Understanding SMB Tail Protocol in QRadar
Introduction
In large Windows ecosystems, log data is distributed across multiple systems—from domain controllers and Exchange servers to IIS and DHCP hosts. Managing and centralizing these logs efficiently is crucial for security monitoring, compliance, and forensic analysis.
In many environments, deploying collection agents or configuring direct log forwarding is not always feasible due to security policies, access restrictions, or performance concerns.
This is where QRadar's SMB Tail Protocol becomes invaluable—providing a secure, agentless, automated way to collect, parse, and normalize logs directly from network-shared folders over SMB.
By continuously monitoring shared folders for new or updated log files, SMB Tail ensures QRadar maintains near real-time visibility into critical events.
What is SMB (Server Message Block)?
SMB is a network file-sharing protocol that allows systems to access files, printers, and other shared resources over a network. It primarily operates over TCP/IP (port 445) and supports authenticated, session-based access to shared directories.
Key SMB Features
- File & directory access: Read/write access to remote shared files.
- Session management: Authenticated and encrypted connections.
- Opportunistic locking & caching: Improves performance in multi-user scenarios.
- Protocol Versions: SMB v1, v2, v3 — each improving speed, reliability, and security.
SMB Version Overview
| SMB Version |
Introduced |
Key Features |
Security Level |
Recommended Use |
| SMB v1 |
1980s / 1990s |
Basic file & printer sharing |
Weak (Deprecated) |
Avoid, legacy systems only |
| SMB v2 |
2006 |
Improved performance, signing support |
Moderate |
Use only if v3 unsupported |
| SMB v3 |
2012 |
Encryption, multichannel, persistent handles |
Strong |
Preferred & recommended |
Understanding SMB Tail Protocol in QRadar
The SMB Tail Protocol in QRadar enables the platform to monitor and analyze SMB-based traffic commonly used in Windows environments for file sharing. In QRadar, the SMB Tail Protocol is used to read log data directly from log files stored on shared network folders.
It functions much like continuously reading a log file and detecting new lines as they appear—forwarding them to QRadar in near real-time. These logs might include:
- User login activity
- File access attempts
- System operations and security events
Unlike Syslog (push-based) or agent-based collection, SMB Tail pulls logs at configurable intervals, offering agentless visibility across distributed environments.
Functional Flow: How SMB Tail Works in QRadar
The SMB Tail Protocol follows a structured process to establish secure connections, read log data, and deliver events for parsing:
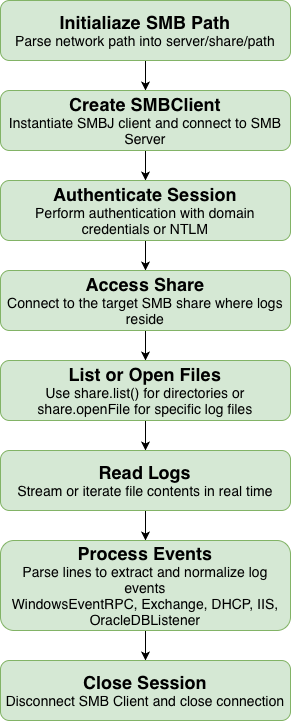
This continuous monitoring ensures QRadar maintains visibility into Windows-based network behaviors — essential for threat detection, audit visibility, and forensic investigations.
How QRadar Uses SMB Tail for Common Microsoft Log Sources?
QRadar supports several Protocols that internally rely on the SMB Tail Protocol to access remote log files:
- Windows EventRPC Protocol
- Retrieves events from files exported from Windows Event Viewer.
- Covers system, security, and application logs.
- Useful when WMI or WinCollect access is not possible (e.g., DMZ or isolated subnets).
- Microsoft Exchange Protocol
- Reads message tracking logs and audit logs generated by Exchange servers.
- Helps security teams detect anomalies such as unexpected mailbox access, failed deliveries, or large outbound mail patterns.
- Windows DHCP Protocol
- Accesses DHCP log files (DhcpSrvLog-*.log) to monitor lease allocations, IP renewals, and MAC-IP bindings.
- Critical for incident correlation - mapping IP addresses to endpoints during investigations.
- Microsoft IIS Protocol
- Monitors IIS web access and error logs for traffic patterns, failed logins, or exploit attempts.
- Enables detection of brute-force or SQL injection attacks on hosted applications.
- Oracle Database Listener Protocol
- Reads listener.log files for database connection attempts and errors.
- Identifies unauthorized login attempts or configuration changes.
Each of these Protocols leverages SMB Tail as a file transport layer, allowing consistent and secure access to shared log files across Windows or mixed environments.
Common Use Cases
- Agentless Collection When deploying agents is restricted due to policy or system limitations, SMB Tail offers a clean, agentless collection alternative.
- Centralized Log Repositories Many organizations aggregate application logs from multiple servers into a central Windows share. SMB Tail can monitor this location directly, reducing configuration complexity.
- Historical Log ImportAnalysts can mount archived log shares temporarily to QRadar and reprocess historical log data for incident reconstruction or audit analysis.
- Forensic InvestigationsBy replaying log files over SMB, security teams can reconstruct event timelines for post-incident analysis.
More Information