Hi All and first thanks for all your support....
Also proves I certainly need to brush-up on my apparent rusty MQ knowledge.
From all comments etc. I distilled there are probably from an architecture point of 2 basic options:
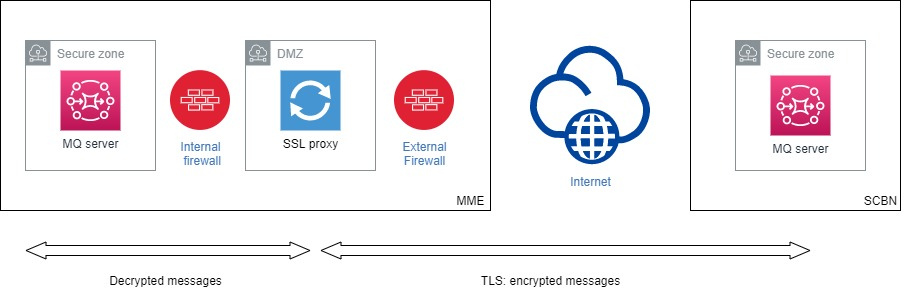
or

Any guidance on which to be preferred and/or why or not feasible??
Again all views, remarks, comments etc. will be most appreciated.
Stay safe and kind regards.
------------------------------
Pierre Mijnsbergen
Solution Architect
IBM
Amsterdam
------------------------------
Original Message:
Sent: Tue March 02, 2021 07:02 AM
From: Pierre Mijnsbergen
Subject: MQ for inter-company communications
I have a customer who intends to use MQ to do direct messaging with its partner over MQ, read going outside their firewall. What would be the objection?? Any best practices?? And if not to be advised, why not??
------------------------------
Pierre Mijnsbergen
Solution Architect
IBM
Amsterdam
------------------------------