in using one of the users who has access to these published Apps. ( “test1@contoso.onmicrosoft.com” OR “name@myorg.com” based on the type of Azure directory used)
- Once you launch, the published apps will look as shown below. You can use the published Apps.

( “test1@contoso.onmicrosoft.com” OR “user1.name@myorg.com” based on the type of Azure directory used)
The published apps will look as shown below.