Hi, Leandro Takeda here!
There you go one more tutorial related to a challenge I needed to resolve and I didn´t find useful information on the internet!
The POC created to my client consist in receive the user from the Basic HTTP Header and authenticate it against LDAP, later the same user will pass thought an AAA file to authorize it.
Let´s go!
First, we need to create the AAA, and as you should know, you can use it in a Web Service Proxy, Multi-Protocol Gateway, etc, it´s reusable, but I decided to create one per service, because we will limit it by operations.
We need to start creating the AAA. Go to search and type AAA. You can create the AAA from left side menu or even directly from the service rules (Policy tab for Web Service Proxy or Multi-Protocol Gateway Policy option for MPGW).
- We will not change anything in the “Main” tab. I called my AAA as AAA-CustomerService. You can use any standard you would like, but it´s always good to have a standard. J
- In the “Identity extraction”, we will select the option: “HTTP Authentication header”. See below:

- Now, let´s setup your LDAP, you should have the hostname, port and LDAP DN suffix, pay special attention in the LDAP Search attribute field, this is the field that LDAP will return when searching for a user. If you put the wrong value here, your Authorization file will not work. This is the field that we will use returned by the LDAP to validate later against our AAA Authorization file.

- We will not use “Credential mapping” tab, but just fyi, this part is used when you want to map user x to a group, for example.
- In the “Resource extraction” tab, we will set as below. As you see we will extract the operation from the payload, to validate later against the AAA file.
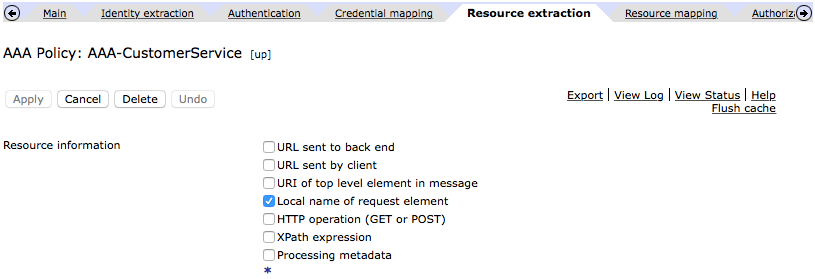
- We will also not use “Resource mapping”, but this work as “Credential mapping”, but for the resource extracted.
- Now, in the “Authorization” tab is where we will upload our AAA file, see below:

And this is the file:
<?xml version="1.0"?>
<aaa:AAAInfo xmlns:dpfunc="http://www.datapower.com/extensions/functions" xmlns:aaa="http://www.datapower.com/AAAInfo">
<aaa:FormatVersion>1</aaa:FormatVersion>
<Filename>local://AAA/AAA-CustomerService.xml</Filename>
<aaa:Summary/>
<aaa:Authorize>
<aaa:InputCredential>user123</aaa:InputCredential>
<aaa:InputResource>CreateRequest|GetRequest</aaa:InputResource>
<aaa:Access>allow</aaa:Access>
</aaa:Authorize>
</aaa:AAAInfo>
- As you see, the file is pretty simple, it contains the user and the operations allowed (CreateRequeset and GetRequest). You can add blocks of <aaa:Authorize> for each user. You can also add or remove operations using the | (pipe) char. There is also an <aaa:Access> tag to allow or deny an user, if you may need, temporarily, without need to remove it from the file.
- To give you more information. You can use the store:///AAAInfo.xml from DataPower filesystem to see more examples. The XSD from this file is also located at store:///AAAInfo.xsd
- And that´s it, test it and let me know in case of any questions. Remember, again, this is just an example that worked for my client, edit it as needed, and hope it helps! ;)
Thanks, and enjoy!
Leandro Takeda
https://www.linkedin.com/in/leandrotakeda/