Hello community,
We’re trying to set up a reverse invoke deployment involving an API Gateway server and a IS, where the authentication method to IS server is with Client Certificates.
All ports are set up with Request Client Certificates authentication option.
IS internal port is successfully connected to API Gateway registration port, but when invoking the API, destination IS is not using the keystore certificate to authenticate. The API Gateway is using Default user.
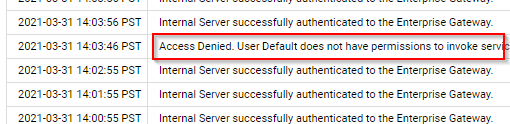
Some of testing I’ve made:
- Direct invocation to the API Gateway with same SSL settings (same keystore) → works fine
- Adding a Username and Password to the Outbound Authentication - Transport policy → makes the request work fine. There is no option of SSL authentication on this policy.
- Adding Default user to allowed ACL → makes the request work fine.
Is there any known limitation to use SSL Authentication with reverse invoke? Am I doing something wrong?
Thank you very much.
#API-Management#API-Gateway#webMethods