Hi Alexandre,
I'm not sure what else I can say. Let me try.
To start:
- You have a set of HTTP services and for each one you have an SPN (probably HTTP/
serverx.domain.com@DOMAIN.COM)
- You have a user in AD to represent ISVA (user is "isamkrb")
1. You run the ktpass command to set an SPN for this user and generate a keytab:
ktpass -out isamkrb.keytab -princ HTTP/
isam.domain.com@DOMAIN.COM -mapuser
isamkrb@DOMAIN.COM -mapOp set -pass some_long_password -pType KRB5_NT_PRINCIPAL
You can check SPN with "setspn -UL isamkrb" and "setspn -Q HTTP/
isam.domain.com@DOMAIN.COM"
2. Use AD tools to enable delegation for the isamkrb user - so it can delegate to the SPNs for the target services.
You must set "Trust this user for delegation to specified services only" and "Use any authentication protocol"
3. You set your ISAM system is configured to use AD DNS.
4. You configure Kerberos in ISAM system
Create realm = DOMAIN.COM
Set property kdc = domain_controller.domain.com
Set Default: default_realm = DOMAIN.COM
You should be able to test setup by testing with isamkrb and its password.
5. Import isamkrb.keytab keytab file
You should be able to test by authenticating with the keytab and principal name HTTP/isam.domain.com
6. In Reverse Proxy, configure common Kerberos SSO config:
kerberos-sso-enable = true
kerberos-keytab-file = isamkrb.keytab
kerberos-principal-name = HTTP/
isam.domain.com@DOMAIN.COM6. For each junction where you will use Kerberos SSO add this junction-specific configuration:
[junction:/my_serverx_junction]
kerberos-service-name = HTTP/
serverx.domain.com@DOMAIN.COMThat should do it. I hope it helps you get this working.
Jon.
------------------------------
Jon Harry
Consulting IT Security Specialist
IBM
------------------------------
Original Message:
Sent: Thu March 11, 2021 10:04 AM
From: Alexandre Gammaro
Subject: Doubt with multiple entrys Kerberos
Hi Jon,
As i mentioned in my last note, i opened a support case.
Could you help me there?
I'm stucked on this configuration.
Regards,
------------------------------
Alexandre Gammaro
CyberSecurity Especialist
Triscal - agammaro@triscal.com.br
Original Message:
Sent: Mon March 08, 2021 10:10 AM
From: Jon Harry
Subject: Doubt with multiple entrys Kerberos
That's right !
------------------------------
Jon Harry
Consulting IT Security Specialist
IBM
Original Message:
Sent: Fri March 05, 2021 08:48 AM
From: Alexandre Gammaro
Subject: Doubt with multiple entrys Kerberos
Hi Jon,
How do i do that?
Executing ktpass with these parameters? such as ktpass -out C:\isva.keytab -princ HTTP/isva@AD_DOMAIN.COM
-mapUser AD_DOMAIN\isva -mapOp set -pass XXX -pType KRB5_NT_PRINCIPAL
And i need to do all differents delegations backends on this user "isva", right?
Regards,
------------------------------
Alexandre Gammaro
CyberSecurity Especialist
Triscal - agammaro@triscal.com.br
Original Message:
Sent: Fri March 05, 2021 07:53 AM
From: Jon Harry
Subject: Doubt with multiple entrys Kerberos
Alexandre,
Creating a single principal for ISAM (in a single keytab) and using as the "master" for all of the delegations to different backends should work fine.
So, hoping your answer above means you have it working.
Jon.
------------------------------
Jon Harry
Consulting IT Security Specialist
IBM
Original Message:
Sent: Thu March 04, 2021 01:50 PM
From: Alexandre Gammaro
Subject: Doubt with multiple entrys Kerberos
Hi Jon,
I have more than one backend servers that need to use Kerberos SSO, all of them behind different IIS servers.
I created a user called isva in my Active Directory, i executed ktpass and i delegated the all servers for this user.
Regards,
------------------------------
Alexandre Gammaro
CyberSecurity Especialist
Triscal - agammaro@triscal.com.br
Original Message:
Sent: Thu March 04, 2021 01:26 PM
From: Jon Harry
Subject: Doubt with multiple entrys Kerberos
Hi Alexandre,
What you're trying to do is not supported. You can only specify a single .keytab file and kerberos-principal-name for Kerberos SSO authentication to junctioned servers. This means that the same kerberos principal must be used for generation of delegated tickets across all junctions.
The kerberos-service-name can be specified per junction. This means that each back end service that you delegate to can have a different SPN.
What is your use case? Why do you need to specify so many principals?
Jon.
------------------------------
Jon Harry
Consulting IT Security Specialist
IBM
Original Message:
Sent: Thu March 04, 2021 10:48 AM
From: Alexandre Gammaro
Subject: Doubt with multiple entrys Kerberos
Hi all,
I have a doubt about multiple kerberos entrys in webseal conf.
Can i do that?
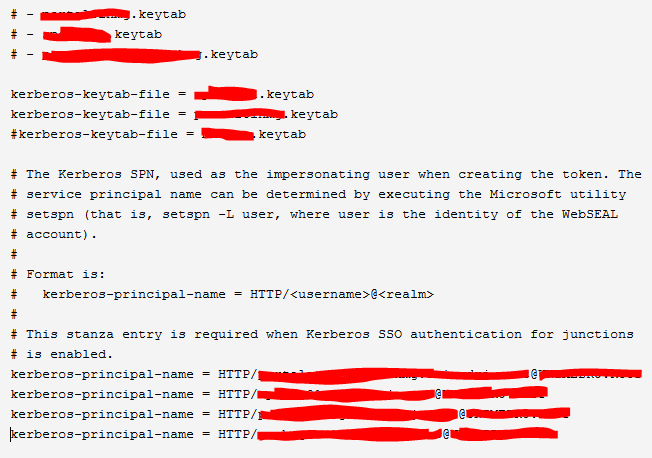
Regards,
------------------------------
Alexandre Gammaro
CyberSecurity Especialist
Triscal - agammaro@triscal.com.br
------------------------------