Using the EntireX .NET wrapper and EntireX Security from a Intranet ASP.NET solution
In the following I present how my company use the EntireX .NET wrapper classes and EntireX Security from a Intranet ASP.net solution.
I hope some of you will review and discuss our setup. 
I?ve chosen not to send the actual code, since it?s very easy to get lost in less important details of production code. Instead I try to explain the design behind the code, showing slightly simplified code samples to elaborate.
Our task
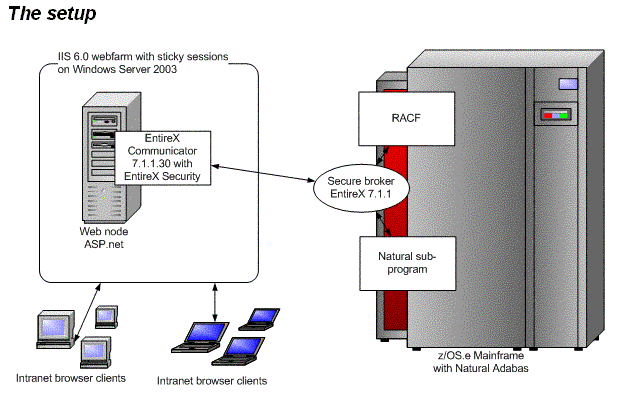
It is our task to substitute all 3270-terminal emulation with web based clients. The business logic will be the same as that of today, programmed in Natural/Adabas running on a z/OS.e mainframe. To expose the existing business logic we produce a service layer, that is numerous natural subprograms with no presentation logic. We use the .NET wrapper to create C# classes making the services available from the .NET framework.
See attached gif-file for overview.
Handling authentication & authorizationFor clarity I?ll describe the first call (logon), subsequent calls and the session end (logoff) separately in the following.
The first call
When the user logs on, a service is called to get user rolls. To make this first call we initialize a broker object like this:
Broker b = new Broker(adr,RACFUsername);
b.Token = HttpContext.Current.Session.SessionID;
That is we assign the broker Token property the unique session ID used to identify the IIS-session.
Since we are using EntireX security we must log on to the broker like this:
b.Logon(RACFPassword);
To avoid subsequent logons during a session, the security token of the first broker instance is cached between calls in the IIS session object, like this:
HttpContext.Current.Session.Add(?Securitytoken?,b.SecurityToken);
In our solution EntireX Security & RACF is used for authentication only. Our natural subprograms perform the authorization. For this we need the user name authorized by RACF.
Under certain configuration settings , the variable *USER will contain the user name if we instantiate the service object like this:
Service s = new Service(b, “RPC/SRV1/CALLNAT”);
s.NaturalLogon = true;
s.UserIDAndPassword(b.UserID,“NOPASSWORD”);
Finally, the class exposing the business logic can now be instantiated, for example:
Example e = new Example( s );
and the business methods can be called, like this:
int result = ex.Calculator( “+”, 10, 15);
Subsequent calls
For subsequent calls within a session we do not log on to the broker. Instead the broker SecurityToken is assigned the cached security token, instantiating the broker like this:
Broker b = new Broker(adr,RACFUsername);
b.Token = HttpContext.Current.Session.SessionID;
b.SecurityToken = (byte)HttpContext.Current.Session[?Securitytoken?];
As for the first call we instantiate the service object like this:
Service s = new Service(b, “RPC/SRV1/CALLNAT”);
s.NaturalLogon = true;
s.UserIDAndPassword(b.UserID,“NOPASSWORD”);
And call the business methods like this:
Example e = new Example( s );
int result = ex.Calculator( “+”, 10, 15);
Note: We?ve set the web session timeout lower than the client-none-activity-timeout of the broker, but still we can get situations where the cached security token expire. In this case we force the session to end and the user to log on once again.
Session end (logoff)
When the session ends, either because the user explicitly chooses to log out, or because the session times out, the session object is cleared hereby clearing the cached security token. However just before this happens (in Session_End of the global.asax or a similar method for explicit logoff) we call the broker log off method:
b.Logoff();
Configuration
On the client site EntireX 7.11 patch 30 has been installed. During the installation the EntireX Security option was selected.
On the mainframe site EntireX 7.11 patch 30 has been installed. In addition EntireX Security, at the same level, has been configured and security has been activated by specifying SECURITY=YES in the Broker attribute file.
Due to the fact that all communication is based on the Callnat model, a Callnat server has been established. I addition to the basic Natural parameter setup, the following parameters has been specified:
? SERVER=ON, to activate Callnat
? LOGONRQ=ON, to ensure that calls can?t be accomplished without a proper logon
? SRVUSER=?*NSC?, to ensure that the Callnat server will run under control of a password specification in Natural Security
As explained earlier, it is vital for the basic programming, that the userid of the client is available to the Natural code in the server application. To make this possible, the parameter ?Logon Option? has been set to ?S? in the ?additional options? for the Natural library in use, hereby the userid of the client is transferred to the *USER field on the Natural site. It is our understanding that this will insure that the client site can?t specify an alternative value of the userid, by a possible misuse of a corresponding ?service? call on the client side. Thus ? this will ensure that the correct userid is specified, that it is not manipulated and that the control of the password is based on settings in RACF alone.
Questions
? Is our use of the .NET Wrapper and EntireX Security as described above sound?
? Is it correct that by setting the parameter ?Logon Option? to ?S? in the ?additional options? for the Natural library in use, we insure that the client site can?t specify an alternative value of the userid, by a possible misuse of a corresponding ?service? call on the client side? And that this will ensure that the correct userid is specified, that it is not manipulated and that the control of the password is based on settings in RACF alone?
? What are the strengths and weaknesses of our solution?
? Where could we choose to do otherwise?
? Does the use of Natural Security to get the authenticated username constitute a performance overhead? And if so, how much?
? Is there any secure alternatives to *USER passing the username to the Natural subprograms?
? According to our SAG-consultant, the security token and token should somehow be used in combination by the broker to identify a broker session. To make it harder to use a stolen security token we assign the sessionid to the token. Testing this feature however it seems that the token value is ignored by the broker. Does the token property have any meaning?
? When do we get a overloaded method Service.UserIDAndPassword taking only userid as parameter? The need for a dummy password which can?t be null or the empty string seems unprofessional.
Best regards,
Michael
#EntireX#Mainframe-Integration#webMethods