Hello, I am currently testing IAG with OAuth introspection. My issue seems to be that the JWT that is sent to the resource server, has some claims with numeric values (e.g., exp, nbf, iat) sent as string.
The logged result body from calling introspection endpoint in iag (exp and iat are numbers):
{
"active": true,
"client_id": "client12345id",
"exp": 1646384697,
"iat": 1646381097,
"scope": "scopesrequested",
"token_type": "bearer",
"username": "alice"
}
When I call https://my.iag.app.io/credview the result is (exp and iat are now strings):
{
"AUTHENTICATION_LEVEL": "1",
"AZN_CRED_AUTHNMECH_INFO": "OAuth Introspect Authentication",
"AZN_CRED_AUTHZN_ID": "alice",
"AZN_CRED_AUTH_EPOCH_TIME": "1646388553",
"AZN_CRED_AUTH_METHOD": "oauth-introspect",
"AZN_CRED_BROWSER_INFO": "PostmanRuntime/7.28.4",
"AZN_CRED_IP_FAMILY": "AZN_CRED_IP_FAMILY_AF_INET",
"AZN_CRED_MECH_ID": "oauth-introspect",
"AZN_CRED_NETWORK_ADDRESS_STR": "127.0.0.1",
"AZN_CRED_PRINCIPAL_NAME": "alice",
"AZN_CRED_QOP_INFO": "SSK: TLSV12: 27",
"AZN_CRED_REGISTRY_ID": "alice",
"AZN_CRED_USER_INFO": "alice",
"active": "true",
"client_id": "client12345id",
"exp": "1646384697",
"iat": "1646381097",
"scope": [
"scope1",
"scope2",
"scope3",
"scope4"
],
"tagvalue_login_user_name": "alice",
"tagvalue_session_index": "sessionindex",
"tagvalue_user_session_id": "sessionid",
"token_type": "bearer",
"username": "alice"
}
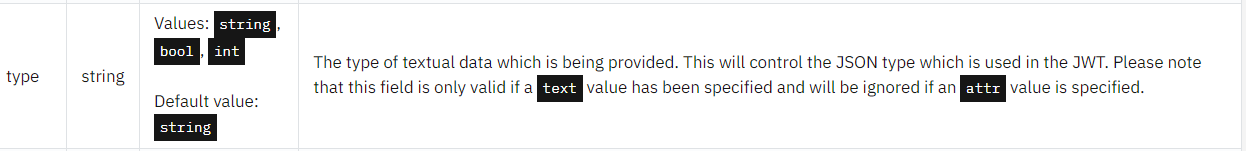
From my understanding, IAG will use the credview information to create the JWT when making a request towards a resource server. Since you can specify the type (e.g., type: int) of claims in resource_servers.identity_headers.jwt.claims, it should then convert the string to a numeric value:
EDIT: It does seem that the type field is valid when attr is specified. So that will have no effect.
version: "%(version)s"
resource_servers:
- path: "%(path)s"
transparent_path: true
connection_type: "tcp"
servers:
- host: "%(host)s"
port: "%(port)s"
identity_headers:
jwt:
certificate: "...cert..."
hdr_name: jwt
claims:
- name: iss
text: 'https://www.issuer.io'
- name: sub
attr: AZN_CRED_PRINCIPAL_NAME
- attr: AZN_*
- name: dest
text: "Default"
- name: source
text: "ext"
- name: groups
text: "[ job ]"
- name: amr
text: "blabla"
- name: acr
attr: AZN_CRED_AUTH_METHOD
- name: name
text: "Fake Login : 123"
- name: aud
text: "urn:liberty"
- name: source
text: "ext"
- name: exp
type: int
attr: exp
- name: iat
type: int
attr: iat
- name: nbf
type: int
attr: iat
- name: jti
text: "sdasdklasjdkla"
However, when the request are received at the resource server. The claims which are specified as int is still strings with double quotes ". What can be the issue here?
EDIT: From what I learn about the type parameter, it seems it will have no effect on attr. So the question then I guess, is there something wrong with the credview?
------------------------------
S Kjemp
------------------------------