Prerequisites
Docker, STIX-Shifter, STIX
Estimated time
30 minutes
Data analysis forms a core part of threat hunting process. Analysts spend majority of the time in arranging and transforming the data collected from EDRs and SIEMS. Kestrel aims to reduce the burden on data analysis by providing simple constructs:
1) Simple constructs to what to look for (GET processes or network-traffic FROM ..)
2) Builds on top of STIX-shifter for normalisation data from multiple data sources
3) Extensible paradigm of APPLY to run purpose-built analytics on collected data.
Kestrel ships with a docker analytics interface, plus 5 examples analytics for threat intelligence enrichment via SANS API, suspicious process scoring, machine learning model testing, geolocation visualization, and data plotting. Use of analytics via APPLY command requires docker installed. Users can build their own analytic as well following template listed in the https://github.com/opencybersecurityalliance/kestrel-analytics/tree/release/template.
Domain-name-lookup is a very simple analytic the provides context enrichment by looking up domain names for IP addresses in the data set.
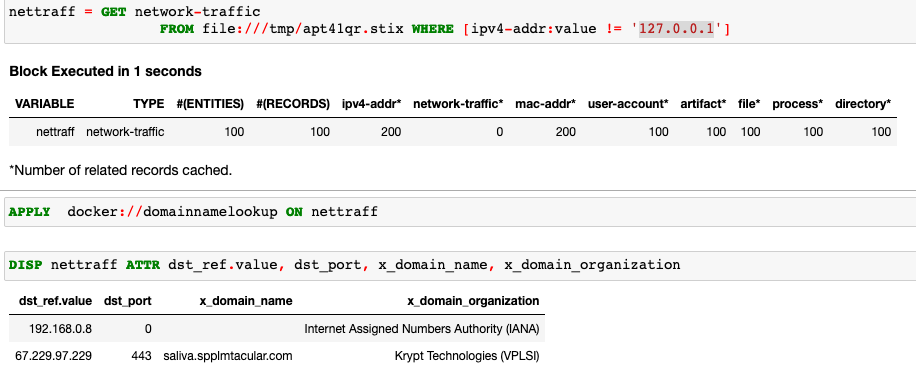
SANS-IP-Enrichment calls the SANS API to perform IP information check. This can be extended to enrich the data with licensed threat intel interfaces.
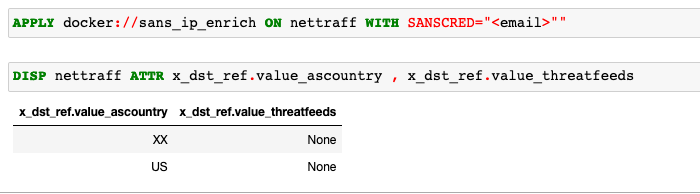
Exfiltration-detection analytic provides insights into likelihood of data exfiltration analysing network traffic data collected from the data sources.
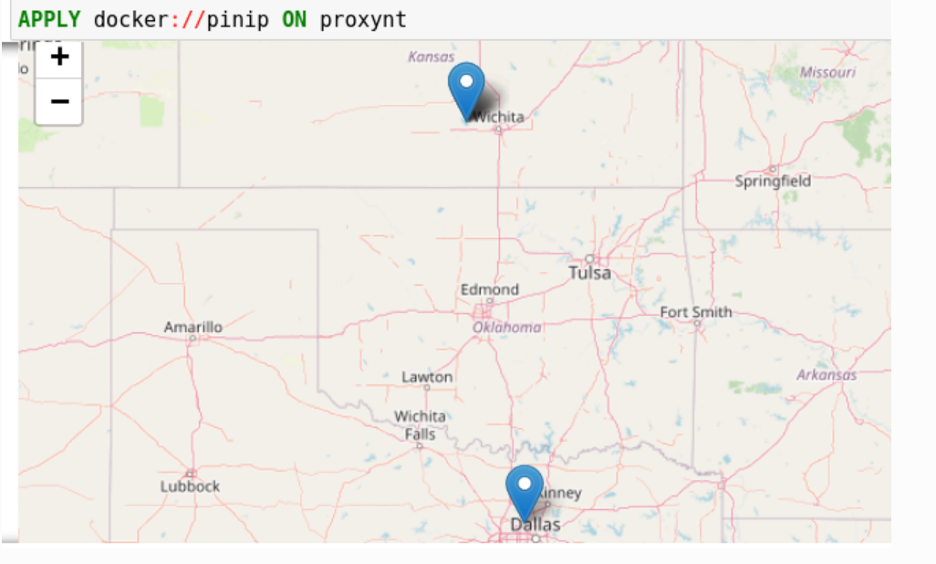
Pinip-on-map analytic provides a way to put IP addresses found in the variable onto a map. This analytics first gets geolocations for all IP addresses in the network traffic using the GeoIP2 API. Then it uses Folium library to pin them on a map. The display object can display the pinned object in a map.
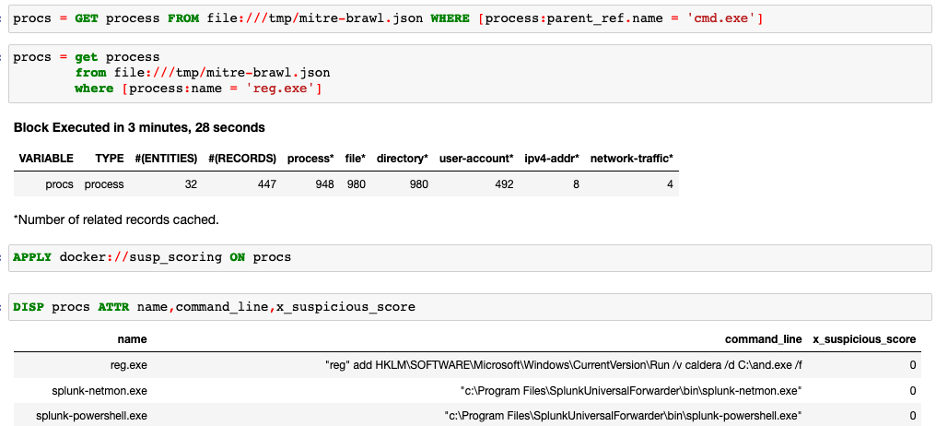
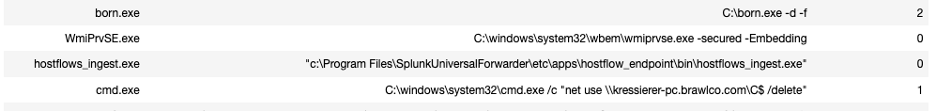
Suspicious-process-scoring is another helpful analytic that looks at the process information in the bundle and scores it based on certain attributes. For example, if the process has established external network connections or launched from a power shell or has obfuscated command-line the score will be higher. It helps in isolating suspicious processes during a threat hunt.


Happy threat hunting !!
For further reading:
https://securityintelligence.com/posts/threat-hunting-guide/
https://kestrel.readthedocs.io/en/latest/tutorial.html#applying-an-analytics